To protect passwords, experts suggest using a strong and slow hashing algorithm like Argon2 or Bcrypt, combined with salt (or even better, with salt and pepper). (Basically, avoid faster algorithms for this usage.) To verify file signatures and certificates, SHA-256 is among your best hashing algorithm choices.There are multiple types of hashing algorithms, but the most common are Message Digest 5 (MD5) and Secure Hashing Algorithm (SHA) 1 and 2. The slightest change in the data will result in a dramatic difference in the resulting hash values.What's the Most Secure Hashing Algorithm SHA-256. SHA-256 (secure hash algorithm) is an algorithm that takes an input of any length and uses it to create a 256-bit fixed-length hash value.
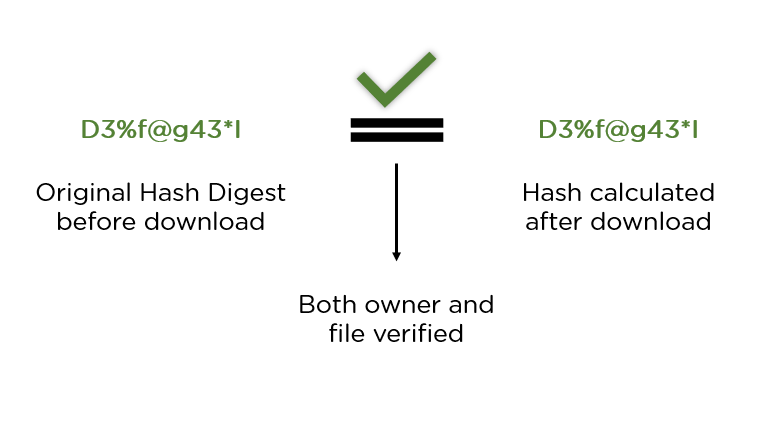
How important is the hash function : Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.
Which is better MD5 or SHA-256 hash function
The most common is SHA-256 that produces 256-bit hashes. Secondly, the SHA-2 is more secure than MD5, especially in terms of collision resistance. Therefore, the MD5 isn't recommended to use for high-security purposes.
What is the weakest hash function : The worst hash function is one that returns a constant value. I.e. all objects of that type have the same hash value, resulting in tons of collisions. While collisions can not usually be avoided entirely, minimising them is important for the performance of anything working with hashes.
The easiest example of a cryptographic hash function is the Rabin function, modular squaring. It works like this: Take your input as a number (any digital data can easily be interpreted as a binary number). Square it. SHA-256 (Secure Hash Algorithm 256-bit)
It is known for its security and resistance to collision attacks, making it suitable for applications such as digital signatures, data authentication, and password hashing.
Which is better MD5 or SHA256
SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.The importance of hash functions is evident in their widespread use in various applications such as digital signatures, password storage, and message authentication codes. These functions have proven to be a reliable method for protecting data and ensuring that it has not been tampered with or altered. The most common is SHA-256 that produces 256-bit hashes. Secondly, the SHA-2 is more secure than MD5, especially in terms of collision resistance. Therefore, the MD5 isn't recommended to use for high-security purposes.
Why SHA is better than MD5 : Using the MD5 technique, an attacker would require 2128 operations to determine the original message. In contrast, it will be 2160 in SHA1, which makes it very challenging to locate. SHA is a safer because of a cryptographic hash algorithm than MD5.
Which hash algorithm is broken : SHA-1 is no longer secure, and we should not rely on it for practical security. Until now, collision attacks have been more theoretical and expensive. But the SHA-1 attack is no longer theoretical.
Which hash function is obsolete
Avoid using outdated hash functions like MD5 or SHA-1, which are known to be insecure. Use appropriate hash lengths: Use appropriate hash lengths to ensure that the cryptographic hashes generated are strong enough to resist attacks. Longer hash lengths are generally more secure and harder to break. The easiest example of a cryptographic hash function is the Rabin function, modular squaring. It works like this: Take your input as a number (any digital data can easily be interpreted as a binary number). Square it.SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Should I use SHA-256 or SHA512 : SHA-256 is a secure algorithm and is the most widely used. It is computed with 32-bit words. SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.
Antwort What is the most important hash function? Weitere Antworten – What is the best hash function
To protect passwords, experts suggest using a strong and slow hashing algorithm like Argon2 or Bcrypt, combined with salt (or even better, with salt and pepper). (Basically, avoid faster algorithms for this usage.) To verify file signatures and certificates, SHA-256 is among your best hashing algorithm choices.There are multiple types of hashing algorithms, but the most common are Message Digest 5 (MD5) and Secure Hashing Algorithm (SHA) 1 and 2. The slightest change in the data will result in a dramatic difference in the resulting hash values.What's the Most Secure Hashing Algorithm SHA-256. SHA-256 (secure hash algorithm) is an algorithm that takes an input of any length and uses it to create a 256-bit fixed-length hash value.
How important is the hash function : Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.
Which is better MD5 or SHA-256 hash function
The most common is SHA-256 that produces 256-bit hashes. Secondly, the SHA-2 is more secure than MD5, especially in terms of collision resistance. Therefore, the MD5 isn't recommended to use for high-security purposes.
What is the weakest hash function : The worst hash function is one that returns a constant value. I.e. all objects of that type have the same hash value, resulting in tons of collisions. While collisions can not usually be avoided entirely, minimising them is important for the performance of anything working with hashes.
The easiest example of a cryptographic hash function is the Rabin function, modular squaring. It works like this: Take your input as a number (any digital data can easily be interpreted as a binary number). Square it.

SHA-256 (Secure Hash Algorithm 256-bit)
It is known for its security and resistance to collision attacks, making it suitable for applications such as digital signatures, data authentication, and password hashing.
Which is better MD5 or SHA256
SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.The importance of hash functions is evident in their widespread use in various applications such as digital signatures, password storage, and message authentication codes. These functions have proven to be a reliable method for protecting data and ensuring that it has not been tampered with or altered.

The most common is SHA-256 that produces 256-bit hashes. Secondly, the SHA-2 is more secure than MD5, especially in terms of collision resistance. Therefore, the MD5 isn't recommended to use for high-security purposes.
Why SHA is better than MD5 : Using the MD5 technique, an attacker would require 2128 operations to determine the original message. In contrast, it will be 2160 in SHA1, which makes it very challenging to locate. SHA is a safer because of a cryptographic hash algorithm than MD5.
Which hash algorithm is broken : SHA-1 is no longer secure, and we should not rely on it for practical security. Until now, collision attacks have been more theoretical and expensive. But the SHA-1 attack is no longer theoretical.
Which hash function is obsolete
Avoid using outdated hash functions like MD5 or SHA-1, which are known to be insecure. Use appropriate hash lengths: Use appropriate hash lengths to ensure that the cryptographic hashes generated are strong enough to resist attacks. Longer hash lengths are generally more secure and harder to break.
The easiest example of a cryptographic hash function is the Rabin function, modular squaring. It works like this: Take your input as a number (any digital data can easily be interpreted as a binary number). Square it.SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Should I use SHA-256 or SHA512 : SHA-256 is a secure algorithm and is the most widely used. It is computed with 32-bit words. SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.