The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
What is the use of hash function in real life : Hash functions are commonly used data structures in computing systems for tasks such as checking the integrity of messages and authenticating information. While they are considered cryptographically "weak" because they can be solved in polynomial time, they are not easily decipherable.
Why use hashing instead of encryption
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why are hashes so secure : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
It would be impossible to figure out the original data of the function with just the resulting hash – as not much of that data is left – the only workable method is to brute force every possible combination. If we could reverse a hash, we would be able to compress data of any size into a mere few bytes of data. Some common use cases for hashing functions include the following ones:
Detecting duplicated records.
Locating points that are near each other.
Verifying message integrity.
Verifying passwords.
Should I hash or encrypt
Encryption techniques protect data in motion. Hashing protects data at rest. Combining these strategies could, in theory, put a strong security boundary around critical assets. But both come with risks and benefits you should know about.For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed. Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.
Why use hashing over encryption : Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.
Why is a hash function required in cryptography : Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.
What is the weakness of hashing
Hash tables are widely used data structures that offer efficient data retrieval and storage, but they also have some disadvantages: Collisions: One of the primary disadvantages of hash tables is the potential for collisions. Collisions occur when two different keys hash to the same index in the table. Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.However, when a hash function is used to produce fixed-length hashes of input messages that are longer than the hash, the function is truly one-way, because the same hash can be produced by multiple input messages and there is no way to know which possible input message was the correct one.
Why is hashing not safe : Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible.
Antwort Why do we need hashing? Weitere Antworten – What is the main purpose of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
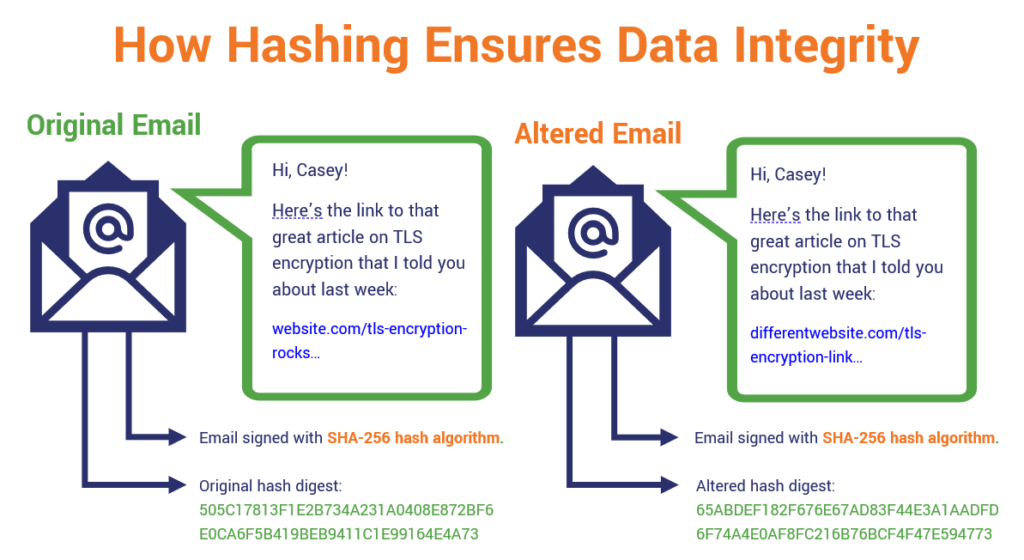
What is the use of hash function in real life : Hash functions are commonly used data structures in computing systems for tasks such as checking the integrity of messages and authenticating information. While they are considered cryptographically "weak" because they can be solved in polynomial time, they are not easily decipherable.
Why use hashing instead of encryption
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why are hashes so secure : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
It would be impossible to figure out the original data of the function with just the resulting hash – as not much of that data is left – the only workable method is to brute force every possible combination. If we could reverse a hash, we would be able to compress data of any size into a mere few bytes of data.
