The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.Medium- and short-chain-3-hydroxyacyl-coenzyme A (CoA) dehydrogenase (SCHAD) (gene name, hadh) catalyze the third reaction of the mitochondrial β-oxidation cascade, the oxidation of 3-hydroxyacyl-CoA to 3-ketoacyl-CoA, for medium- and short-chain fatty acids.Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
What is the function of hashing : A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
What is the point of hashes
Hashing is a function used to map data to a fixed-length value. Businesses use hashing in authentication systems and to validate different types of data, such as files and documents. Understanding what hashing is and how it's used is important because it can help to prevent data breaches and protect stored information.
What is the advantage of hashing : The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.
The hash symbol represents a command for the preprocessor, and is known as a macro. It literally tells your computer to take the code in the included file and place it where the #include statement is. Hashing has a large number of applications in cybersecurity, centering around the ability to verify that data is legitimate. With a secure hashing algorithm, one could verify that a downloaded file matched what was expected. In fact, many projects provide hashes alongside their downloads.
Why do we use hash code
Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.What are the benefits of Hashing One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications. Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is hashing preferred : Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.
Why use hashing instead of encryption : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why do we hash before encryption
To fit the keys to the encryption key length. Most passwords are going to be either longer or shorter than the key space of the encryption function. By hashing your password, the exact key length will be exactly the size of the input key of your encryption function. Python programmers use hashing to transform input data into a fixed-size value. This value represents the data uniquely, and the hashing technique makes it easy to transmit and store various forms of data securely. Hashing protects data from unauthorized access and tampering.This is because the hash function directly maps each data item to its corresponding bucket, without having to compare it with other data items or traverse a list or a tree. This makes hash tables very efficient for searching for data that can be easily hashed, such as strings, numbers, or dates.
How is hashing used in real life : Image processing: Hashing is used in image processing applications, such as perceptual hashing, to detect and prevent image duplicates and modifications. File comparison: Hashing is used in file comparison algorithms, such as the MD5 and SHA-1 hash functions, to compare and verify the integrity of files.
Antwort Why is hash used? Weitere Antworten – Why do we use hash
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.Medium- and short-chain-3-hydroxyacyl-coenzyme A (CoA) dehydrogenase (SCHAD) (gene name, hadh) catalyze the third reaction of the mitochondrial β-oxidation cascade, the oxidation of 3-hydroxyacyl-CoA to 3-ketoacyl-CoA, for medium- and short-chain fatty acids.Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
What is the function of hashing : A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
What is the point of hashes
Hashing is a function used to map data to a fixed-length value. Businesses use hashing in authentication systems and to validate different types of data, such as files and documents. Understanding what hashing is and how it's used is important because it can help to prevent data breaches and protect stored information.
What is the advantage of hashing : The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.
The hash symbol represents a command for the preprocessor, and is known as a macro. It literally tells your computer to take the code in the included file and place it where the #include statement is.
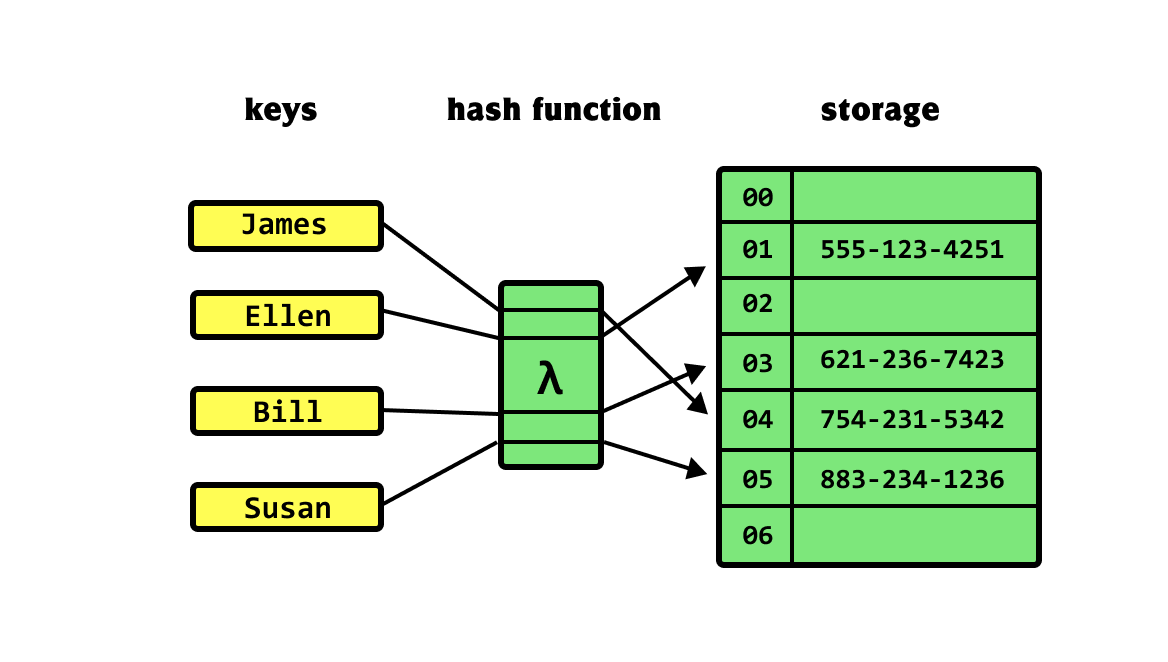
Hashing has a large number of applications in cybersecurity, centering around the ability to verify that data is legitimate. With a secure hashing algorithm, one could verify that a downloaded file matched what was expected. In fact, many projects provide hashes alongside their downloads.
Why do we use hash code
Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.What are the benefits of Hashing One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.

Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is hashing preferred : Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.
Why use hashing instead of encryption : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why do we hash before encryption
To fit the keys to the encryption key length. Most passwords are going to be either longer or shorter than the key space of the encryption function. By hashing your password, the exact key length will be exactly the size of the input key of your encryption function.

Python programmers use hashing to transform input data into a fixed-size value. This value represents the data uniquely, and the hashing technique makes it easy to transmit and store various forms of data securely. Hashing protects data from unauthorized access and tampering.This is because the hash function directly maps each data item to its corresponding bucket, without having to compare it with other data items or traverse a list or a tree. This makes hash tables very efficient for searching for data that can be easily hashed, such as strings, numbers, or dates.
How is hashing used in real life : Image processing: Hashing is used in image processing applications, such as perceptual hashing, to detect and prevent image duplicates and modifications. File comparison: Hashing is used in file comparison algorithms, such as the MD5 and SHA-1 hash functions, to compare and verify the integrity of files.