Hashing is primarily used for security purposes, and specifically those in cybersecurity. A hashed value has many uses, but it's primarily meant to encode a plaintext value so the enclosed information can't be exposed.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is a real life example of a hash table : There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is an example of hashing
Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.
How are hashes used by hackers : It's common for hackers to use specialized hash-dumping tools to extract password information from a target computer or network. These tools typically store passwords in a specific format (such as the Windows Security Account Manager database).
Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common. Cryptographic hash functions combine message-passing capabilities with security properties. It is used in many applications, from database security to cryptocurrency. On the Bitcoin blockchain, the nonce is a number used when a miner generates a hash from the block header to compare to the network difficulty target.
Why is hashing used in Bitcoin
Hashes are used to secure information—in the case of cryptocurrency, they are used to ensure data contained in the blocks on a blockchain are not altered.Hashing is simply passing some data through a formula that produces a result, called a hash. That hash is usually a string of characters and the hashes generated by a formula are always the same length, regardless of how much data you feed into it. For example, the MD5 formula always produces 32 character-long hashes.As you continue to engage with computer science, consider the two primary use-cases for hash tables: data retrieval and data insertion.
Data Retrieval: Hash Tables are known for their phenomenal speed in data retrieval.
Data Insertion: Similar to data retrieval, data insertion in a Hash Table is also O(1).
Bitcoin uses the SHA-256 hash algorithm to generate verifiably “random” numbers in a way that requires a predictable amount of CPU effort. Generating a SHA-256 hash with a value less than the current target solves a block and wins you some coins.
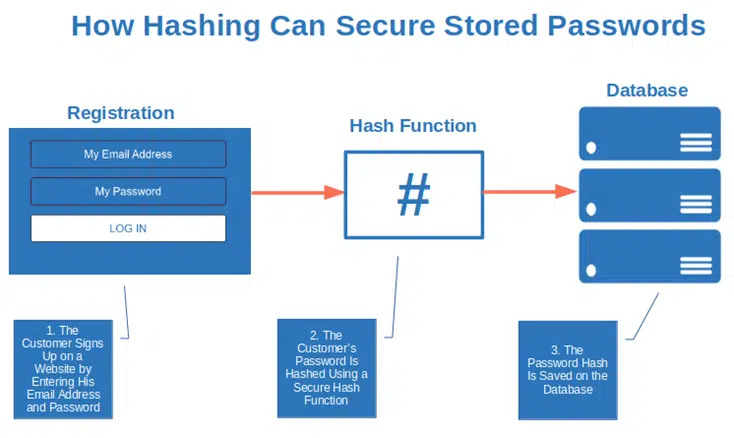
Is hashing used for passwords : Password hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords.
Does Google use hashing : How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.
Does Bitcoin use hash
On the Bitcoin blockchain, the nonce is a number used when a miner generates a hash from the block header to compare to the network difficulty target. Block rewards are new cryptocurrencies and fees awarded to miners for validating transactions in blockchains with Proof-of-Work (PoW) consensus mechanisms. Blockchain hash verifies the integrity of data transferred from one place to another. Hashing makes this verification process faster and easier. This will verify if the data being transferred has been altered in any way.The most commonly used hash function on Ethereum is Keccak256. However, it's crucial to exercise caution, as some libraries may refer to Keccak256 as SHA-256, which is a distinct hash function. SHA-256 is a variant of SHA-2 (Secure Hash Algorithm 2) with a 256-bit output and is extensively employed by Bitcoin.
Why use hashing instead of encryption : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Antwort Where is hashing used? Weitere Antworten – Where are hashes used
Hashing is primarily used for security purposes, and specifically those in cybersecurity. A hashed value has many uses, but it's primarily meant to encode a plaintext value so the enclosed information can't be exposed.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is a real life example of a hash table : There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is an example of hashing
Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.
How are hashes used by hackers : It's common for hackers to use specialized hash-dumping tools to extract password information from a target computer or network. These tools typically store passwords in a specific format (such as the Windows Security Account Manager database).
Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common.

Cryptographic hash functions combine message-passing capabilities with security properties. It is used in many applications, from database security to cryptocurrency. On the Bitcoin blockchain, the nonce is a number used when a miner generates a hash from the block header to compare to the network difficulty target.
Why is hashing used in Bitcoin
Hashes are used to secure information—in the case of cryptocurrency, they are used to ensure data contained in the blocks on a blockchain are not altered.Hashing is simply passing some data through a formula that produces a result, called a hash. That hash is usually a string of characters and the hashes generated by a formula are always the same length, regardless of how much data you feed into it. For example, the MD5 formula always produces 32 character-long hashes.As you continue to engage with computer science, consider the two primary use-cases for hash tables: data retrieval and data insertion.
Bitcoin uses the SHA-256 hash algorithm to generate verifiably “random” numbers in a way that requires a predictable amount of CPU effort. Generating a SHA-256 hash with a value less than the current target solves a block and wins you some coins.
Is hashing used for passwords : Password hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords.
Does Google use hashing : How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.
Does Bitcoin use hash
On the Bitcoin blockchain, the nonce is a number used when a miner generates a hash from the block header to compare to the network difficulty target. Block rewards are new cryptocurrencies and fees awarded to miners for validating transactions in blockchains with Proof-of-Work (PoW) consensus mechanisms.
Blockchain hash verifies the integrity of data transferred from one place to another. Hashing makes this verification process faster and easier. This will verify if the data being transferred has been altered in any way.The most commonly used hash function on Ethereum is Keccak256. However, it's crucial to exercise caution, as some libraries may refer to Keccak256 as SHA-256, which is a distinct hash function. SHA-256 is a variant of SHA-2 (Secure Hash Algorithm 2) with a 256-bit output and is extensively employed by Bitcoin.
Why use hashing instead of encryption : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.