Type 1 hypervisors offer a greater degree of isolation for each virtual environment. There's no shared layer like there is with the operating system for a type 2 hypervisor. This makes virtual machines running on the type 1 hypervisor inherently more secure.VMware Security vs Hyper-V Security. VMware is an enterprise-grade virtualization solution, and naturally, its security features are more robust. However, Hyper-V also provides robust security features.Best Hypervisors of 2024
Virtuozzo. Virtuozzo. The Virtuozzo platform is designed and built as a solution for running your own cloud business.
Apple Hypervisor. Apple.
VirtualBox. Oracle.
CrossOver. CodeWeavers.
Parallels Desktop for Mac. Parallels.
QEMU. QEMU.
VMware ESXi. VMware.
vSphere Hypervisor. VMware.
What is the risk of hypervisor : Since hypervisors allow a system administrator to create and monitor VMs on their hardware, the entire system could be at risk if an attacker compromises the hypervisor. Threat actors do this by exploiting outdated hypervisor software or by infecting a machine with malware.
Can a hypervisor be hacked
For a hyperjacking attack to succeed, an attacker would have to take control of the hypervisor by the following methods: Injecting a rogue hypervisor beneath the original hypervisor. Directly obtaining control of the original hypervisor. Running a rogue hypervisor on top of an existing hypervisor.
What are hypervisor vulnerabilities : Hypervisor security is important because, if attackers gain control of the hypervisor, they can access every VM under that hypervisor and all data stored in each VM. Additional points of vulnerability include shared hardware caches, the network and access to the physical server.
There is nothing about virtual computing that is inherently unsecure; it is just a new security attack vector [Higgins07]. The virtual machine layer is more secure than any OS, due to its simplicity and strict access control. If you prioritize industry support, robust management tools, and a wide range of features, VMware and its ESXi offering is the suitable choice. On the other hand, if you have a Windows-based environment, prefer seamless integration with Microsoft technologies, and cost-effectiveness, Hyper-V can be a viable option.
Is ESXi still free
Along with the termination of perpetual licensing, Broadcom has also decided to discontinue the Free ESXi Hypervisor, marking it as EOGA (End of General Availability). Regrettably, there is currently no substitute product offered.ESXi: Robust Virtualization by VMware
ESXi is known for its reliability, performance, and comprehensive feature set, making it a preferred choice for many enterprises.The biggest risk of running a virtual computer is that it will go offline immediately if the server that it is housed on fails. All other virtual computers on that particular server will also go offline immediately. Since virtual machines are designed to be independent of the host server, multiple VMs can be spinned in a matter of seconds and data can be easily cloned and transferred to other hardware devices without getting noticed. This data theft can cause huge losses to an organization and result in security breaches.
Why do hackers use VMware : This means you can revert back to a stable state if anything goes wrong lastly VMS are highly portable. And can be used on any machine without needing to adjust the settings for different Hardware.
Can malware break out of a VM : While there is no guarantee that virtual machines will prevent malware from escaping the sandbox, since virtualization provides isolation and protection, the chances of malware stepping out of VMs are extremely rare. However, there have been instances where worms or malware have managed to escape virtual machines.
Are virtual machines illegal
Are virtual machines illegal Using a virtual machine is perfectly legal. However, you might run into issues if you don't have licensed versions of the operating system or software you're running within the virtual machine. While there is no guarantee that virtual machines will prevent malware from escaping the sandbox, since virtualization provides isolation and protection, the chances of malware stepping out of VMs are extremely rare.ESXi excels for large enterprises needing maximum uptime, performance, and scalability to run demanding workloads. Proxmox suits small to mid-sized organizations requiring virtualization on a budget, with enough power and flexibility for most workloads.
Is Hyper-V bare-metal : Microsoft Hyper-V Architecture
Hyper-V is a Type 1 hypervisor which is installed on bare-metal servers, or on the Windows 10 operating system, but then boots up before the operating system does and runs it as a guest OS.
Antwort What is the safest hypervisor? Weitere Antworten – Which hypervisor is highly secure
Type 1 hypervisors offer a greater degree of isolation for each virtual environment. There's no shared layer like there is with the operating system for a type 2 hypervisor. This makes virtual machines running on the type 1 hypervisor inherently more secure.VMware Security vs Hyper-V Security. VMware is an enterprise-grade virtualization solution, and naturally, its security features are more robust. However, Hyper-V also provides robust security features.Best Hypervisors of 2024
What is the risk of hypervisor : Since hypervisors allow a system administrator to create and monitor VMs on their hardware, the entire system could be at risk if an attacker compromises the hypervisor. Threat actors do this by exploiting outdated hypervisor software or by infecting a machine with malware.
Can a hypervisor be hacked
For a hyperjacking attack to succeed, an attacker would have to take control of the hypervisor by the following methods: Injecting a rogue hypervisor beneath the original hypervisor. Directly obtaining control of the original hypervisor. Running a rogue hypervisor on top of an existing hypervisor.
What are hypervisor vulnerabilities : Hypervisor security is important because, if attackers gain control of the hypervisor, they can access every VM under that hypervisor and all data stored in each VM. Additional points of vulnerability include shared hardware caches, the network and access to the physical server.
There is nothing about virtual computing that is inherently unsecure; it is just a new security attack vector [Higgins07]. The virtual machine layer is more secure than any OS, due to its simplicity and strict access control.
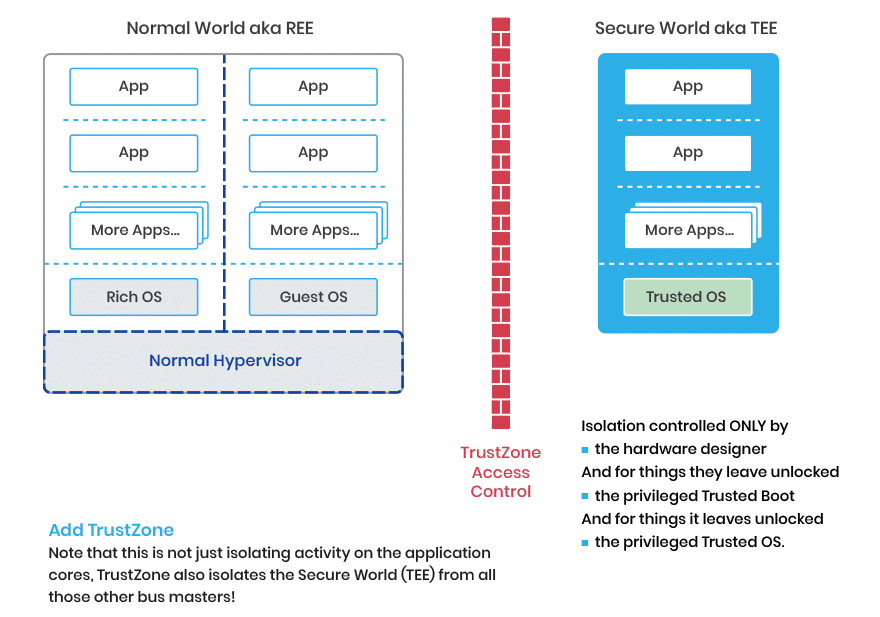
If you prioritize industry support, robust management tools, and a wide range of features, VMware and its ESXi offering is the suitable choice. On the other hand, if you have a Windows-based environment, prefer seamless integration with Microsoft technologies, and cost-effectiveness, Hyper-V can be a viable option.
Is ESXi still free
Along with the termination of perpetual licensing, Broadcom has also decided to discontinue the Free ESXi Hypervisor, marking it as EOGA (End of General Availability). Regrettably, there is currently no substitute product offered.ESXi: Robust Virtualization by VMware
ESXi is known for its reliability, performance, and comprehensive feature set, making it a preferred choice for many enterprises.The biggest risk of running a virtual computer is that it will go offline immediately if the server that it is housed on fails. All other virtual computers on that particular server will also go offline immediately.

Since virtual machines are designed to be independent of the host server, multiple VMs can be spinned in a matter of seconds and data can be easily cloned and transferred to other hardware devices without getting noticed. This data theft can cause huge losses to an organization and result in security breaches.
Why do hackers use VMware : This means you can revert back to a stable state if anything goes wrong lastly VMS are highly portable. And can be used on any machine without needing to adjust the settings for different Hardware.
Can malware break out of a VM : While there is no guarantee that virtual machines will prevent malware from escaping the sandbox, since virtualization provides isolation and protection, the chances of malware stepping out of VMs are extremely rare. However, there have been instances where worms or malware have managed to escape virtual machines.
Are virtual machines illegal
Are virtual machines illegal Using a virtual machine is perfectly legal. However, you might run into issues if you don't have licensed versions of the operating system or software you're running within the virtual machine.

While there is no guarantee that virtual machines will prevent malware from escaping the sandbox, since virtualization provides isolation and protection, the chances of malware stepping out of VMs are extremely rare.ESXi excels for large enterprises needing maximum uptime, performance, and scalability to run demanding workloads. Proxmox suits small to mid-sized organizations requiring virtualization on a budget, with enough power and flexibility for most workloads.
Is Hyper-V bare-metal : Microsoft Hyper-V Architecture
Hyper-V is a Type 1 hypervisor which is installed on bare-metal servers, or on the Windows 10 operating system, but then boots up before the operating system does and runs it as a guest OS.