Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Data integrity: Hash functions are useful for ensuring the integrity of data, as any changes to the data will result in a different hash value. This property makes hash functions a valuable tool for detecting data tampering or corruption.
Why is hash function needed in cryptography : Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.
What is the importance of hashing
In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
Why is hash value important : A hash value guarantees authenticity thanks to four particular characteristics: It is deterministic, meaning that a specific input (or file) wil always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file.
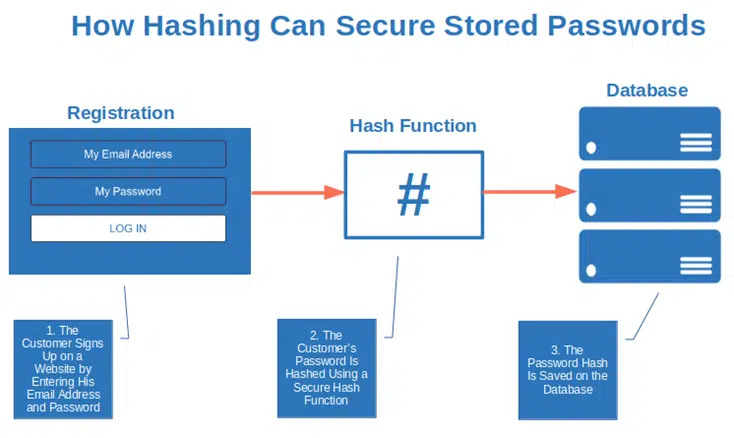
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.
Hash indexes help to ensure fast performance by converting inputs into an array of "buckets." Each bucket contains the same number of records as the others in the table, ensuring that all the rows can map to one bucket regardless of the number of values there are for a particular column.
How important is the hash function
Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hashing is an algorithm that calculates a fixed-size bit string value from a file. A file basically contains blocks of data. Hashing transforms this data into a far shorter fixed-length value or key which represents the original string.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
What are the advantages of hashing : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
Why is hashing important in database : So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What is the main advantage of hashing
What are the benefits of Hashing One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.
The primary goal of hashing is to ensure data integrity and validate the original data. Hash functions are intended to be fast and efficient, generating unique hash values for each input. Hashing is irreversible, which means it's computationally impractical to recover the original data from the hash value.Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.
What is a hash and why is it important : Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.
Antwort Why is hashing important to secure data? Weitere Antworten – Why is hashing used in security
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Data integrity: Hash functions are useful for ensuring the integrity of data, as any changes to the data will result in a different hash value. This property makes hash functions a valuable tool for detecting data tampering or corruption.
Why is hash function needed in cryptography : Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.
What is the importance of hashing
In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
Why is hash value important : A hash value guarantees authenticity thanks to four particular characteristics: It is deterministic, meaning that a specific input (or file) wil always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file.
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.

Hash indexes help to ensure fast performance by converting inputs into an array of "buckets." Each bucket contains the same number of records as the others in the table, ensuring that all the rows can map to one bucket regardless of the number of values there are for a particular column.
How important is the hash function
Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hashing is an algorithm that calculates a fixed-size bit string value from a file. A file basically contains blocks of data. Hashing transforms this data into a far shorter fixed-length value or key which represents the original string.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.

Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
What are the advantages of hashing : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
Why is hashing important in database : So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What is the main advantage of hashing
What are the benefits of Hashing One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.
The primary goal of hashing is to ensure data integrity and validate the original data. Hash functions are intended to be fast and efficient, generating unique hash values for each input. Hashing is irreversible, which means it's computationally impractical to recover the original data from the hash value.Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.
What is a hash and why is it important : Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.