Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.The HASHTYPE data type can be used to store hash values such as MD5 hashes or Universally Unique Identifiers (UUID). There is no special literal for the HASHTYPE data type. Values are defined as strings and must be delimited with single quotes.The primary goal of hashing is to ensure data integrity and validate the original data. Hash functions are intended to be fast and efficient, generating unique hash values for each input. Hashing is irreversible, which means it's computationally impractical to recover the original data from the hash value.
What can a hash tell you : A hash value is a numeric value of a fixed length that uniquely identifies data.
What is hash value and its types
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
When to use hashing : The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
In computing, a hash table, also known as a hash map or a hash set, is a data structure that implements an associative array, also called a dictionary, which is an abstract data type that maps keys to values. Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.
Can you reverse a hash
As hashing is extremely infeasible to reverse, hashing algorithms are used on passwords. This makes the password shorter and undiscoverable by attackers.Characteristics of a Good Hash Function. There are four main characteristics of a good hash function: 1) The hash value is fully determined by the data being hashed. 2) The hash function uses all the input data. 3) The hash function "uniformly" distributes the data across the entire set of possible hash values.Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Non-cryptographic hash functions
Name
Length
Type
Fast-Hash
32 or 64 bits
xorshift operations
SpookyHash
32, 64, or 128 bits
see Jenkins hash function
CityHash
32, 64, 128, or 256 bits
FarmHash
32, 64 or 128 bits
Why are there different hash types : Any piece of digital information, like a file on your computer, a photo on your smartphone, or a block on a cryptocurrency blockchain, has a hash. And each hash is unique to each piece of data – any small change in the underlying information will lead to a completely different hash.
Why do people use hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Can you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted. Hashing is implemented in two steps: An element is converted into an integer by using a hash function. This element can be used as an index to store the original element, which falls into the hash table. The element is stored in the hash table where it can be quickly retrieved using hashed key.While the hash produced is irreversible, it's not pre-image resistant! Given the hash value of 0, I can very easily produce any number of inputs that produce that hash: 2, 4, 6, 8, 10, etc.
What is a perfect hash : In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions. In mathematical terms, it is an injective function.
Antwort What is hash and its types? Weitere Antworten – What is hashing and types
Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.The HASHTYPE data type can be used to store hash values such as MD5 hashes or Universally Unique Identifiers (UUID). There is no special literal for the HASHTYPE data type. Values are defined as strings and must be delimited with single quotes.The primary goal of hashing is to ensure data integrity and validate the original data. Hash functions are intended to be fast and efficient, generating unique hash values for each input. Hashing is irreversible, which means it's computationally impractical to recover the original data from the hash value.
What can a hash tell you : A hash value is a numeric value of a fixed length that uniquely identifies data.
What is hash value and its types
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
When to use hashing : The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
In computing, a hash table, also known as a hash map or a hash set, is a data structure that implements an associative array, also called a dictionary, which is an abstract data type that maps keys to values.
:max_bytes(150000):strip_icc()/hash.asp-final-f341f429ebc1421ab167f2f97609b5eb.png)
Hash provides better synchronization than other data structures. Hash tables are more efficient than search trees or other data structures. Hash provides constant time for searching, insertion and deletion operations on average. Hash tables are space-efficient.
Can you reverse a hash
As hashing is extremely infeasible to reverse, hashing algorithms are used on passwords. This makes the password shorter and undiscoverable by attackers.Characteristics of a Good Hash Function. There are four main characteristics of a good hash function: 1) The hash value is fully determined by the data being hashed. 2) The hash function uses all the input data. 3) The hash function "uniformly" distributes the data across the entire set of possible hash values.Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.

Non-cryptographic hash functions
Why are there different hash types : Any piece of digital information, like a file on your computer, a photo on your smartphone, or a block on a cryptocurrency blockchain, has a hash. And each hash is unique to each piece of data – any small change in the underlying information will lead to a completely different hash.
Why do people use hashing : Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Can you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
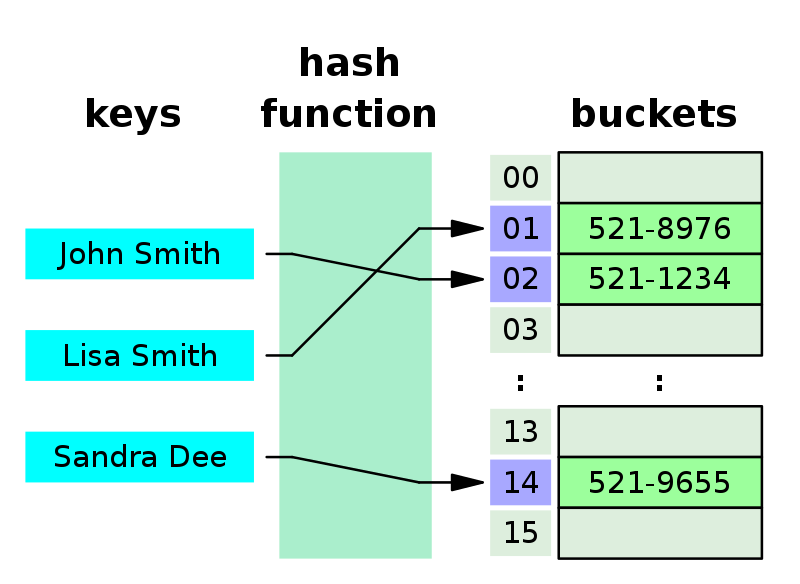
Hashing is implemented in two steps: An element is converted into an integer by using a hash function. This element can be used as an index to store the original element, which falls into the hash table. The element is stored in the hash table where it can be quickly retrieved using hashed key.While the hash produced is irreversible, it's not pre-image resistant! Given the hash value of 0, I can very easily produce any number of inputs that produce that hash: 2, 4, 6, 8, 10, etc.
What is a perfect hash : In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions. In mathematical terms, it is an injective function.