The hash size for the SHA256 algorithm is 256 bits.256-bit
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash.MD5 produces a 128-bit output, and SHA256 produces a 256-bit output. Generally, the longer the output, the more secure the hash function, as it reduces the chances of collisions (two different inputs producing the same output).
How many characters are in a SHA-256 hash : The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash.
Why use SHA-256 hash
The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.
How to get SHA-256 hash : You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible. The SHA-256 algorithm, like other hash functions, takes any input and produces an output (often called a hash) of fixed length. It doesn't matter if the input is a single word, a full sentence, a page from a book, or an entire book, the output of a hashing algorithm like SHA256 will always be the same length.
Is SHA better than MD5
The conclusion is that SHA-2 does better than MD5 in most cases, especially regarding security. On the other hand, MD5 can be used in solutions that don't require a high level of security and when speed is the main criteria.It's also really hard to break. For example, hashing algorithms should be irreversible, but aren't always. SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.Steps in SHA-256 Algorithm
It adds some extra bits to the message, such that the length is exactly 64 bits short of a multiple of 512. During the addition, the first bit should be one, and the rest of it should be filled with zeroes. For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.
Is SHA-256 safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
How does SHA hashing work : SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.
Is SHA-256 a good hash
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. To generate SHA-1 and SHA-256 keys
Navigate to your project > Tasks > android. Double-click on signingReport. The SHA1 and SHA256 keys will be displayed in the Run tab at the bottom of the window.SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
How long does SHA-256 take to crack : SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
Antwort What is SHA256 hash generator? Weitere Antworten – What is the hash value of SHA-256
256 bits
The hash size for the SHA256 algorithm is 256 bits.256-bit
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash.MD5 produces a 128-bit output, and SHA256 produces a 256-bit output. Generally, the longer the output, the more secure the hash function, as it reduces the chances of collisions (two different inputs producing the same output).
How many characters are in a SHA-256 hash : The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash.
Why use SHA-256 hash
The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.
How to get SHA-256 hash : You can use Windows Powershell to calculate the SHA-256 checksum for a file.
On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
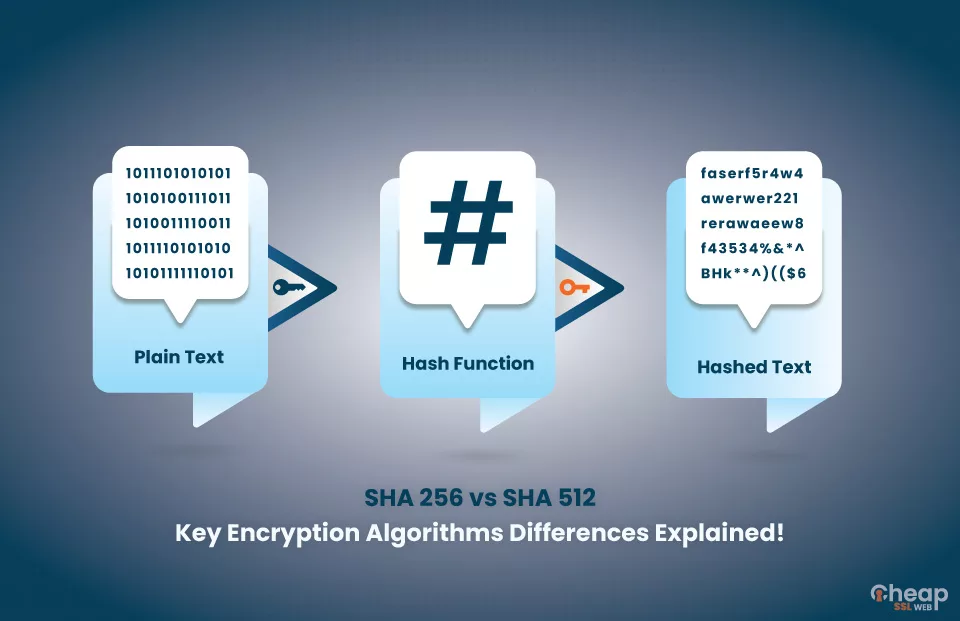
The SHA-256 algorithm, like other hash functions, takes any input and produces an output (often called a hash) of fixed length. It doesn't matter if the input is a single word, a full sentence, a page from a book, or an entire book, the output of a hashing algorithm like SHA256 will always be the same length.
Is SHA better than MD5
The conclusion is that SHA-2 does better than MD5 in most cases, especially regarding security. On the other hand, MD5 can be used in solutions that don't require a high level of security and when speed is the main criteria.It's also really hard to break. For example, hashing algorithms should be irreversible, but aren't always. SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.Steps in SHA-256 Algorithm
It adds some extra bits to the message, such that the length is exactly 64 bits short of a multiple of 512. During the addition, the first bit should be one, and the rest of it should be filled with zeroes.
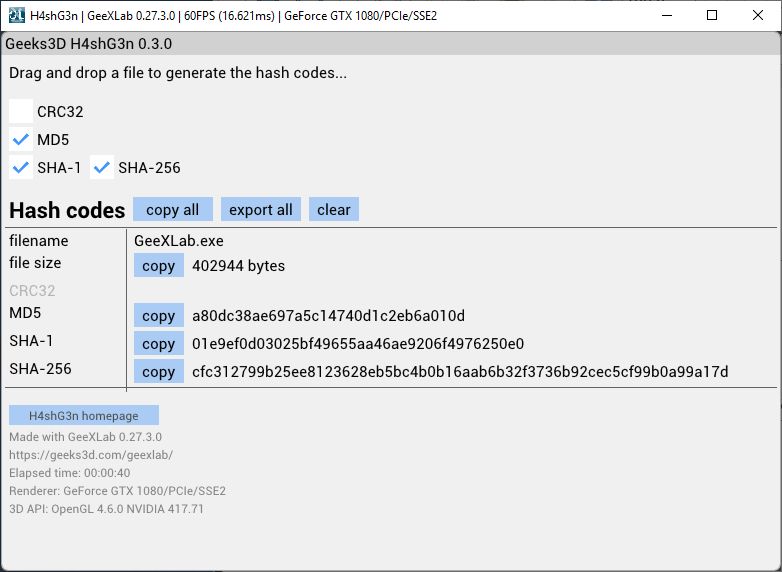
For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.
Is SHA-256 safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
How does SHA hashing work : SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.
Is SHA-256 a good hash
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value.
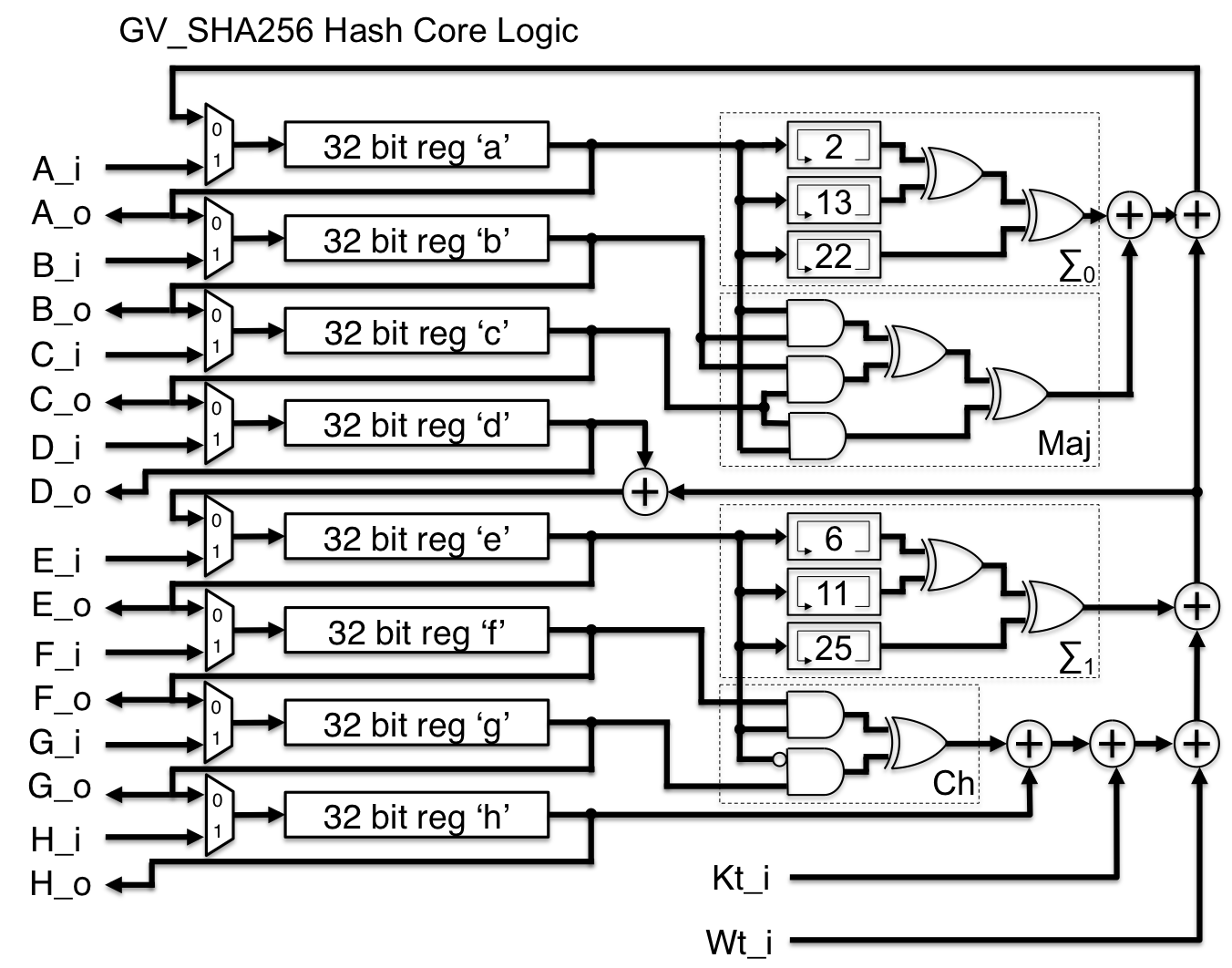
To generate SHA-1 and SHA-256 keys
Navigate to your project > Tasks > android. Double-click on signingReport. The SHA1 and SHA256 keys will be displayed in the Run tab at the bottom of the window.SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
How long does SHA-256 take to crack : SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …