Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value. Hash values are also useful for verifying the integrity of data sent through insecure channels.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.To ensure the transferred file is not corrupted, a user can compare the hash value of both files. If they are the same, then the transferred file is an identical copy.
What is the purpose of hashing a file : To verify that a file has not been corrupted or tampered with. By comparing the hash of a downloaded file with the original hash, a user can be sure that the file is exactly as it should be.
Why are hash values unique
Are Hash Codes Unique Identifiers A hash code is of a fixed length, so from a mathematical point of view it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the probability of a collision (two distinct files with the same hash value).
How is hashing used in real life : Image processing: Hashing is used in image processing applications, such as perceptual hashing, to detect and prevent image duplicates and modifications. File comparison: Hashing is used in file comparison algorithms, such as the MD5 and SHA-1 hash functions, to compare and verify the integrity of files.
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data. So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What are the benefits of hashing in data structure
In data structure, hashing helps in narrowing down search and find number within seconds. Hashing is the process of converting input data of any size into a fixed-size value, usually for the purpose of fast data retrieval.A one-way method of hiding sensitive data. Using a hashing algorithm, hashing turns a plaintext into a unique hash digest that cannot be reverted to the original plaintext, without considerable effort.For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key). Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.
Why are hashes so secure : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why are hashes secure : Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.
What is a hash value in cyber security
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file. Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
What causes a hash value to change : Hash values provide digital files with a unique identifier that corresponds to its contents. If the contents change, the file's hashtag will change as well, indicating that the file is not the same as it was before.
Antwort Why is hash value important? Weitere Antworten – What is the purpose of hash value
Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value. Hash values are also useful for verifying the integrity of data sent through insecure channels.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.To ensure the transferred file is not corrupted, a user can compare the hash value of both files. If they are the same, then the transferred file is an identical copy.
What is the purpose of hashing a file : To verify that a file has not been corrupted or tampered with. By comparing the hash of a downloaded file with the original hash, a user can be sure that the file is exactly as it should be.
Why are hash values unique
Are Hash Codes Unique Identifiers A hash code is of a fixed length, so from a mathematical point of view it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the probability of a collision (two distinct files with the same hash value).
How is hashing used in real life : Image processing: Hashing is used in image processing applications, such as perceptual hashing, to detect and prevent image duplicates and modifications. File comparison: Hashing is used in file comparison algorithms, such as the MD5 and SHA-1 hash functions, to compare and verify the integrity of files.
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.

So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What are the benefits of hashing in data structure
In data structure, hashing helps in narrowing down search and find number within seconds. Hashing is the process of converting input data of any size into a fixed-size value, usually for the purpose of fast data retrieval.A one-way method of hiding sensitive data. Using a hashing algorithm, hashing turns a plaintext into a unique hash digest that cannot be reverted to the original plaintext, without considerable effort.For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).
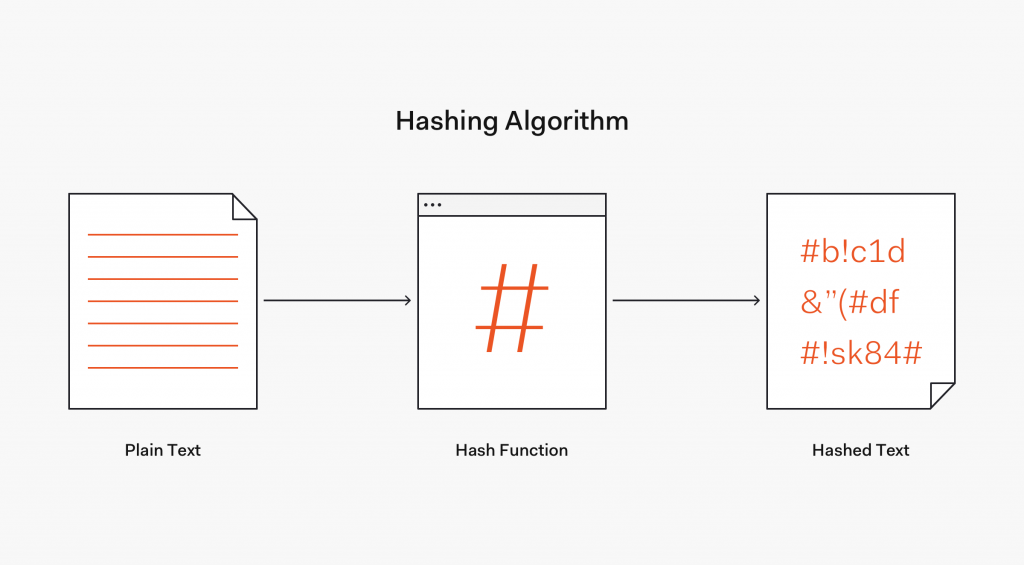
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.
Why are hashes so secure : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why are hashes secure : Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.
What is a hash value in cyber security
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
What causes a hash value to change : Hash values provide digital files with a unique identifier that corresponds to its contents. If the contents change, the file's hashtag will change as well, indicating that the file is not the same as it was before.