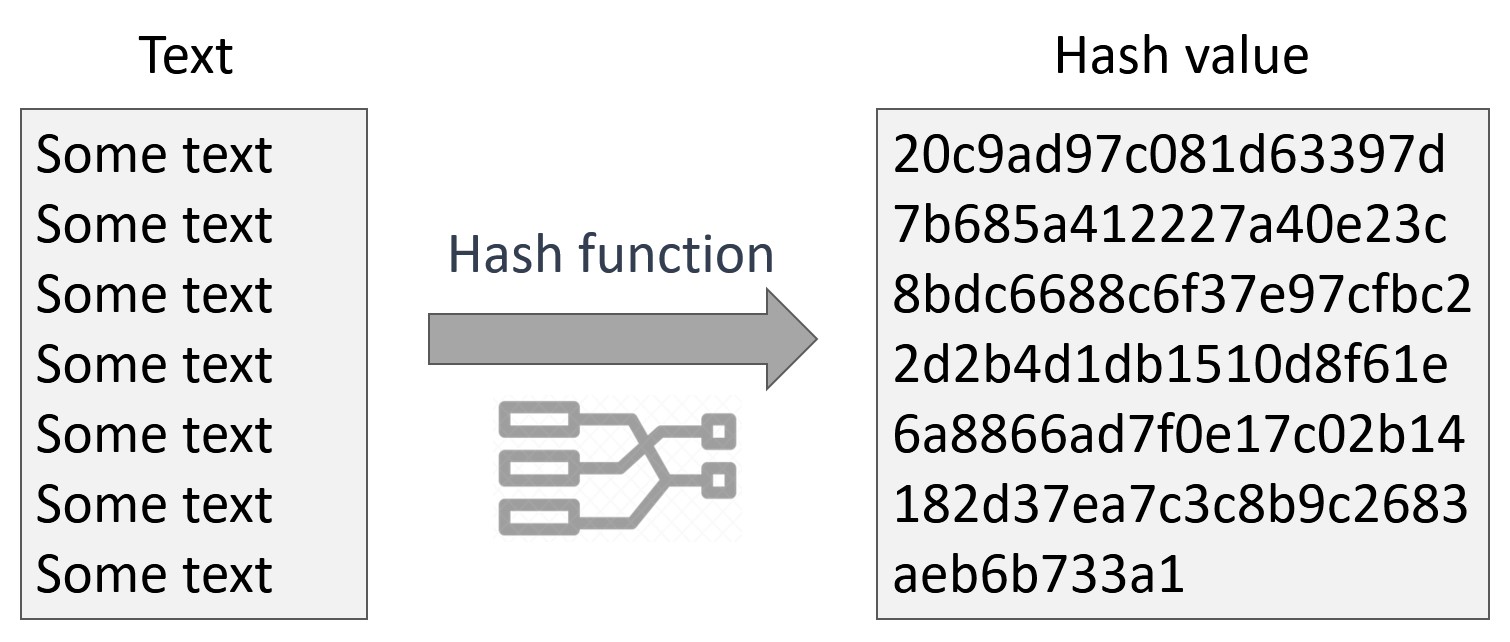
Hash values are also useful for verifying the integrity of data sent through insecure channels. The hash value of received data can be compared to the hash value of data as it was sent to determine whether the data was altered.Hash functions are mathematical functions that transform or "map" a given data set into a bit string of fixed size, also known as the "hash value." Hash functions are used in cryptography and have variable levels of complexity and difficulty.There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
When to use hashing : Hashing is commonly used to ensure data integrity. By generating a hash value for an amount of data, such as a file or message, a user can later compare it with the hash value of the received data to verify if any changes or corruption occurred during transmission.
Why do we need hash
Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
What are the applications of hashing : Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.
Applications of Hashing Algorithms
Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity.
Signature generation and verification.
Password verification.
Proof-of-work.
File or data identifier.
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
How is hashing used in real life problems
Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.Hash is used for cache mapping for fast access of the data. Hash can be used for password verification. Hash is used in cryptography as a message digest.Security: Hashing is a fundamental component of many security processes. It's used to securely store passwords, as well as to ensure the integrity of software and data. For example, when you download software, the publisher often provides the hash value of the software package so that you can verify its authenticity. Hash Tables: The most common use of hash functions in DSA is in hash tables, which provide an efficient way to store and retrieve data. Data Integrity: Hash functions are used to ensure the integrity of data by generating checksums.
What is the most common use of hashing : Some of the most common applications of hashing in cybersecurity are: Message integrity. File integrity. Password validation.
Why do people use hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Why do we use hash values on files
Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions. The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
What is the most popular hash functions : Commonly used hash functions:
SHA-1: SHA-1 is a 160-bit hash function that was widely used for digital signatures and other applications.
SHA-2: SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512.
Antwort Where are hash values used? Weitere Antworten – What is the use of hash value
Hash values are also useful for verifying the integrity of data sent through insecure channels. The hash value of received data can be compared to the hash value of data as it was sent to determine whether the data was altered.Hash functions are mathematical functions that transform or "map" a given data set into a bit string of fixed size, also known as the "hash value." Hash functions are used in cryptography and have variable levels of complexity and difficulty.There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
When to use hashing : Hashing is commonly used to ensure data integrity. By generating a hash value for an amount of data, such as a file or message, a user can later compare it with the hash value of the received data to verify if any changes or corruption occurred during transmission.
Why do we need hash
Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
What are the applications of hashing : Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.
Applications of Hashing Algorithms
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
How is hashing used in real life problems
Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.Hash is used for cache mapping for fast access of the data. Hash can be used for password verification. Hash is used in cryptography as a message digest.Security: Hashing is a fundamental component of many security processes. It's used to securely store passwords, as well as to ensure the integrity of software and data. For example, when you download software, the publisher often provides the hash value of the software package so that you can verify its authenticity.
.png)
Hash Tables: The most common use of hash functions in DSA is in hash tables, which provide an efficient way to store and retrieve data. Data Integrity: Hash functions are used to ensure the integrity of data by generating checksums.
What is the most common use of hashing : Some of the most common applications of hashing in cybersecurity are: Message integrity. File integrity. Password validation.
Why do people use hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Why do we use hash values on files
Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function.Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
What is the most popular hash functions : Commonly used hash functions: