The very first hashing algorithm, developed in 1958, was used for classifying and organizing data. Since then, developers have discovered dozens of uses for the technology. Your company might use a hashing algorithm for: Password storage.Definition: Hash-based cryptography was first developed by Leslie Lamport and Ralph Merkle in the late 1970s. Hash-based cryptography creates digital signature algorithms whose security is mathematically based on the security of a selected cryptographic hash function.Hashing is a one-way process where data is transformed into a fixed length alphanumeric string. This string is known as a hash or message digest. A hash cannot be reversed back to the original data because it is a one-way operation.
When to use hashing : Hashing is commonly used to ensure data integrity. By generating a hash value for an amount of data, such as a file or message, a user can later compare it with the hash value of the received data to verify if any changes or corruption occurred during transmission.
When was SHA-256 created
2001
SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family, which was slowly losing strength against brute force attacks.
Who invented hash : Information Scientist: Starting in the 1940s, Luhn devised machines and schemes for parsing information, most notably the now widely used hashing algorithm, which he suggested as a way to sort both numbers and text.
SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family, which was slowly losing strength against brute force attacks. Hans Peter Luhn
Hans Peter Luhn invented Hashing. He was a conscientious scientist in IBM researching the field of Computer Science and Information Science. There is one more famous algorithm he contributed- the Luhn algorithm.
Is SHA-256 proven to be irreversible
Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.SHA-256 refers to the bit size of the hash output. In other words, the resulting hash value from SHA-256 is 256 bits long, which provides a significantly larger search space compared to its predecessor, making it computationally infeasible to reverse engineer the original input from the hash value.Due to this one-way property, storing a hashed value of a password is a good idea since if their hash is compromised (via a database leak), the attacker would not know the original password (which is the input to the hash function). How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed.
Is SHA-2 still secure : SHA-1 and SHA-2 are the Secure Hash Algorithms required by law for use in certain U.S. Government applications, including use within other cryptographic algorithms and protocols, for the protection of sensitive unclassified information.
Did the NSA invent SHA-256 : Higher numbers indicate the length of the hashing outputs, which we'll discuss below. The origins of SHA-256 can be traced back to intelligence services in the US, namely the National Security Agency, or the NSA for short.
When was hash first made
The earliest form of Hash, known as hashish, was produced by gently rubbing growing cannabis plants together. References to hashish date back as early as the 12th and 13th centuries – it's one of the oldest forms of cannabis concentrates! The idea of hashing was introduced in the early 1950s by an IBM researcher, Hans Peter Luhn. Although Luhn didn't invent today's algorithms, his work ultimately led to the first forms of hashing.2001
SHA-512 is a hash algorithm designed by the NSA and published by NIST in FIPS PUB 180-2 [14] in 2002 (the first draft was published in 2001). The size of the output of this algorithm is 512 bits.
Can you fake SHA-256 : you can't – a hash by definition is non-reversible: in that you can't take a hash value and retrieve the input file. the sha256 hash is by definition 256 bits 'wide' – that is 32 bytes. which means at most it has 2^{256} possible values. That is all.
Antwort When was hashing invented? Weitere Antworten – When were hashes invented
The very first hashing algorithm, developed in 1958, was used for classifying and organizing data. Since then, developers have discovered dozens of uses for the technology. Your company might use a hashing algorithm for: Password storage.Definition: Hash-based cryptography was first developed by Leslie Lamport and Ralph Merkle in the late 1970s. Hash-based cryptography creates digital signature algorithms whose security is mathematically based on the security of a selected cryptographic hash function.Hashing is a one-way process where data is transformed into a fixed length alphanumeric string. This string is known as a hash or message digest. A hash cannot be reversed back to the original data because it is a one-way operation.
When to use hashing : Hashing is commonly used to ensure data integrity. By generating a hash value for an amount of data, such as a file or message, a user can later compare it with the hash value of the received data to verify if any changes or corruption occurred during transmission.
