The cryptographic hash function in Blockchain is a way to secure the message block and is used to connect the blocks in a chain. Briefly, In the blockchain, each block contains its own block hash and a hash of its previous block. It helps them to form a cryptographically secured linear chain of blocks.Blockchain Technology
SHA-256 enables the proof-of-work (PoW) consensus algorithm on the Bitcoin blockchain. The cryptographic hash function is used to verify transactions on the blockchain protocol.A cryptographic hash is used to validate the integrity of a block of data. You can pass data of arbitrary size into a hashing algorithm and it will return a (large) number called a Message Digest (MD) that is unique to that data. You can think of a Message Digest as a cryptographic checksum or fingerprint of the data.
What hashing algorithm does Bitcoin use : SHA-256 function
The SHA-256 function that Bitcoin uses is short for “Secure Hash Algorithm” and was designed by the United States National Security Agency (NSA) and includes SHA-1, SHA-2 (a family within a family that includes SHA-224, SHA-256, SHA-384, and SHA-512), and SHA-3 (SHA3-224, SHA3-256, SHA3-384, and SHA3-512).
What is the main purpose of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
Why do people use hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
SHA-256 can help secure SSL/TLS (Transport Layer Security) certificates by creating a digital signature your device can verify. For example, when a server presents its TLS certificate to clients such as web browsers, the client can then use the corresponding public key to decrypt and verify the signature. Furthermore, Bitcoin transactions are digitally signed via the private keys of senders to prove ownership before bitcoins are sent. That is, the transaction data is hashed using SHA-256, and then the hash is signed using the sender's private key with the aforementioned ECDSA.
Why is hashing used in cyber security
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.What is Target Hash A target hash is a number that must be greater than or equal to a hashed block header for a new block to be awarded. The target hash is used to determine the difficulty of input and can be adjusted to ensure efficient processing of the blocks. In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
Why use hashing instead of encryption : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is SHA-256 so popular : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
What is the function of SHA hashing
SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions. The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.The double hashing is invented by Ferguson and Schneier in their book Practical Cryptography to countermeasure against length extension attacks. As a side note, double-hashing doesn't prevent collision attacks since any collision SHA256(x)=SHA256(y) is also a collision for SHA256(SHA256(x))=SHA256(SHA256(y)).
Why do we need hashing : Hashing enables efficient data retrieval in hash tables, especially when dealing with large data sets. It uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map.
Antwort Why do we use hashing in blockchain? Weitere Antworten – Why is hashing used in blockchain
The cryptographic hash function in Blockchain is a way to secure the message block and is used to connect the blocks in a chain. Briefly, In the blockchain, each block contains its own block hash and a hash of its previous block. It helps them to form a cryptographically secured linear chain of blocks.Blockchain Technology
SHA-256 enables the proof-of-work (PoW) consensus algorithm on the Bitcoin blockchain. The cryptographic hash function is used to verify transactions on the blockchain protocol.A cryptographic hash is used to validate the integrity of a block of data. You can pass data of arbitrary size into a hashing algorithm and it will return a (large) number called a Message Digest (MD) that is unique to that data. You can think of a Message Digest as a cryptographic checksum or fingerprint of the data.

What hashing algorithm does Bitcoin use : SHA-256 function
The SHA-256 function that Bitcoin uses is short for “Secure Hash Algorithm” and was designed by the United States National Security Agency (NSA) and includes SHA-1, SHA-2 (a family within a family that includes SHA-224, SHA-256, SHA-384, and SHA-512), and SHA-3 (SHA3-224, SHA3-256, SHA3-384, and SHA3-512).
What is the main purpose of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
Why do people use hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
SHA-256 can help secure SSL/TLS (Transport Layer Security) certificates by creating a digital signature your device can verify. For example, when a server presents its TLS certificate to clients such as web browsers, the client can then use the corresponding public key to decrypt and verify the signature.

Furthermore, Bitcoin transactions are digitally signed via the private keys of senders to prove ownership before bitcoins are sent. That is, the transaction data is hashed using SHA-256, and then the hash is signed using the sender's private key with the aforementioned ECDSA.
Why is hashing used in cyber security
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.What is Target Hash A target hash is a number that must be greater than or equal to a hashed block header for a new block to be awarded. The target hash is used to determine the difficulty of input and can be adjusted to ensure efficient processing of the blocks.
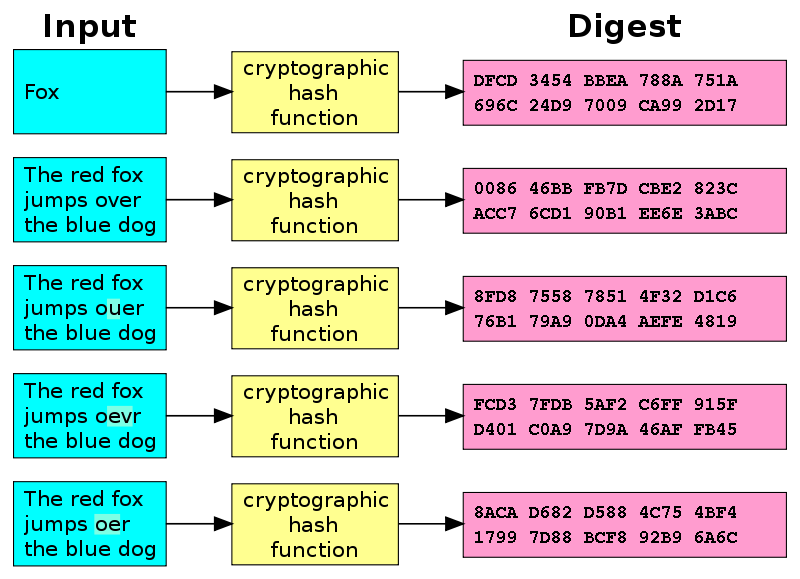
In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
Why use hashing instead of encryption : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is SHA-256 so popular : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
What is the function of SHA hashing
SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.

The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.The double hashing is invented by Ferguson and Schneier in their book Practical Cryptography to countermeasure against length extension attacks. As a side note, double-hashing doesn't prevent collision attacks since any collision SHA256(x)=SHA256(y) is also a collision for SHA256(SHA256(x))=SHA256(SHA256(y)).
Why do we need hashing : Hashing enables efficient data retrieval in hash tables, especially when dealing with large data sets. It uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map.