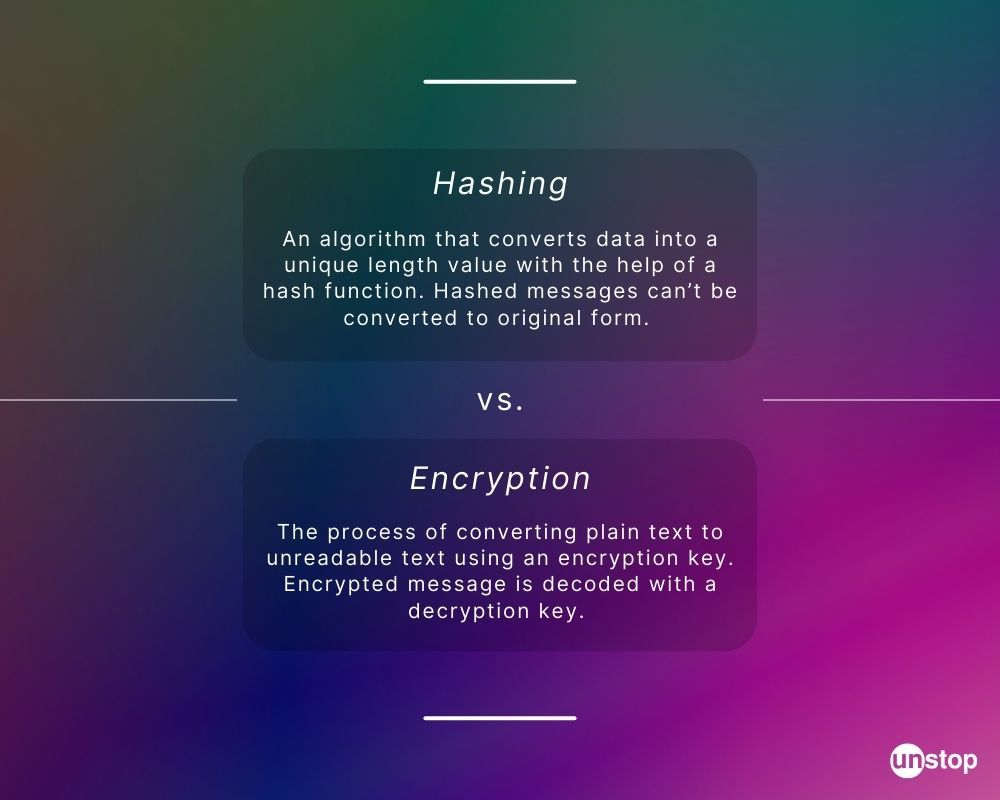
Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.Encryption is a reversible process, but hashing is not. Hashing is way more secure in comparison to encryption. The main purpose of hashing is to check the integrity of data. Whereas the main purpose of encryption is to secure the data by converting it to an unreadable format.
Why is hashing irreversible : Hashing is generally a one-way function, which means that it is easy to convert a message into a hash but very difficult to “reverse hash” a hash value back to its original message as it requires a massive amount of computing power.
What is hash encryption disadvantages
Disadvantages of Hash:
Hash is inefficient when there are many collisions.
Hash collisions are practically not be avoided for large set of possible keys.
Hash does not allow null values.
Hash tables have a limited capacity and will eventually fill up.
Hash tables can be complex to implement.
Can hashed data be decrypted : No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, NOT encrypted. Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation. If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.
In what scenario would you want to use hashing instead of encryption
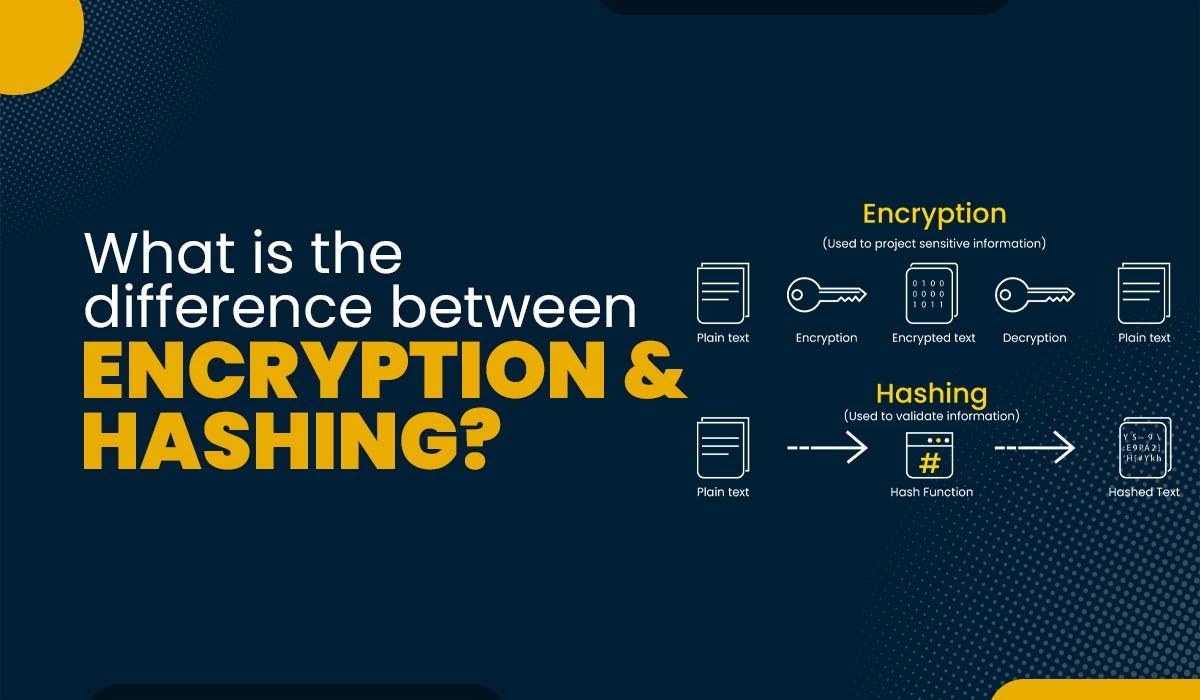
Hashing helps protect the integrity of the information and Encryption is used to secure the data from the reach of third parties. They both look indistinguishable but are dissimilar from each other. Hashing emphasizes the integrity of the information while Encryption focuses on the confidentiality of the data.One of the main challenges of using a hash table is how to deal with collisions, which occur when two or more keys map to the same index in the table.Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again. The hashing algorithm has been found to have a weakness known as collision in which two different messages have the same hashing values. Although the probability of producing such weakness is very small, this collision can be used to deny the usage of the evidence in court of justice.
Is hashed data readable : Hashing is a method of turning readable data into unique but unreadable data — this can be applied to PII to protect the values in a way that they can still be used to link datasets.
What are the disadvantages of hashing passwords : Limitations of Password Hashing
Hackers can try a brute-force attack by running random passwords through the hash function until they finally find a match. This is rather inefficient since the hash algorithms designed for securely storing passwords are designed to be slow, making the entire process tedious and long.
How hard is it to crack a hashed password
Because of the one-way nature of hashing algorithms, the only way to reveal the actual password from a hash is to guess via brute force techniques. Guessing would be an impossible task for a human alone, so attackers user hardware and password cracking software like Hashcat, L0phtcrack, or John The Ripper. Password hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords.Hash tables are widely used data structures that offer efficient data retrieval and storage, but they also have some disadvantages: Collisions: One of the primary disadvantages of hash tables is the potential for collisions. Collisions occur when two different keys hash to the same index in the table.
What are the disadvantages of hashing encryption : Disadvantages of Hash:
