Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.With modular hashing, the hash function is simply h(k) = k mod m for some m (usually, the number of buckets). The value k is an integer hash code generated from the key. If m is a power of two (i.e., m=2p), then h(k) is just the p lowest-order bits of k.For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
What is hash in programming : Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.
How to use hash code
Use of hashCode in Hashing
The hashcode value received is referred to as a bucket number. Keys with the same hash code are present in the same bucket. In the same bucket, multiple (key, value) pairs may be stored in the form of a linked list. However, keys with different hash codes reside in different buckets.
How to find hash code : The hashCode() method returns the hash code of a string. where s[i] is the ith character of the string, n is the length of the string, and ^ indicates exponentiation.
The Python hash() built-in function returns an integer value for every object which is hashable. The hash method is used in programming to return integer values that can be used to compare dictionary keys using a dictionary look-up function. The simplest example of a hash function encodes the input in the same way as the output range and then discards all that exceeds the output range. For example if the output range of the hash function is 0–9 then we can interpret all input as an (base 10) integer and discard all but the last digit.
What is perfect hash code
In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions. In mathematical terms, it is an injective function. Perfect hash functions may be used to implement a lookup table with constant worst-case access time.The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash. With recent computational advancements, it has become possible to decrypt SHA-256 hashes.The hash() function allows us to obtain the hash value of an object, which is an integer used for quick comparison and dictionary key lookups.
What is the most famous hash function : The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function. It is the fastest of all the . NET hashing algorithms, but it uses a smaller 128-bit hash value, making it the most vulnerable to attack over the long term.
What is the hash code 256 : SHA-256 is a patented cryptographic hash function that outputs a value that is 256 bits long. What is hashing In encryption, data is transformed into a secure format that is unreadable unless the recipient has a key. In its encrypted form, the data may be of unlimited size, often just as long as when unencrypted.
What is the 31 hash code
There is perhaps a couple of reasons for choosing 31. The main reason is that it is a prime number and prime numbers have better distribution results in hashing algorithms, by other words the hashing outputs have less collisions for different inputs. The hash is used as a unique value of fixed size representing a large amount of data. Hashes of two sets of data should match if and only if the corresponding data also matches. Small changes to the data result in large unpredictable changes in the hash. The hash size for the SHA256 algorithm is 256 bits.As __hash__() returns an integer and is used for "binning" objects into hashtables I assume that the values of the returned integer should be uniformly distributed for common data (to minimize collisions).
What is the SHA-256 hash function : SHA-256 is a patented cryptographic hash function that outputs a value that is 256 bits long. What is hashing In encryption, data is transformed into a secure format that is unreadable unless the recipient has a key. In its encrypted form, the data may be of unlimited size, often just as long as when unencrypted.
Antwort What is the hash function code? Weitere Antworten – What is meant by hash code
Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.With modular hashing, the hash function is simply h(k) = k mod m for some m (usually, the number of buckets). The value k is an integer hash code generated from the key. If m is a power of two (i.e., m=2p), then h(k) is just the p lowest-order bits of k.For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
What is hash in programming : Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.
How to use hash code
Use of hashCode in Hashing
The hashcode value received is referred to as a bucket number. Keys with the same hash code are present in the same bucket. In the same bucket, multiple (key, value) pairs may be stored in the form of a linked list. However, keys with different hash codes reside in different buckets.
How to find hash code : The hashCode() method returns the hash code of a string. where s[i] is the ith character of the string, n is the length of the string, and ^ indicates exponentiation.
The Python hash() built-in function returns an integer value for every object which is hashable. The hash method is used in programming to return integer values that can be used to compare dictionary keys using a dictionary look-up function.
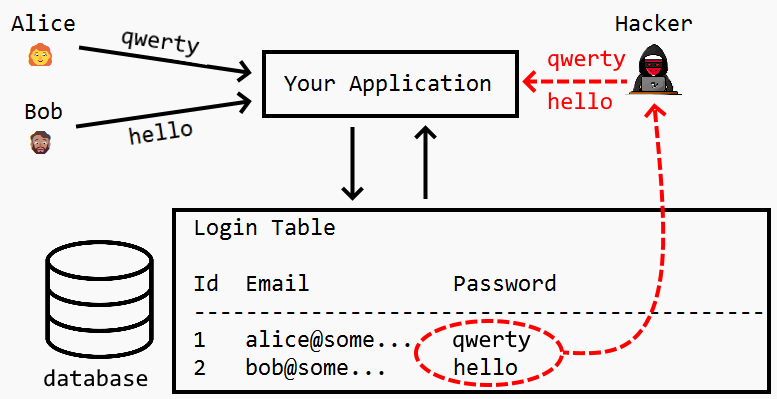
The simplest example of a hash function encodes the input in the same way as the output range and then discards all that exceeds the output range. For example if the output range of the hash function is 0–9 then we can interpret all input as an (base 10) integer and discard all but the last digit.
What is perfect hash code
In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions. In mathematical terms, it is an injective function. Perfect hash functions may be used to implement a lookup table with constant worst-case access time.The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash. With recent computational advancements, it has become possible to decrypt SHA-256 hashes.The hash() function allows us to obtain the hash value of an object, which is an integer used for quick comparison and dictionary key lookups.
Python hash() Function Example 4
What is the most famous hash function : The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function. It is the fastest of all the . NET hashing algorithms, but it uses a smaller 128-bit hash value, making it the most vulnerable to attack over the long term.
What is the hash code 256 : SHA-256 is a patented cryptographic hash function that outputs a value that is 256 bits long. What is hashing In encryption, data is transformed into a secure format that is unreadable unless the recipient has a key. In its encrypted form, the data may be of unlimited size, often just as long as when unencrypted.
What is the 31 hash code
There is perhaps a couple of reasons for choosing 31. The main reason is that it is a prime number and prime numbers have better distribution results in hashing algorithms, by other words the hashing outputs have less collisions for different inputs.
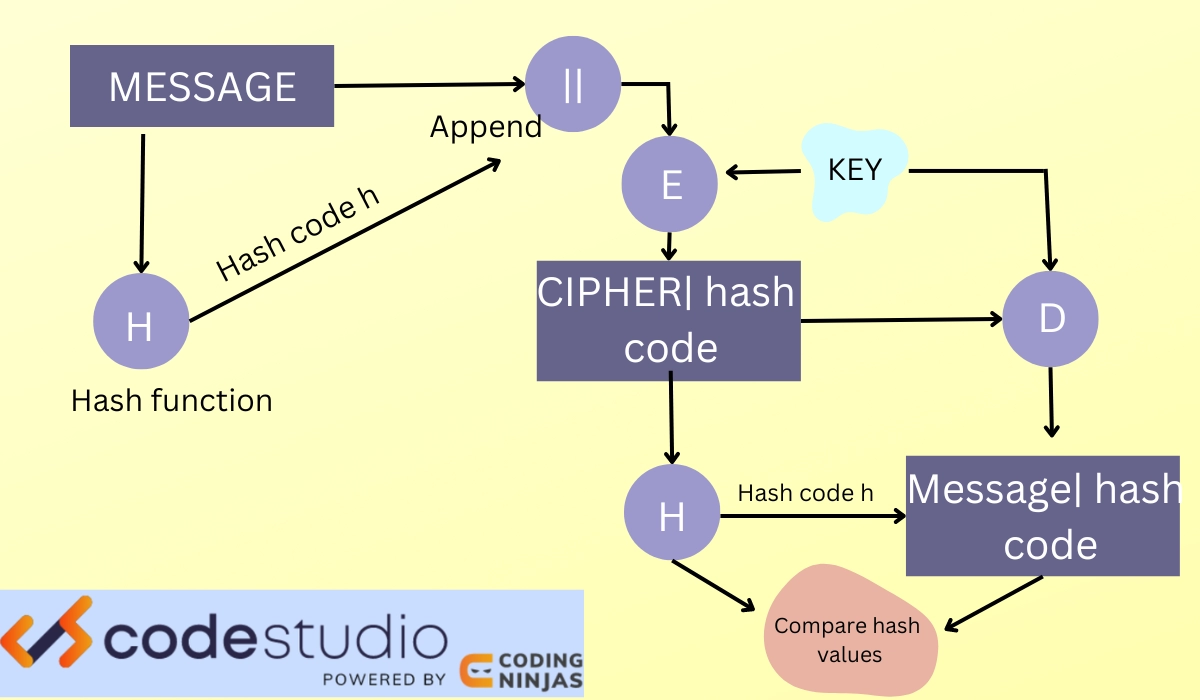
The hash is used as a unique value of fixed size representing a large amount of data. Hashes of two sets of data should match if and only if the corresponding data also matches. Small changes to the data result in large unpredictable changes in the hash. The hash size for the SHA256 algorithm is 256 bits.As __hash__() returns an integer and is used for "binning" objects into hashtables I assume that the values of the returned integer should be uniformly distributed for common data (to minimize collisions).
What is the SHA-256 hash function : SHA-256 is a patented cryptographic hash function that outputs a value that is 256 bits long. What is hashing In encryption, data is transformed into a secure format that is unreadable unless the recipient has a key. In its encrypted form, the data may be of unlimited size, often just as long as when unencrypted.