When was SHA-256 created
2001
SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family, which was slowly losing strength against brute force attacks.
Who invented hash : Information Scientist: Starting in the 1940s, Luhn devised machines and schemes for parsing information, most notably the now widely used hashing algorithm, which he suggested as a way to sort both numbers and text.
SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family, which was slowly losing strength against brute force attacks.

Hans Peter Luhn
Hans Peter Luhn invented Hashing. He was a conscientious scientist in IBM researching the field of Computer Science and Information Science. There is one more famous algorithm he contributed- the Luhn algorithm.
Is SHA-256 proven to be irreversible
Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.SHA-256 refers to the bit size of the hash output. In other words, the resulting hash value from SHA-256 is 256 bits long, which provides a significantly larger search space compared to its predecessor, making it computationally infeasible to reverse engineer the original input from the hash value.Due to this one-way property, storing a hashed value of a password is a good idea since if their hash is compromised (via a database leak), the attacker would not know the original password (which is the input to the hash function).

How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed.
Is SHA-2 still secure : SHA-1 and SHA-2 are the Secure Hash Algorithms required by law for use in certain U.S. Government applications, including use within other cryptographic algorithms and protocols, for the protection of sensitive unclassified information.
Did the NSA invent SHA-256 : Higher numbers indicate the length of the hashing outputs, which we'll discuss below. The origins of SHA-256 can be traced back to intelligence services in the US, namely the National Security Agency, or the NSA for short.
When was hash first made
The earliest form of Hash, known as hashish, was produced by gently rubbing growing cannabis plants together. References to hashish date back as early as the 12th and 13th centuries – it's one of the oldest forms of cannabis concentrates!
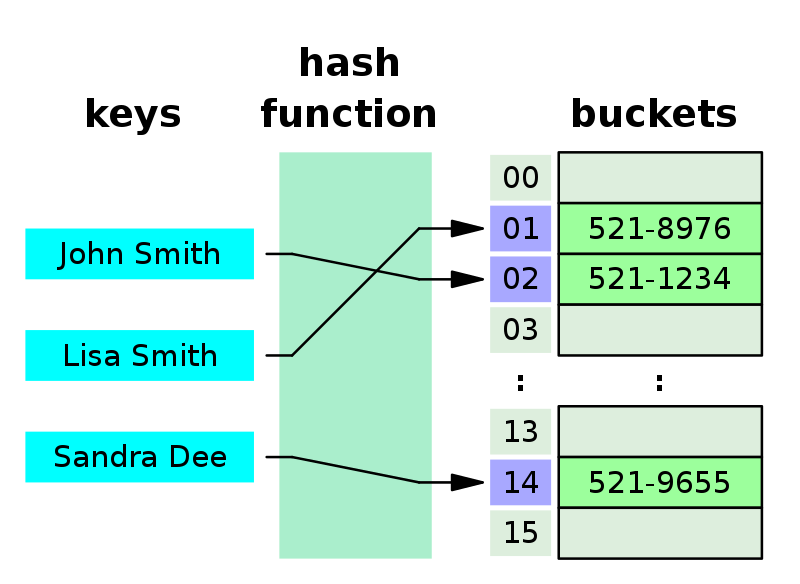
The idea of hashing was introduced in the early 1950s by an IBM researcher, Hans Peter Luhn. Although Luhn didn't invent today's algorithms, his work ultimately led to the first forms of hashing.2001
SHA-512 is a hash algorithm designed by the NSA and published by NIST in FIPS PUB 180-2 [14] in 2002 (the first draft was published in 2001). The size of the output of this algorithm is 512 bits.
Can you fake SHA-256 : you can't – a hash by definition is non-reversible: in that you can't take a hash value and retrieve the input file. the sha256 hash is by definition 256 bits 'wide' – that is 32 bytes. which means at most it has 2^{256} possible values. That is all.