Hash is inefficient when there are many collisions.
Hash collisions are practically not be avoided for large set of possible keys.
Hash does not allow null values.
Hash tables have a limited capacity and will eventually fill up.
Antwort Why use hashing instead of encryption? Weitere Antworten – Why hash instead of encrypt
Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.Encryption is a reversible process, but hashing is not. Hashing is way more secure in comparison to encryption. The main purpose of hashing is to check the integrity of data. Whereas the main purpose of encryption is to secure the data by converting it to an unreadable format.
Why is hashing irreversible : Hashing is generally a one-way function, which means that it is easy to convert a message into a hash but very difficult to “reverse hash” a hash value back to its original message as it requires a massive amount of computing power.
What is hash encryption disadvantages
Disadvantages of Hash:
Can hashed data be decrypted : No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, NOT encrypted. Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation.
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.
In what scenario would you want to use hashing instead of encryption
Hashing helps protect the integrity of the information and Encryption is used to secure the data from the reach of third parties. They both look indistinguishable but are dissimilar from each other. Hashing emphasizes the integrity of the information while Encryption focuses on the confidentiality of the data.One of the main challenges of using a hash table is how to deal with collisions, which occur when two or more keys map to the same index in the table.Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
The hashing algorithm has been found to have a weakness known as collision in which two different messages have the same hashing values. Although the probability of producing such weakness is very small, this collision can be used to deny the usage of the evidence in court of justice.
Is hashed data readable : Hashing is a method of turning readable data into unique but unreadable data — this can be applied to PII to protect the values in a way that they can still be used to link datasets.
What are the disadvantages of hashing passwords : Limitations of Password Hashing
Hackers can try a brute-force attack by running random passwords through the hash function until they finally find a match. This is rather inefficient since the hash algorithms designed for securely storing passwords are designed to be slow, making the entire process tedious and long.
How hard is it to crack a hashed password
Because of the one-way nature of hashing algorithms, the only way to reveal the actual password from a hash is to guess via brute force techniques. Guessing would be an impossible task for a human alone, so attackers user hardware and password cracking software like Hashcat, L0phtcrack, or John The Ripper.
Password hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords.Hash tables are widely used data structures that offer efficient data retrieval and storage, but they also have some disadvantages: Collisions: One of the primary disadvantages of hash tables is the potential for collisions. Collisions occur when two different keys hash to the same index in the table.
What are the disadvantages of hashing encryption : Disadvantages of Hash: