Weak security: MD5 produces a fixed-sized 128-bit hash value, which is significantly shorter than modern secure hash functions like SHA-256 or SHA-3. A shorter hash length reduces the resistance against brute-force and collision attacks, increasing the risk of an attacker successfully compromising the data.MD5 was once used for data security and encryption, but these days its primary use is authentication. Because a hacker can create a file that has the exact same hash as an entirely different file, MD5 is not secure in the event that someone tampers with a file.MD5 is obsolete
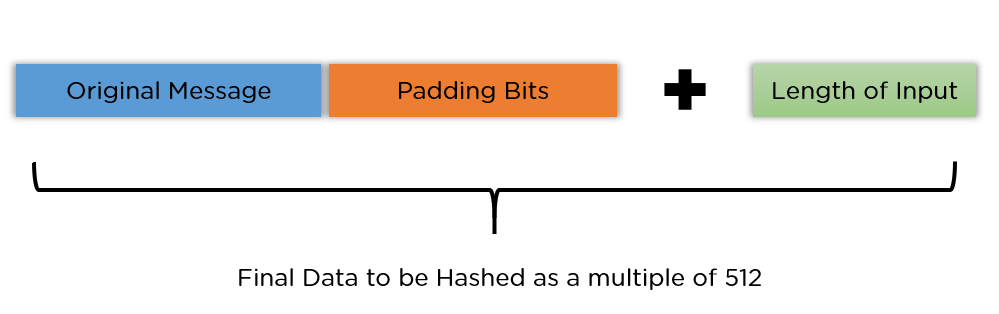
There are many cryptographic hash functions, and only a few are recommended for current use. The others are obsolete. MD5 is extremely old, in tech years. It was introduced in 1992, problems were noticed in 1996 and 2005, and by 2008, it was deemed unusable.
Which is better MD5 or SHA256 : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
When not to use MD5
MD5 should not be used for security purposes or when collision resistance is important.
Is MD5 a weak encryption : A major concern with MD5 is the potential it has for message collisions when message hash codes are inadvertently duplicated. MD5 hash code strings also are limited to 128 bits. This makes them easier to breach than other hash code algorithms that followed.
The final hash value generated by the hash computation is used to determine the message digest [2]. Due to the fact that SHA produces larger message digest size than MD5, SHA is considered more secure than MD5.
GDPR is about telling users exactly what information you collect and exactly what you will do with it. If you declare your MD5 plans, then no. If not, then you're technically in violation.
Is MD5 still being used
MD5 is still being used today as a hash function even though it has been exploited for years.Collision attacks are possible, where cyber criminals can cause MD5 and SHA1 collisions to steal data and cause other problems.Collision attacks are possible, where cyber criminals can cause MD5 and SHA1 collisions to steal data and cause other problems.
A hash, like MD5 or SHA is used to verify passwords because it's hard to invert, that is, to obtain the password from the hash-string. An AES encryption, on the other hand, is invertible, the original message can be obtained if you know the key.
What is the weakest encryption : DES
DES (Data Encryption Standard): is a symmetric key algorithm that uses a 56-bit key. It is considered weak because it can be cracked with a brute-force attack in a reasonable amount of time.
Why not use MD5 for passwords : A major concern with MD5 is the potential it has for message collisions when message hash codes are inadvertently duplicated. MD5 hash code strings also are limited to 128 bits. This makes them easier to breach than other hash code algorithms that followed.
Can MD5 be spoofed
This technique allows an attacker to create two different digital certificates that have the same MD5 hash value, or "fingerprint." By doing so, the attacker can create a "spoofed" certificate that appears to be legitimate and use it to impersonate another entity, such as a website or application.
The MD5 cryptographic algorithm is not reversible i.e. We cannot decrypt a hash value created by the MD5 to get the input back to its original value. So there is no way to decrypt an MD5 password. But, we can use something like brute force hacking, which is extremely resource-intensive, not practical, and unethical.The most common is SHA-256 that produces 256-bit hashes. Secondly, the SHA-2 is more secure than MD5, especially in terms of collision resistance. Therefore, the MD5 isn't recommended to use for high-security purposes.
Why is SHA-1 no longer used : Since 2005, SHA-1 has not been considered secure against well-funded opponents; as of 2010 many organizations have recommended its replacement. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013, and declared that it should be phased out by 2030.
Antwort Why is MD5 not recommended? Weitere Antworten – What is the problem with MD5
Weak security: MD5 produces a fixed-sized 128-bit hash value, which is significantly shorter than modern secure hash functions like SHA-256 or SHA-3. A shorter hash length reduces the resistance against brute-force and collision attacks, increasing the risk of an attacker successfully compromising the data.MD5 was once used for data security and encryption, but these days its primary use is authentication. Because a hacker can create a file that has the exact same hash as an entirely different file, MD5 is not secure in the event that someone tampers with a file.MD5 is obsolete
There are many cryptographic hash functions, and only a few are recommended for current use. The others are obsolete. MD5 is extremely old, in tech years. It was introduced in 1992, problems were noticed in 1996 and 2005, and by 2008, it was deemed unusable.
Which is better MD5 or SHA256 : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
When not to use MD5
MD5 should not be used for security purposes or when collision resistance is important.
Is MD5 a weak encryption : A major concern with MD5 is the potential it has for message collisions when message hash codes are inadvertently duplicated. MD5 hash code strings also are limited to 128 bits. This makes them easier to breach than other hash code algorithms that followed.
The final hash value generated by the hash computation is used to determine the message digest [2]. Due to the fact that SHA produces larger message digest size than MD5, SHA is considered more secure than MD5.
GDPR is about telling users exactly what information you collect and exactly what you will do with it. If you declare your MD5 plans, then no. If not, then you're technically in violation.
