Hashes provide security to an organization's cyber system so that hackers cannot steal it; for example, email passwords stored on servers.Hashing and encryption differ in their advantages based on their speed and security. Hashing is faster than encryption, because it does not involve complex mathematical operations or key management.Encryption scrambles data that can be decoded with a key. The intent is to pass the information to another party, and the recipient will use keys to decipher the data. Hashing also scrambles data, but the intent is to prove its authenticity.
What is the primary reason for using cryptographic hash algorithm over encryption on user passwords : Password verification commonly relies on cryptographic hashes. Storing all user passwords as cleartext can result in a massive security breach if the password file is compromised. One way to reduce this danger is to only store the hash digest of each password.
Why can’t you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Is SHA-256 hash safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
Security Vulnerabilities: If a weak or poorly designed hash function is used, it can be vulnerable to various attacks, such as collision attacks, rainbow table attacks, and preimage attacks. How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed.
Can hashed passwords be hacked
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.There is a difference between hashing and encryption. SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted. SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.
Is SHA-512 safer than SHA-256 : SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Can hashing be broken : Indeed there are some cryptographic hash functions based on number-theoretical problems, such as x2(modN), that can be exponentially broken with a quantum computer. Here, N is the product of two large prime numbers N=p1×p2, and x is a binary representation of the string to be hashed.
Why is hash not secure
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords. Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.Simply put, no. Ultimately all Machine Learning methods are extensions of gradient descent. The "gradient" of the space of inverse hash functions is intentionally a fractal hellscape that is basically impossible to traverse.
Can a hashed password be unhashed : Unlike encrypted data, hashed data cannot be unhashed; the hashing process is irreversible, thanks to the algorithms used.
Antwort Why are hashes so secure? Weitere Antworten – Are hashes secure
Hashes provide security to an organization's cyber system so that hackers cannot steal it; for example, email passwords stored on servers.Hashing and encryption differ in their advantages based on their speed and security. Hashing is faster than encryption, because it does not involve complex mathematical operations or key management.Encryption scrambles data that can be decoded with a key. The intent is to pass the information to another party, and the recipient will use keys to decipher the data. Hashing also scrambles data, but the intent is to prove its authenticity.
What is the primary reason for using cryptographic hash algorithm over encryption on user passwords : Password verification commonly relies on cryptographic hashes. Storing all user passwords as cleartext can result in a massive security breach if the password file is compromised. One way to reduce this danger is to only store the hash digest of each password.
Why can’t you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Is SHA-256 hash safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
Security Vulnerabilities: If a weak or poorly designed hash function is used, it can be vulnerable to various attacks, such as collision attacks, rainbow table attacks, and preimage attacks.
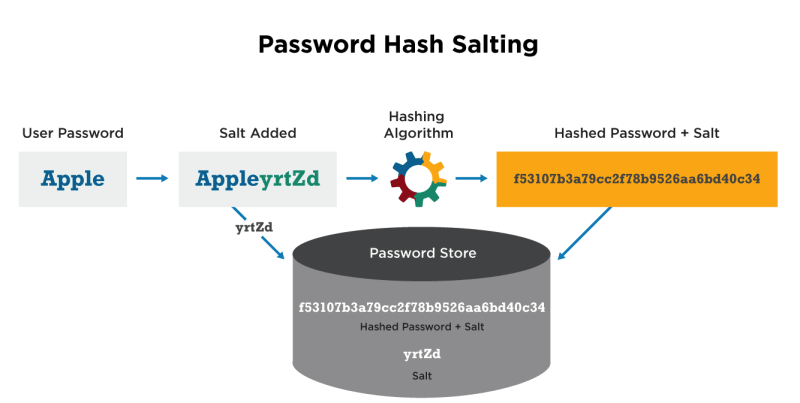
How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed.
Can hashed passwords be hacked
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.There is a difference between hashing and encryption. SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.

SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.
Is SHA-512 safer than SHA-256 : SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Can hashing be broken : Indeed there are some cryptographic hash functions based on number-theoretical problems, such as x2(modN), that can be exponentially broken with a quantum computer. Here, N is the product of two large prime numbers N=p1×p2, and x is a binary representation of the string to be hashed.
Why is hash not secure
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.

Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.Simply put, no. Ultimately all Machine Learning methods are extensions of gradient descent. The "gradient" of the space of inverse hash functions is intentionally a fractal hellscape that is basically impossible to traverse.
Can a hashed password be unhashed : Unlike encrypted data, hashed data cannot be unhashed; the hashing process is irreversible, thanks to the algorithms used.