Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.the main purpose of existence of Hash code to allow the types to be use in the hash table. Hash table are heavily use in the collections in the dot net framework. Collection are internally store the their value in the hash table. The purpose of the hash table to speed up looking the items in the collection.Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
What are the benefits of hash value : Hashing is commonly used to verify the integrity of data. By generating a hash value (checksum) of a piece of data and comparing it to a previously computed hash value, one can quickly determine if the data has been altered. This is crucial in ensuring the integrity of files during data transmission or storage.
Why is hashCode faster
In Java, the hashCode() method returns a 32-bit number (int) for any object. Comparing two numbers is much faster than comparing two objects using the equals() method, especially if that method considers many fields. If our program compares objects, this is much simpler to do using a hash code.
Why use hash keys : They can be used to offer significant performance improvements within data warehousing scenarios, while also offer robust repeatability and consistency in outputs of surrogate key generation, simplifying data migrations and data processing workloads.
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
What is the main purpose of hash
The primary goal of hashing is to ensure data integrity and validate the original data. Hash functions are intended to be fast and efficient, generating unique hash values for each input. Hashing is irreversible, which means it's computationally impractical to recover the original data from the hash value.Hashing helps to shrink a large data set into a more manageable form, similar to data compression. A good hash typically uses a one-way hashing algorithm, which can prevent the conversion of a hash back into the original key.It is not cryptographically secure, because that's not part of its requirements. How the hashCode is implemented is an implementation detail up to the JVM and can be different for different object types (objects can override the hashCode method and provide an own implementation). Ensuring Uniqueness: The hash code generated by hashCode() is intended to be unique for each distinct object instance. This uniqueness ensures that objects with different properties or states produce distinct hash codes, preventing unintended collisions and maintaining the integrity of the data structure.
What is the point of hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Why is hash useful : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
What is the advantage of hash
Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.Hashing is widely used for secure password storage. Instead of storing passwords in plain text, they're hashed and stored as hash values. This adds an extra layer of security so even if the hash values are compromised, it's computationally infeasible to reverse-engineer the original passwords.
Is the hashCode unique : The hashCode method is designed to return an integer that represents the value of the object. This integer is not unique, but it is generated in a way that helps minimize collisions (two different objects producing the same hash code).
Antwort Why use hashCode? Weitere Antworten – Why use hash code
Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.the main purpose of existence of Hash code to allow the types to be use in the hash table. Hash table are heavily use in the collections in the dot net framework. Collection are internally store the their value in the hash table. The purpose of the hash table to speed up looking the items in the collection.Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
What are the benefits of hash value : Hashing is commonly used to verify the integrity of data. By generating a hash value (checksum) of a piece of data and comparing it to a previously computed hash value, one can quickly determine if the data has been altered. This is crucial in ensuring the integrity of files during data transmission or storage.
Why is hashCode faster
In Java, the hashCode() method returns a 32-bit number (int) for any object. Comparing two numbers is much faster than comparing two objects using the equals() method, especially if that method considers many fields. If our program compares objects, this is much simpler to do using a hash code.
Why use hash keys : They can be used to offer significant performance improvements within data warehousing scenarios, while also offer robust repeatability and consistency in outputs of surrogate key generation, simplifying data migrations and data processing workloads.
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.

Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
What is the main purpose of hash
The primary goal of hashing is to ensure data integrity and validate the original data. Hash functions are intended to be fast and efficient, generating unique hash values for each input. Hashing is irreversible, which means it's computationally impractical to recover the original data from the hash value.Hashing helps to shrink a large data set into a more manageable form, similar to data compression. A good hash typically uses a one-way hashing algorithm, which can prevent the conversion of a hash back into the original key.It is not cryptographically secure, because that's not part of its requirements. How the hashCode is implemented is an implementation detail up to the JVM and can be different for different object types (objects can override the hashCode method and provide an own implementation).
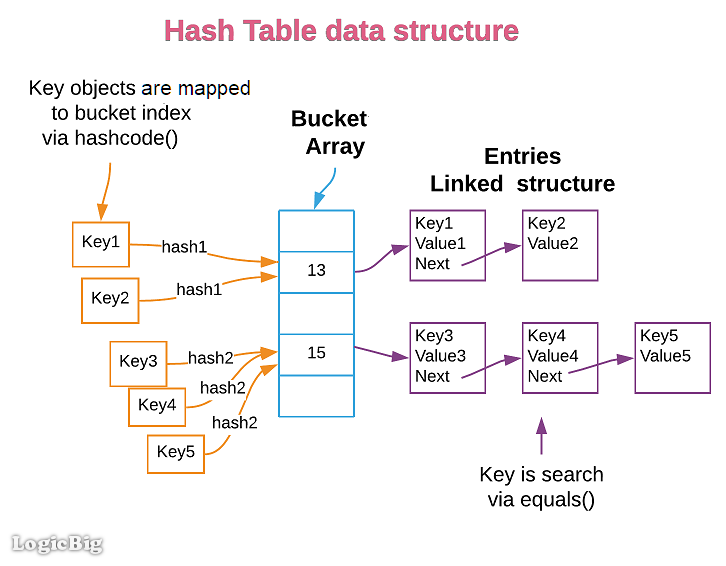
Ensuring Uniqueness: The hash code generated by hashCode() is intended to be unique for each distinct object instance. This uniqueness ensures that objects with different properties or states produce distinct hash codes, preventing unintended collisions and maintaining the integrity of the data structure.
What is the point of hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Why is hash useful : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
What is the advantage of hash
Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.

Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.Hashing is widely used for secure password storage. Instead of storing passwords in plain text, they're hashed and stored as hash values. This adds an extra layer of security so even if the hash values are compromised, it's computationally infeasible to reverse-engineer the original passwords.
Is the hashCode unique : The hashCode method is designed to return an integer that represents the value of the object. This integer is not unique, but it is generated in a way that helps minimize collisions (two different objects producing the same hash code).