Is MD5 still being used
MD5 is still being used today as a hash function even though it has been exploited for years.Collision attacks are possible, where cyber criminals can cause MD5 and SHA1 collisions to steal data and cause other problems.Collision attacks are possible, where cyber criminals can cause MD5 and SHA1 collisions to steal data and cause other problems.

A hash, like MD5 or SHA is used to verify passwords because it's hard to invert, that is, to obtain the password from the hash-string. An AES encryption, on the other hand, is invertible, the original message can be obtained if you know the key.
What is the weakest encryption : DES
DES (Data Encryption Standard): is a symmetric key algorithm that uses a 56-bit key. It is considered weak because it can be cracked with a brute-force attack in a reasonable amount of time.
Why not use MD5 for passwords : A major concern with MD5 is the potential it has for message collisions when message hash codes are inadvertently duplicated. MD5 hash code strings also are limited to 128 bits. This makes them easier to breach than other hash code algorithms that followed.
Can MD5 be spoofed
This technique allows an attacker to create two different digital certificates that have the same MD5 hash value, or "fingerprint." By doing so, the attacker can create a "spoofed" certificate that appears to be legitimate and use it to impersonate another entity, such as a website or application.
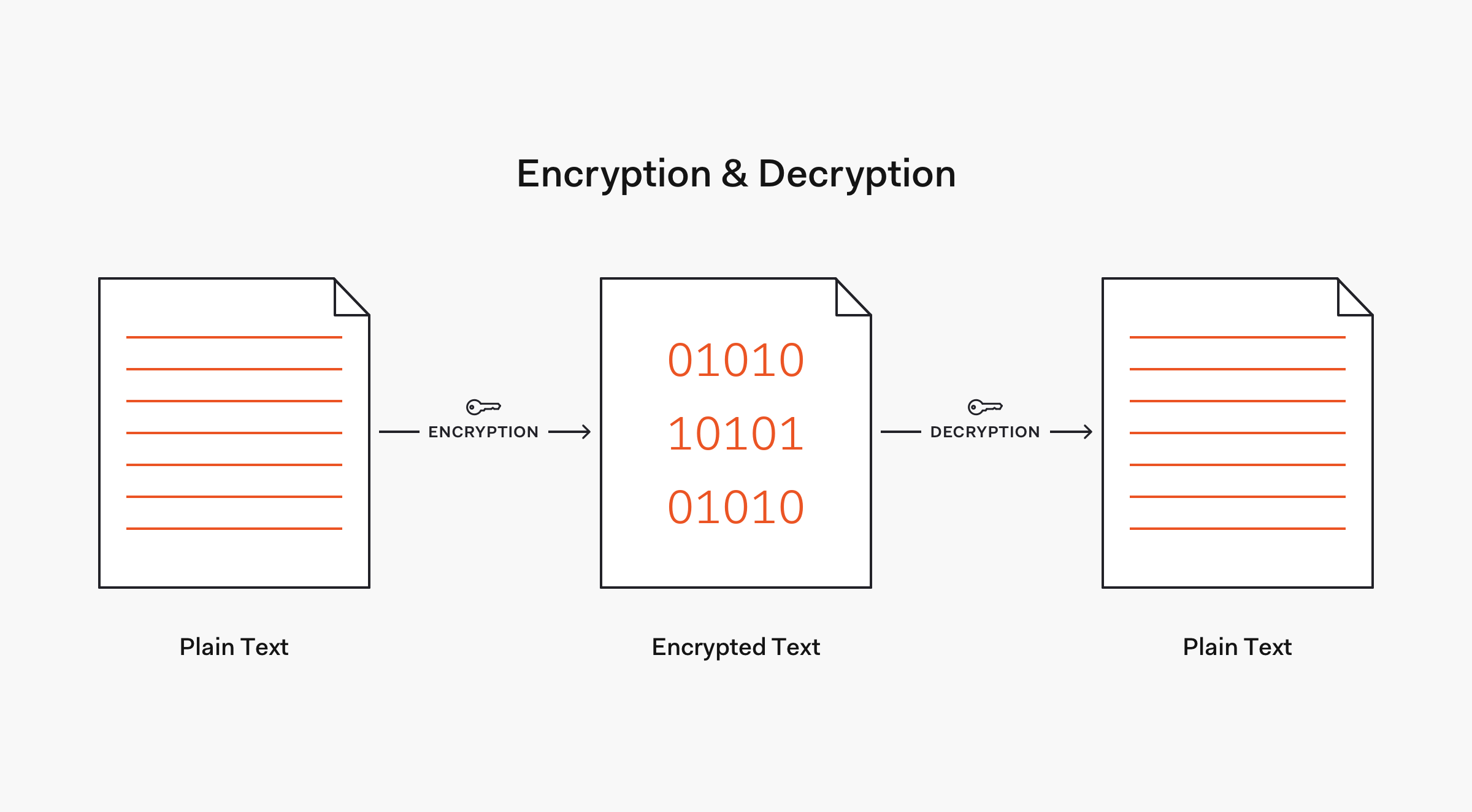
The MD5 cryptographic algorithm is not reversible i.e. We cannot decrypt a hash value created by the MD5 to get the input back to its original value. So there is no way to decrypt an MD5 password. But, we can use something like brute force hacking, which is extremely resource-intensive, not practical, and unethical.The most common is SHA-256 that produces 256-bit hashes. Secondly, the SHA-2 is more secure than MD5, especially in terms of collision resistance. Therefore, the MD5 isn't recommended to use for high-security purposes.
Why is SHA-1 no longer used : Since 2005, SHA-1 has not been considered secure against well-funded opponents; as of 2010 many organizations have recommended its replacement. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013, and declared that it should be phased out by 2030.