The most common hash functions used in digital forensics are Message Digest 5 (MD5), and Secure Hashing Algorithm (SHA) 1 and 2.Commonly used hash functions:
SHA-1: SHA-1 is a 160-bit hash function that was widely used for digital signatures and other applications.
SHA-2: SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512.
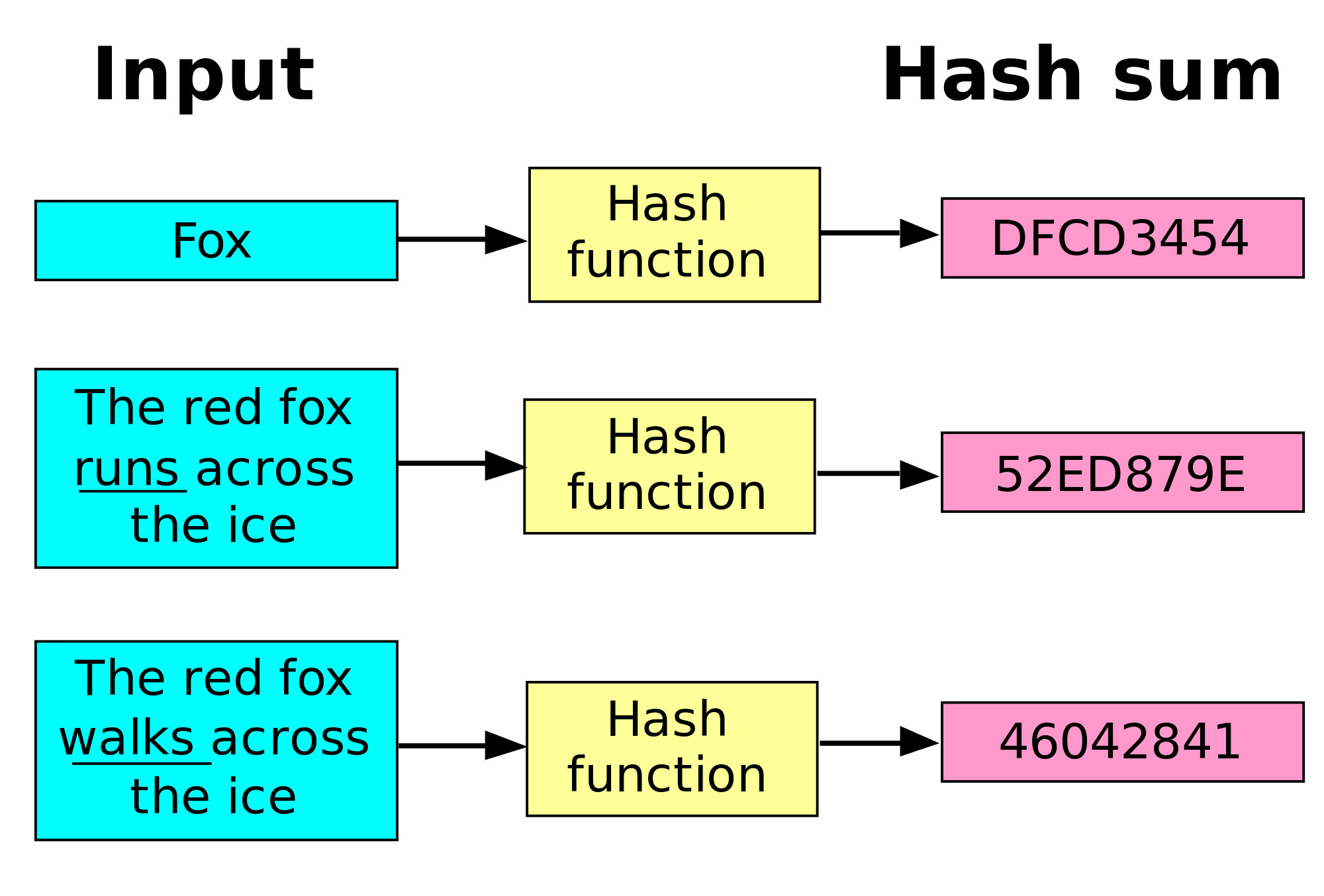
Hash functions are mathematical functions that transform or "map" a given data set into a bit string of fixed size, also known as the "hash value." Hash functions are used in cryptography and have variable levels of complexity and difficulty.
What is the most widely used hash function for SSL : The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.
What is the best hash function algorithm
SHA-256 it's a NIST's (National Institute of Standards and Technology) recommended and officially approved standard algorithm. Thanks to the possibility of verifying the content of data without showing it, it's also used by many governments and public-sector agencies worldwide, including the U.S. and Australia.
What is the simplest hash function : The simplest example of a hash function encodes the input in the same way as the output range and then discards all that exceeds the output range. For example if the output range of the hash function is 0–9 then we can interpret all input as an (base 10) integer and discard all but the last digit.
SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP. In data structures, a hash function is used to calculate the hash value of a key, which is then used to store and retrieve the corresponding data. Hash functions are often used in conjunction with an array, where the hash value is used as an index in the array.
Which hash function is mostly used in Blockchain
SHA-256
SHA-256 is the most famous of all cryptographic hash functions because it's used extensively in blockchain technology.On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.The easiest example of a cryptographic hash function is the Rabin function, modular squaring. It works like this: Take your input as a number (any digital data can easily be interpreted as a binary number). Square it. In terms of speed, the MD5 is slightly faster than SHA-2. Therefore, the MD5 is often used as a checksum for verifying files integrity. To sum up, in most cases, SHA-2 will do better than MD5. It's more secure, reliable, and less likely to be broken.
Is bcrypt better than SHA-256 : Another important detail is that SHA256 hashes don't include the salt element, which makes them more susceptible to dictionary-based cyberattacks. So while SHA256 is more suitable for applications that require frequent interaction, bcrypt is a better solution for safely storing passwords.
What are 5 common uses applications of hash functions : Applications of Hashing Algorithms
Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity.
Signature generation and verification.
Password verification.
Proof-of-work.
File or data identifier.
Which hash functions are recommended now
To protect passwords, experts suggest using a strong and slow hashing algorithm like Argon2 or Bcrypt, combined with salt (or even better, with salt and pepper). (Basically, avoid faster algorithms for this usage.) To verify file signatures and certificates, SHA-256 is among your best hashing algorithm choices. The reason why SHA-512 is faster than SHA-256 on 64-bit machines is that has 37.5% less rounds per byte (80 rounds operating on 128 byte blocks) compared to SHA- 256 (64 rounds operating on 64 byte blocks), where the operations use 64-bit integer arithmetic.SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Is there a better algorithm than SHA256 : SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.
Antwort What is the most commonly used hash function? Weitere Antworten – What is the most common hash function
The most common hash functions used in digital forensics are Message Digest 5 (MD5), and Secure Hashing Algorithm (SHA) 1 and 2.Commonly used hash functions:
Hash functions are mathematical functions that transform or "map" a given data set into a bit string of fixed size, also known as the "hash value." Hash functions are used in cryptography and have variable levels of complexity and difficulty.

What is the most widely used hash function for SSL : The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.
What is the best hash function algorithm
SHA-256 it's a NIST's (National Institute of Standards and Technology) recommended and officially approved standard algorithm. Thanks to the possibility of verifying the content of data without showing it, it's also used by many governments and public-sector agencies worldwide, including the U.S. and Australia.
What is the simplest hash function : The simplest example of a hash function encodes the input in the same way as the output range and then discards all that exceeds the output range. For example if the output range of the hash function is 0–9 then we can interpret all input as an (base 10) integer and discard all but the last digit.
SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
In data structures, a hash function is used to calculate the hash value of a key, which is then used to store and retrieve the corresponding data. Hash functions are often used in conjunction with an array, where the hash value is used as an index in the array.
Which hash function is mostly used in Blockchain
SHA-256
SHA-256 is the most famous of all cryptographic hash functions because it's used extensively in blockchain technology.On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.The easiest example of a cryptographic hash function is the Rabin function, modular squaring. It works like this: Take your input as a number (any digital data can easily be interpreted as a binary number). Square it.

In terms of speed, the MD5 is slightly faster than SHA-2. Therefore, the MD5 is often used as a checksum for verifying files integrity. To sum up, in most cases, SHA-2 will do better than MD5. It's more secure, reliable, and less likely to be broken.
Is bcrypt better than SHA-256 : Another important detail is that SHA256 hashes don't include the salt element, which makes them more susceptible to dictionary-based cyberattacks. So while SHA256 is more suitable for applications that require frequent interaction, bcrypt is a better solution for safely storing passwords.
What are 5 common uses applications of hash functions : Applications of Hashing Algorithms
Which hash functions are recommended now
To protect passwords, experts suggest using a strong and slow hashing algorithm like Argon2 or Bcrypt, combined with salt (or even better, with salt and pepper). (Basically, avoid faster algorithms for this usage.) To verify file signatures and certificates, SHA-256 is among your best hashing algorithm choices.
The reason why SHA-512 is faster than SHA-256 on 64-bit machines is that has 37.5% less rounds per byte (80 rounds operating on 128 byte blocks) compared to SHA- 256 (64 rounds operating on 64 byte blocks), where the operations use 64-bit integer arithmetic.SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security. Thus, when choosing between SHA-256 vs. SHA-512 algorithms, you must consider the trade-off between speed and security.
Is there a better algorithm than SHA256 : SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.