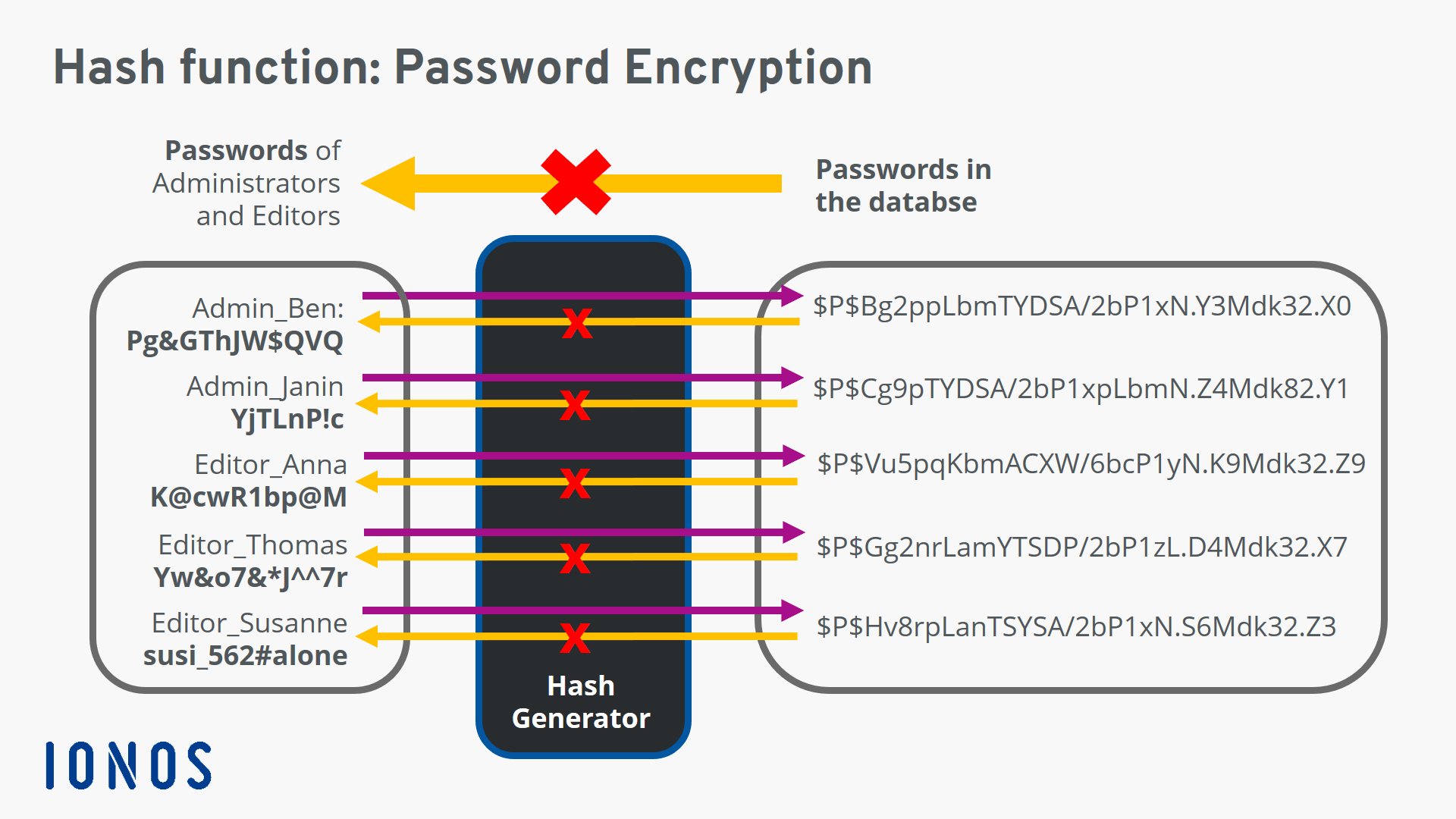
Some common use cases for hashing functions include the following ones:
Should I hash or encrypt
Encryption techniques protect data in motion. Hashing protects data at rest. Combining these strategies could, in theory, put a strong security boundary around critical assets. But both come with risks and benefits you should know about.For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed.

Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.
Why use hashing over encryption : Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.
Why is a hash function required in cryptography : Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.
What is the weakness of hashing
Hash tables are widely used data structures that offer efficient data retrieval and storage, but they also have some disadvantages: Collisions: One of the primary disadvantages of hash tables is the potential for collisions. Collisions occur when two different keys hash to the same index in the table.
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.However, when a hash function is used to produce fixed-length hashes of input messages that are longer than the hash, the function is truly one-way, because the same hash can be produced by multiple input messages and there is no way to know which possible input message was the correct one.
Why is hashing not safe : Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible.