Hashing helps to both encrypt and decrypt digital signatures, which are mathematical algorithms used to routinely validate the authenticity and integrity of a digital document or message. Hash functions transform the digital signature before the hash value, and the signature gets sent to the receiver.Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hash functions are commonly used data structures in computing systems for tasks such as checking the integrity of messages and authenticating information. While they are considered cryptographically "weak" because they can be solved in polynomial time, they are not easily decipherable.
What is the use of a hash table : A hash table is a data structure that is used to store keys/value pairs. It uses a hash function to compute an index into an array in which an element will be inserted or searched. By using a good hash function, hashing can work well.
Why do we need hash
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What can a hash tell you : A hash value is a numeric value of a fixed length that uniquely identifies data.
The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted. So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What is the aim of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.The hash symbol represents a command for the preprocessor, and is known as a macro. It literally tells your computer to take the code in the included file and place it where the #include statement is.Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Medium- and short-chain-3-hydroxyacyl-coenzyme A (CoA) dehydrogenase (SCHAD) (gene name, hadh) catalyze the third reaction of the mitochondrial β-oxidation cascade, the oxidation of 3-hydroxyacyl-CoA to 3-ketoacyl-CoA, for medium- and short-chain fatty acids.
What does the hash allow you to do : In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
What is the goal of hashing : In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
Why is hash value important
A hash value guarantees authenticity thanks to four particular characteristics: It is deterministic, meaning that a specific input (or file) wil always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file. Expert-Verified Answer
The goal of hashing is to produce a search that takes constant time, O(1) regardless of the number of items in the data set. This means that the time it takes to perform a search operation using a hash function should be the same, no matter how many items are in the data set.Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
What are the advantages of hashing : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
Antwort What is the point of a hash? Weitere Antworten – What is the point of hash
Hashing helps to both encrypt and decrypt digital signatures, which are mathematical algorithms used to routinely validate the authenticity and integrity of a digital document or message. Hash functions transform the digital signature before the hash value, and the signature gets sent to the receiver.Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hash functions are commonly used data structures in computing systems for tasks such as checking the integrity of messages and authenticating information. While they are considered cryptographically "weak" because they can be solved in polynomial time, they are not easily decipherable.
What is the use of a hash table : A hash table is a data structure that is used to store keys/value pairs. It uses a hash function to compute an index into an array in which an element will be inserted or searched. By using a good hash function, hashing can work well.
Why do we need hash
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What can a hash tell you : A hash value is a numeric value of a fixed length that uniquely identifies data.
The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.
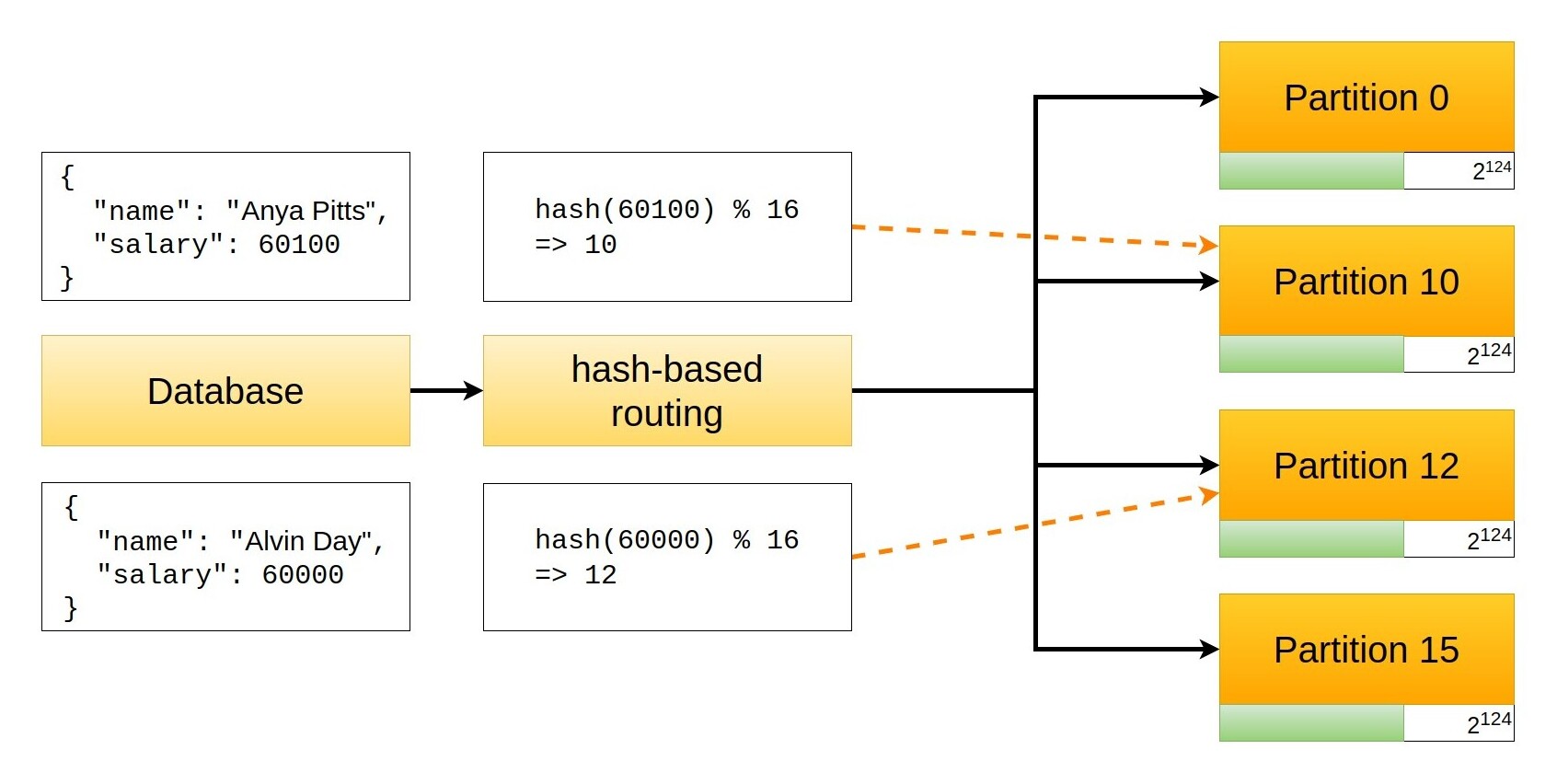
So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
What is the aim of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.The hash symbol represents a command for the preprocessor, and is known as a macro. It literally tells your computer to take the code in the included file and place it where the #include statement is.Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.

Medium- and short-chain-3-hydroxyacyl-coenzyme A (CoA) dehydrogenase (SCHAD) (gene name, hadh) catalyze the third reaction of the mitochondrial β-oxidation cascade, the oxidation of 3-hydroxyacyl-CoA to 3-ketoacyl-CoA, for medium- and short-chain fatty acids.
What does the hash allow you to do : In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
What is the goal of hashing : In addition to enabling rapid data retrieval, hashing helps encrypt and decrypt digital signatures used to authenticate message senders and receivers.
Why is hash value important
A hash value guarantees authenticity thanks to four particular characteristics: It is deterministic, meaning that a specific input (or file) wil always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file.

Expert-Verified Answer
The goal of hashing is to produce a search that takes constant time, O(1) regardless of the number of items in the data set. This means that the time it takes to perform a search operation using a hash function should be the same, no matter how many items are in the data set.Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
What are the advantages of hashing : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.