Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.Therefore, hashing is employed to index and retrieve data from a database since it speeds up the process; finding an item using a smaller hashed key than just its original value is much simpler. is employed in this situation to index and retrieve data from a database since it speeds up the process; it is much simpler …
What is a strength of using a hashing function : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
What is the aim of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is the point of hash : Hashing helps to both encrypt and decrypt digital signatures, which are mathematical algorithms used to routinely validate the authenticity and integrity of a digital document or message. Hash functions transform the digital signature before the hash value, and the signature gets sent to the receiver.
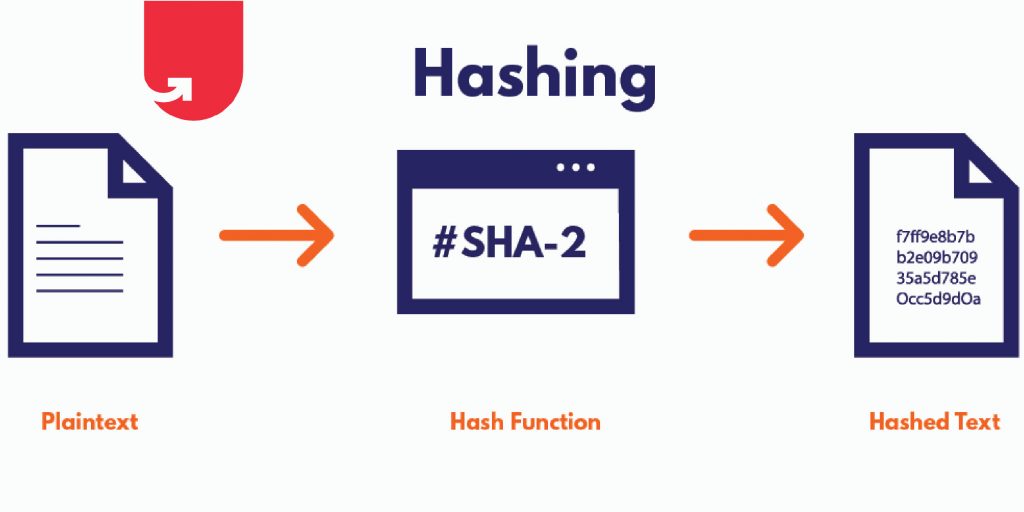
Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode. Expert-Verified Answer
The goal of hashing is to produce a search that takes constant time, O(1) regardless of the number of items in the data set. This means that the time it takes to perform a search operation using a hash function should be the same, no matter how many items are in the data set.
What is hashing mostly used for
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data.The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.What are the benefits of Hashing One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different. Expert-Verified Answer
The goal of hashing is to produce a search that takes constant time, O(1) regardless of the number of items in the data set. This means that the time it takes to perform a search operation using a hash function should be the same, no matter how many items are in the data set.
What is the benefit of hash : Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.
What are the security goals of hash function : Cryptographic hash functions are an important tool in cryptography to achieve certain security goals such as authenticity, digital signatures, digital time stamp- ing, and entity authentication. They are also strongly related to other important cryptographic tools such as block ciphers and pseudorandom functions.
What is the reason for hashing
Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Feature hashing is an essential technique for efficiently managing high-dimensional data. Despite challenges, like collisions, its advantages often prevail, especially in large-scale applications.A hash value guarantees authenticity thanks to four particular characteristics: It is deterministic, meaning that a specific input (or file) wil always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file.
What is the weakness of a hash function : Collision Risk: Collisions occur when two different inputs produce the same hash value. While good hash functions aim to minimize collisions, they are still possible. Collisions can have security implications and impact the efficiency of hash tables.
Antwort What is the goal of hash function? Weitere Antworten – What is the purpose of a hash function
Hash functions are used for data integrity and often in combination with digital signatures. With a good hash function, even a 1-bit change in a message will produce a different hash (on average, half of the bits change). With digital signatures, a message is hashed and then the hash itself is signed.Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.Therefore, hashing is employed to index and retrieve data from a database since it speeds up the process; finding an item using a smaller hashed key than just its original value is much simpler. is employed in this situation to index and retrieve data from a database since it speeds up the process; it is much simpler …
What is a strength of using a hashing function : Using hash functions for authentication offers several advantages, such as speed and efficiency in processing large amounts of data, as well as one-way protection from attackers. Hash functions are also collision-resistant, making it unlikely that two different inputs will produce the same hash.
What is the aim of hashing
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is the point of hash : Hashing helps to both encrypt and decrypt digital signatures, which are mathematical algorithms used to routinely validate the authenticity and integrity of a digital document or message. Hash functions transform the digital signature before the hash value, and the signature gets sent to the receiver.
Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.

Expert-Verified Answer
The goal of hashing is to produce a search that takes constant time, O(1) regardless of the number of items in the data set. This means that the time it takes to perform a search operation using a hash function should be the same, no matter how many items are in the data set.
What is hashing mostly used for
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data.The following are the advantages of Hashing:
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.What are the benefits of Hashing One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.
Expert-Verified Answer
The goal of hashing is to produce a search that takes constant time, O(1) regardless of the number of items in the data set. This means that the time it takes to perform a search operation using a hash function should be the same, no matter how many items are in the data set.
What is the benefit of hash : Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.
What are the security goals of hash function : Cryptographic hash functions are an important tool in cryptography to achieve certain security goals such as authenticity, digital signatures, digital time stamp- ing, and entity authentication. They are also strongly related to other important cryptographic tools such as block ciphers and pseudorandom functions.
What is the reason for hashing
Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.
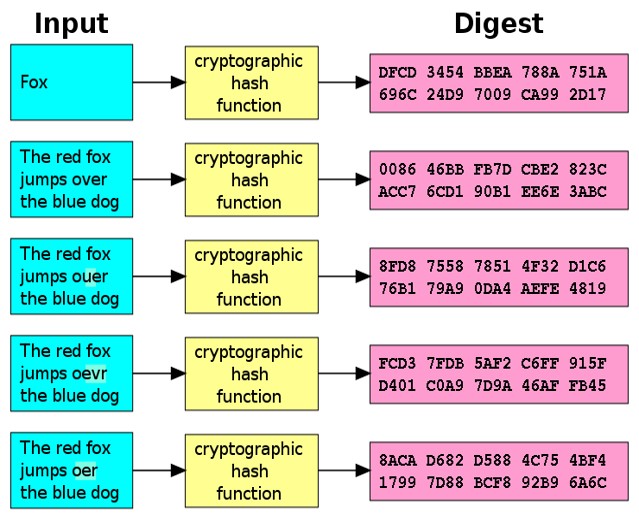
Feature hashing is an essential technique for efficiently managing high-dimensional data. Despite challenges, like collisions, its advantages often prevail, especially in large-scale applications.A hash value guarantees authenticity thanks to four particular characteristics: It is deterministic, meaning that a specific input (or file) wil always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file.
What is the weakness of a hash function : Collision Risk: Collisions occur when two different inputs produce the same hash value. While good hash functions aim to minimize collisions, they are still possible. Collisions can have security implications and impact the efficiency of hash tables.