Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file. If the contents are modified in any way, the value of the hash will also change significantly.Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
What are the advantages of hashes : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
Why are hash values unique
Are Hash Codes Unique Identifiers A hash code is of a fixed length, so from a mathematical point of view it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the probability of a collision (two distinct files with the same hash value).
What is the most common use of a hash function : Hash Tables: The most common use of hash functions in DSA is in hash tables, which provide an efficient way to store and retrieve data. Data Integrity: Hash functions are used to ensure the integrity of data by generating checksums.
The input data to be hashed is also known as the key. A key can be in just about any format. It could be a string of text, a list of numbers, an image, or even an application file.
Security Vulnerabilities: If a weak or poorly designed hash function is used, it can be vulnerable to various attacks, such as collision attacks, rainbow table attacks, and preimage attacks.
What is one of the advantages of using a hash as an identifier of data
Advantages of Applications of Hashing
Secure: Hashing provides a secure method for storing and retrieving sensitive information, such as passwords, as the original data is transformed into a hash value that is difficult to reverse.Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.Hash functions are used in cryptography and have variable levels of complexity and difficulty. Hash functions are used for cryptocurrency, password security, and message security.
Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
Is hashing good enough : Due to this one-way property, storing a hashed value of a password is a good idea since if their hash is compromised (via a database leak), the attacker would not know the original password (which is the input to the hash function).
Why is hashing not safe : Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible.
Why is hash not secure
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.
This is because the hash function directly maps each data item to its corresponding bucket, without having to compare it with other data items or traverse a list or a tree. This makes hash tables very efficient for searching for data that can be easily hashed, such as strings, numbers, or dates.So the original purpose of the checksum still works to detect link problems. Hashes are more robust and designed to add security to detect mailicious manipulation of data in transit. These are security features and constantly evolving as the threat to data access and manipulation increases.
What are the advantages of hash functions in data structure : Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average.
Antwort Why use hash value? Weitere Antworten – Why do we use hash values
Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file. If the contents are modified in any way, the value of the hash will also change significantly.Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
What are the advantages of hashes : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
Why are hash values unique
Are Hash Codes Unique Identifiers A hash code is of a fixed length, so from a mathematical point of view it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the probability of a collision (two distinct files with the same hash value).
What is the most common use of a hash function : Hash Tables: The most common use of hash functions in DSA is in hash tables, which provide an efficient way to store and retrieve data. Data Integrity: Hash functions are used to ensure the integrity of data by generating checksums.
The input data to be hashed is also known as the key. A key can be in just about any format. It could be a string of text, a list of numbers, an image, or even an application file.

Security Vulnerabilities: If a weak or poorly designed hash function is used, it can be vulnerable to various attacks, such as collision attacks, rainbow table attacks, and preimage attacks.
What is one of the advantages of using a hash as an identifier of data
Advantages of Applications of Hashing
Secure: Hashing provides a secure method for storing and retrieving sensitive information, such as passwords, as the original data is transformed into a hash value that is difficult to reverse.Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.Hash functions are used in cryptography and have variable levels of complexity and difficulty. Hash functions are used for cryptocurrency, password security, and message security.

Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
Is hashing good enough : Due to this one-way property, storing a hashed value of a password is a good idea since if their hash is compromised (via a database leak), the attacker would not know the original password (which is the input to the hash function).
Why is hashing not safe : Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible.
Why is hash not secure
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.
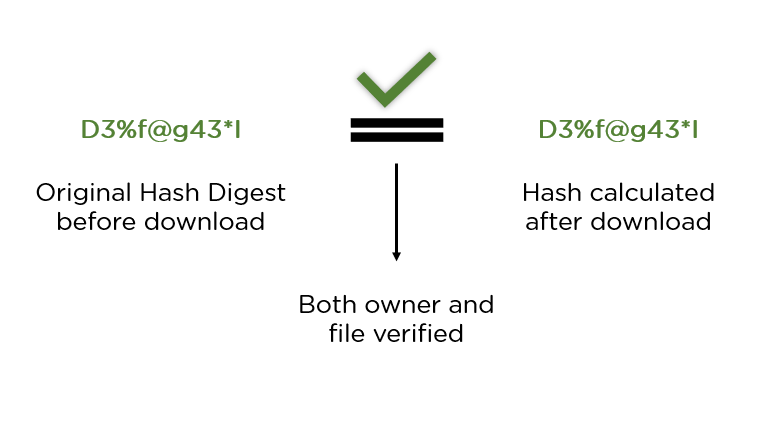
This is because the hash function directly maps each data item to its corresponding bucket, without having to compare it with other data items or traverse a list or a tree. This makes hash tables very efficient for searching for data that can be easily hashed, such as strings, numbers, or dates.So the original purpose of the checksum still works to detect link problems. Hashes are more robust and designed to add security to detect mailicious manipulation of data in transit. These are security features and constantly evolving as the threat to data access and manipulation increases.
What are the advantages of hash functions in data structure : Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average.