Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is the most commonly used hashing algorithm today : The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function. It is the fastest of all the . NET hashing algorithms, but it uses a smaller 128-bit hash value, making it the most vulnerable to attack over the long term.
What are the use cases of hash functions
Applications of Hashing Algorithms
Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity.
Signature generation and verification.
Password verification.
Proof-of-work.
File or data identifier.
What is the most popular hash functions : Commonly used hash functions:
SHA-1: SHA-1 is a 160-bit hash function that was widely used for digital signatures and other applications.
SHA-2: SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512.
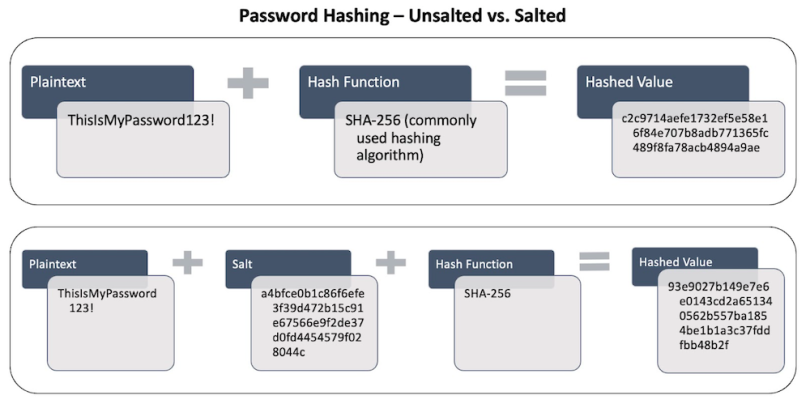
Password Verification: Cryptographic hash functions are very commonly used in password verification. Let's understand this using an Example: When you use any online website which requires a user login, you enter your E-mail and password to authenticate that the account you are trying to use belongs to you. So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What is a good example of hash function
For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.Every time you attempt to log in to your email account, your email provider hashes the password YOU enter and compares this hash to the hash it has saved. Only when the two hashes match are you authorized to access your email.Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common. Password storage: Hashing is used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password. Data compression: Hashing is used in data compression algorithms, such as the Huffman coding algorithm, to encode data efficiently.
Where are hash values used : A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures.
What are simple examples of hash functions : Say we are given keys in the range 0 to 999, and have a hash table of size 10. In this case, a possible hash function might simply divide the key value by 100. Thus, all keys in the range 0 to 99 would hash to slot 0, keys 100 to 199 would hash to slot 1, and so on.
What are two examples of the use of hashing
Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching. Database indexing: Hashing is used to index and retrieve data efficiently in databases and other data storage systems. Password storage: Hashing is used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password.Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
Does Google use hashing : How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.
Antwort Where are hash functions used today? Weitere Antworten – Where do we use hash functions
Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is the most commonly used hashing algorithm today : The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function. It is the fastest of all the . NET hashing algorithms, but it uses a smaller 128-bit hash value, making it the most vulnerable to attack over the long term.
What are the use cases of hash functions
Applications of Hashing Algorithms
What is the most popular hash functions : Commonly used hash functions:
Password Verification: Cryptographic hash functions are very commonly used in password verification. Let's understand this using an Example: When you use any online website which requires a user login, you enter your E-mail and password to authenticate that the account you are trying to use belongs to you.

So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What is a good example of hash function
For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.Every time you attempt to log in to your email account, your email provider hashes the password YOU enter and compares this hash to the hash it has saved. Only when the two hashes match are you authorized to access your email.Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common.

Password storage: Hashing is used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password. Data compression: Hashing is used in data compression algorithms, such as the Huffman coding algorithm, to encode data efficiently.
Where are hash values used : A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures.
What are simple examples of hash functions : Say we are given keys in the range 0 to 999, and have a hash table of size 10. In this case, a possible hash function might simply divide the key value by 100. Thus, all keys in the range 0 to 99 would hash to slot 0, keys 100 to 199 would hash to slot 1, and so on.
What are two examples of the use of hashing
Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.
Database indexing: Hashing is used to index and retrieve data efficiently in databases and other data storage systems. Password storage: Hashing is used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password.Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
Does Google use hashing : How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.