Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Disadvantages of Hash:
Hash is inefficient when there are many collisions.
Hash collisions are practically not be avoided for large set of possible keys.
Hash does not allow null values.
Hash tables have a limited capacity and will eventually fill up.
Hash tables can be complex to implement.
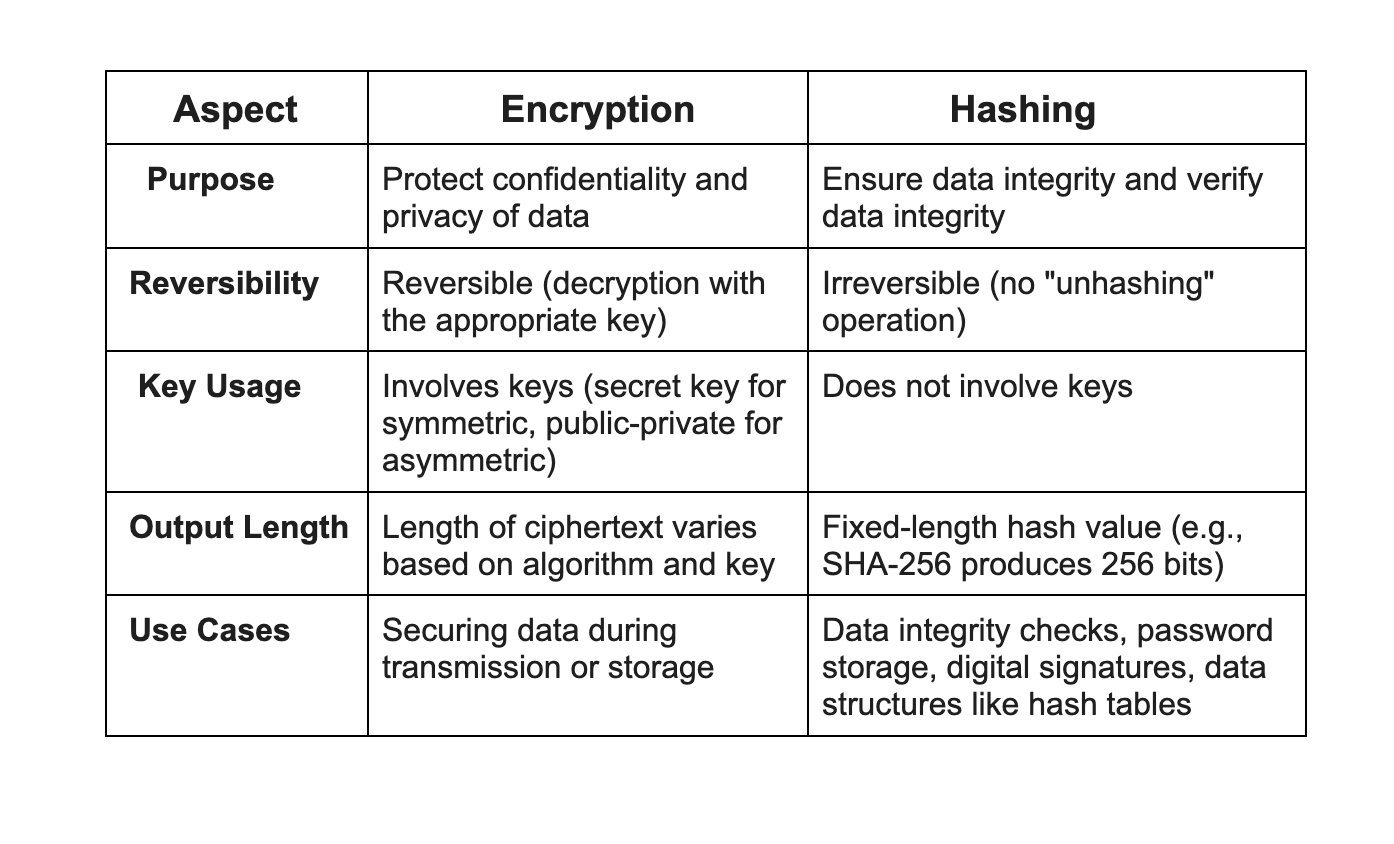
Why hash instead of encrypt : Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.
Is hashing safer than encryption
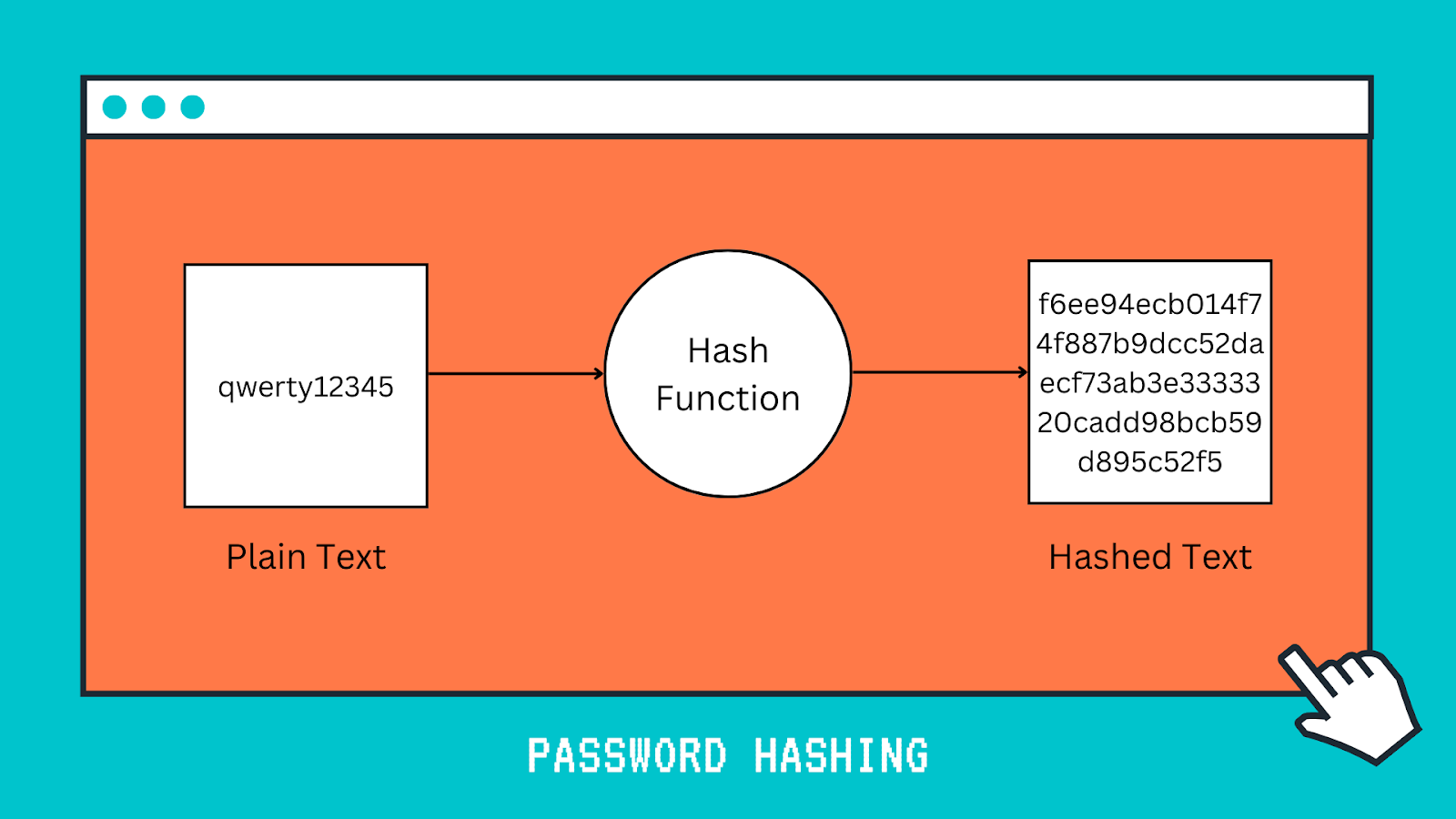
For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).
Is SHA-256 hash safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
Hashes cannot be decrypted because they are not encrypted. Although the output of a hash function often looks similar to the output of an encryption function, hashing is actually an extremely lossy form of data compression. There are a finite number of hash values and an infinite number of hashable plaintext values.
Security Vulnerabilities: If a weak or poorly designed hash function is used, it can be vulnerable to various attacks, such as collision attacks, rainbow table attacks, and preimage attacks.
What are the pros and cons of hashing
The pros for hashing is that it is time efficient and gives an average time complexity of constant time. There are cons as well, like you need to implement collision handling as it is possible that 2 strings might have same hash even when they are different.Encryption techniques protect data in motion. Hashing protects data at rest. Combining these strategies could, in theory, put a strong security boundary around critical assets. But both come with risks and benefits you should know about.You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.
SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Is SHA-256 safer than MD5 : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
Can hashing be broken : Indeed there are some cryptographic hash functions based on number-theoretical problems, such as x2(modN), that can be exponentially broken with a quantum computer. Here, N is the product of two large prime numbers N=p1×p2, and x is a binary representation of the string to be hashed.
Can hashed data be decrypted
No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords. Instead, they just get access to the encrypted unintelligible “hash” created by your password.If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.
How are passwords leaked if they are hashed : Dictionary attack.
Attackers will use software to run popular and predictable passwords through commonly used hashing algorithms. The program will compare the hashed results with the scrambled credentials in the hacker's possession. If there's a match, the hacker can easily deduce the original password.
Antwort Why is hashing not safe? Weitere Antworten – Is hashed data safe
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Disadvantages of Hash:
Why hash instead of encrypt : Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.
Is hashing safer than encryption
For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).
Is SHA-256 hash safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
Hashes cannot be decrypted because they are not encrypted. Although the output of a hash function often looks similar to the output of an encryption function, hashing is actually an extremely lossy form of data compression. There are a finite number of hash values and an infinite number of hashable plaintext values.
:max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png)
Security Vulnerabilities: If a weak or poorly designed hash function is used, it can be vulnerable to various attacks, such as collision attacks, rainbow table attacks, and preimage attacks.
What are the pros and cons of hashing
The pros for hashing is that it is time efficient and gives an average time complexity of constant time. There are cons as well, like you need to implement collision handling as it is possible that 2 strings might have same hash even when they are different.Encryption techniques protect data in motion. Hashing protects data at rest. Combining these strategies could, in theory, put a strong security boundary around critical assets. But both come with risks and benefits you should know about.You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.
SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Is SHA-256 safer than MD5 : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
Can hashing be broken : Indeed there are some cryptographic hash functions based on number-theoretical problems, such as x2(modN), that can be exponentially broken with a quantum computer. Here, N is the product of two large prime numbers N=p1×p2, and x is a binary representation of the string to be hashed.
Can hashed data be decrypted
No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords. Instead, they just get access to the encrypted unintelligible “hash” created by your password.If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.
How are passwords leaked if they are hashed : Dictionary attack.
Attackers will use software to run popular and predictable passwords through commonly used hashing algorithms. The program will compare the hashed results with the scrambled credentials in the hacker's possession. If there's a match, the hacker can easily deduce the original password.