In data structures, a hash function is used to calculate the hash value of a key, which is then used to store and retrieve the corresponding data. Hash functions are often used in conjunction with an array, where the hash value is used as an index in the array.Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient. Most Hash table implementation can automatically resize itself.
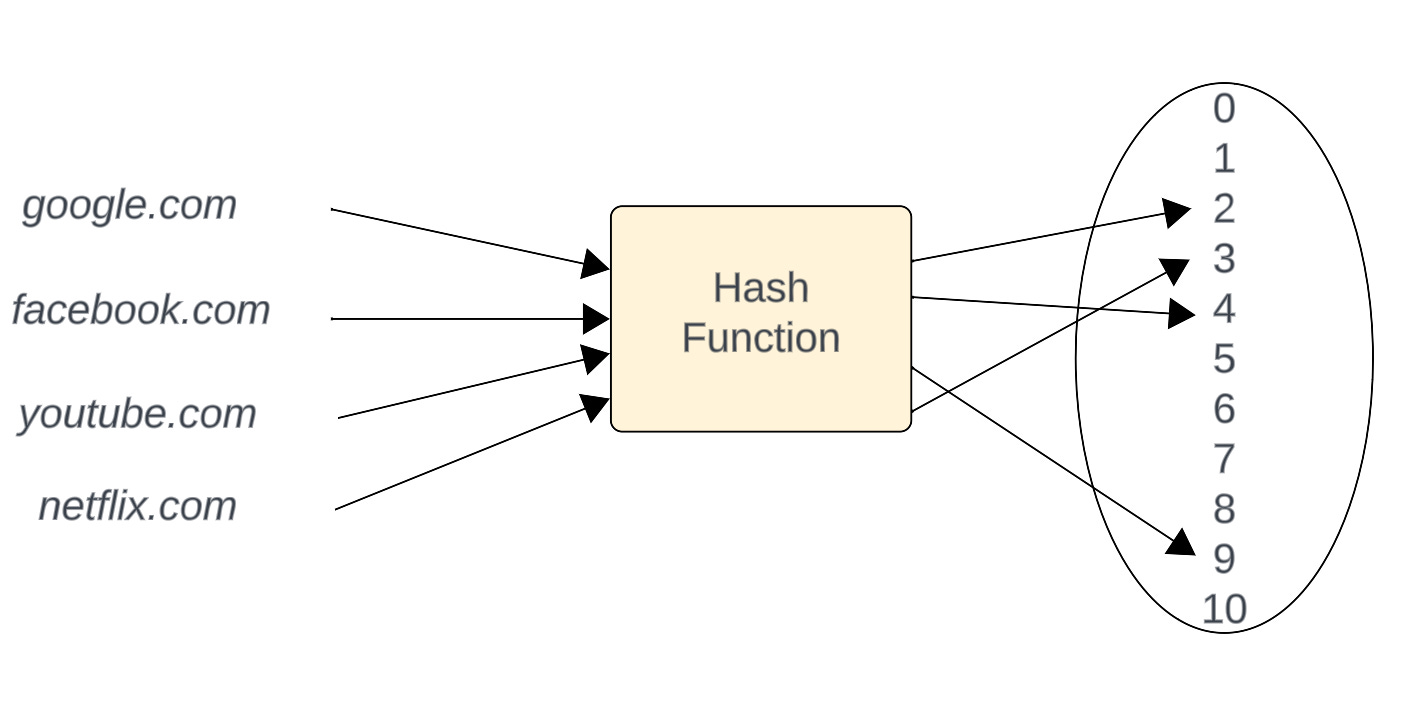
What is the hashing technique : Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use for hashing is the implementation of hash tables.
What are two functions of hashing
Some common use cases for hashing functions include the following ones:
Detecting duplicated records.
Locating points that are near each other.
Verifying message integrity.
Verifying passwords.
Which hashing technique is best : SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Unlike standard encryption, hashing is always used for one-way encryption, and hashed values are very difficult to decode.
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.
Why might we prefer a hash table
1 Benefits of hash tables
This means that you can store and retrieve data in constant time, regardless of the size of the data set. Second, they are flexible and dynamic. You can use any data type as a key or a value, and you can resize the hash table as needed. Third, they are versatile and adaptable.Arrays have low scalability, which means they cannot grow or shrink easily and may cause memory wastage or overflow. Hash tables have high scalability, which means they can adjust to the changing number of elements and optimize the space utilization.One, hashing is a one-way function. It can be used on any input data to generate a hash value. But, applying a hash function to a hash value will not reveal the input data. Second, hashing always produces a fixed-length hash value, irrespective of the length/ size of the input.
Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
Why is hashing irreversible : It would be impossible to figure out the original data of the function with just the resulting hash – as not much of that data is left – the only workable method is to brute force every possible combination. If we could reverse a hash, we would be able to compress data of any size into a mere few bytes of data.
What is hashing and why it is used : Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
How is hashing used in real life
Image processing: Hashing is used in image processing applications, such as perceptual hashing, to detect and prevent image duplicates and modifications. File comparison: Hashing is used in file comparison algorithms, such as the MD5 and SHA-1 hash functions, to compare and verify the integrity of files.
We then compare the two algorithms and find that hashing is faster, but that sorting requires less disk storage. We also compare disk-based with in-memory search, and surprisingly find that there is little or no time over- head associated with disk-based search.This is because the hash function directly maps each data item to its corresponding bucket, without having to compare it with other data items or traverse a list or a tree. This makes hash tables very efficient for searching for data that can be easily hashed, such as strings, numbers, or dates.
What is a hash and why is it important : Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.
Antwort Why do we use hashing in data structure? Weitere Antworten – What is the function of hashing in data structure
In data structures, a hash function is used to calculate the hash value of a key, which is then used to store and retrieve the corresponding data. Hash functions are often used in conjunction with an array, where the hash value is used as an index in the array.Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient. Most Hash table implementation can automatically resize itself.
What is the hashing technique : Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use for hashing is the implementation of hash tables.
What are two functions of hashing
Some common use cases for hashing functions include the following ones:
Which hashing technique is best : SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Unlike standard encryption, hashing is always used for one-way encryption, and hashed values are very difficult to decode.
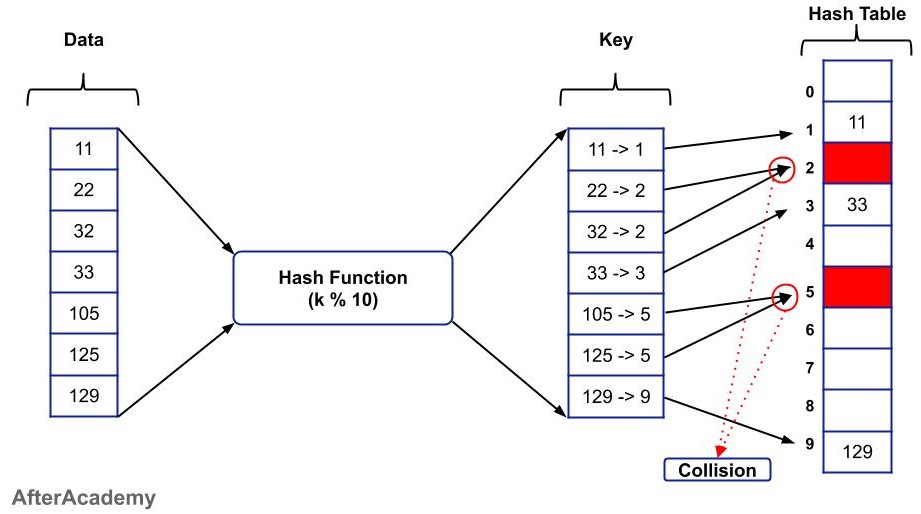
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.
Why might we prefer a hash table
1 Benefits of hash tables
This means that you can store and retrieve data in constant time, regardless of the size of the data set. Second, they are flexible and dynamic. You can use any data type as a key or a value, and you can resize the hash table as needed. Third, they are versatile and adaptable.Arrays have low scalability, which means they cannot grow or shrink easily and may cause memory wastage or overflow. Hash tables have high scalability, which means they can adjust to the changing number of elements and optimize the space utilization.One, hashing is a one-way function. It can be used on any input data to generate a hash value. But, applying a hash function to a hash value will not reveal the input data. Second, hashing always produces a fixed-length hash value, irrespective of the length/ size of the input.

Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
Why is hashing irreversible : It would be impossible to figure out the original data of the function with just the resulting hash – as not much of that data is left – the only workable method is to brute force every possible combination. If we could reverse a hash, we would be able to compress data of any size into a mere few bytes of data.
What is hashing and why it is used : Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
How is hashing used in real life
Image processing: Hashing is used in image processing applications, such as perceptual hashing, to detect and prevent image duplicates and modifications. File comparison: Hashing is used in file comparison algorithms, such as the MD5 and SHA-1 hash functions, to compare and verify the integrity of files.
We then compare the two algorithms and find that hashing is faster, but that sorting requires less disk storage. We also compare disk-based with in-memory search, and surprisingly find that there is little or no time over- head associated with disk-based search.This is because the hash function directly maps each data item to its corresponding bucket, without having to compare it with other data items or traverse a list or a tree. This makes hash tables very efficient for searching for data that can be easily hashed, such as strings, numbers, or dates.
What is a hash and why is it important : Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.