The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash. With recent computational advancements, it has become possible to decrypt SHA-256 hashes.SHA-256 stands for Secure Hash Algorithm 256-bit and it's used for cryptographic security. Cryptographic hash algorithms produce irreversible and unique hashes. The larger the number of possible hashes, the smaller the chance that two values will create the same hash.Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
What is the difference between 256 and 512 hash : The primary difference between SHA-256 and SHA-512 is the word size; SHA-256 uses 32-byte words whereas SHA-512 uses 64-byte words. There are also modified versions of each standard, known as SHA-224, SHA-384, SHA-512/224, and SHA-512/256.
What is SHA code
SHA is the acronym for Secure Hash Algorithm, used for hashing data and certificate files. Every piece of data produces a unique hash that is thoroughly non-duplicable by any other piece of data. The resulting digital signature is unique too as it depends on the hash that's generated out of the data.
How to generate SHA-256 code : We can use the sha256sum command in two modes, binary and text (the default). On Linux, both modes generate the same SHA-256 hash, so the default mode is used throughout this article. We're using the -n option to instruct echo not to output the trailing newline (\n).
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 refers to a cryptographic hash function that belongs to the SHA-2 (Secure Hash Algorithm 2) family. It generates a fixed-size 256-bit (32-byte) hash value from input data of arbitrary length. SHA-256 is widely used in cryptography and data integrity verification. There is a difference between hashing and encryption. SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Is SHA-256 unbreakable
Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.The reason why SHA-512 is faster than SHA-256 on 64-bit machines is that has 37.5% less rounds per byte (80 rounds operating on 128 byte blocks) compared to SHA- 256 (64 rounds operating on 64 byte blocks), where the operations use 64-bit integer arithmetic. SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.
What is SHA-256 Bitcoin : Secure Hash Algorithm 256-bit (SHA-256) is a widely used cryptographic hash function that produces a fixed-size output of 256 bits when given different inputs. It belongs to the SHA-2 family of hash functions, which was preceded by the earliest SHA-1 hash functions.
How to get sha-256 key : To generate SHA-1 and SHA-256 keys
Open your project in Android Studio.
Click on the Gradle tab located on the right side of the window.
Navigate to your project > Tasks > android.
Double-click on signingReport.
The SHA1 and SHA256 keys will be displayed in the Run tab at the bottom of the window.
What is an example of a SHA256 password
For example, the SHA256 hash of "12345" is "5994471abb01112afcc18159f6cc74b4f511b99806da59b3caf5a9c173cacfc5" . If this hash is seen in a database, we know that the user's password is "12345" 2. In fact, there is an entire database of precomputed hashes which can be checked against. These are called rainbow tables. 256-bit encryption is a data/file encryption technique that uses a 256-bit key to encrypt and decrypt data or files. It is one of the most secure encryption methods after 128- and 192-bit encryption, and is used in most modern encryption algorithms, protocols and technologies including AES and SSL.We can use the sha256sum command in two modes, binary and text (the default). On Linux, both modes generate the same SHA-256 hash, so the default mode is used throughout this article. We're using the -n option to instruct echo not to output the trailing newline (\n).
How to detect SHA-256 : How to find out a file's SHA-256 hash
Go to Devices and select Computers or Servers, depending on where the detection occurred.
Find the device on which the file has been detected and click the device name.
Antwort What is hash 256 code? Weitere Antworten – What is the SHA-256 code
The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash. With recent computational advancements, it has become possible to decrypt SHA-256 hashes.SHA-256 stands for Secure Hash Algorithm 256-bit and it's used for cryptographic security. Cryptographic hash algorithms produce irreversible and unique hashes. The larger the number of possible hashes, the smaller the chance that two values will create the same hash.Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
What is the difference between 256 and 512 hash : The primary difference between SHA-256 and SHA-512 is the word size; SHA-256 uses 32-byte words whereas SHA-512 uses 64-byte words. There are also modified versions of each standard, known as SHA-224, SHA-384, SHA-512/224, and SHA-512/256.
What is SHA code
SHA is the acronym for Secure Hash Algorithm, used for hashing data and certificate files. Every piece of data produces a unique hash that is thoroughly non-duplicable by any other piece of data. The resulting digital signature is unique too as it depends on the hash that's generated out of the data.
How to generate SHA-256 code : We can use the sha256sum command in two modes, binary and text (the default). On Linux, both modes generate the same SHA-256 hash, so the default mode is used throughout this article. We're using the -n option to instruct echo not to output the trailing newline (\n).
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 refers to a cryptographic hash function that belongs to the SHA-2 (Secure Hash Algorithm 2) family. It generates a fixed-size 256-bit (32-byte) hash value from input data of arbitrary length. SHA-256 is widely used in cryptography and data integrity verification.
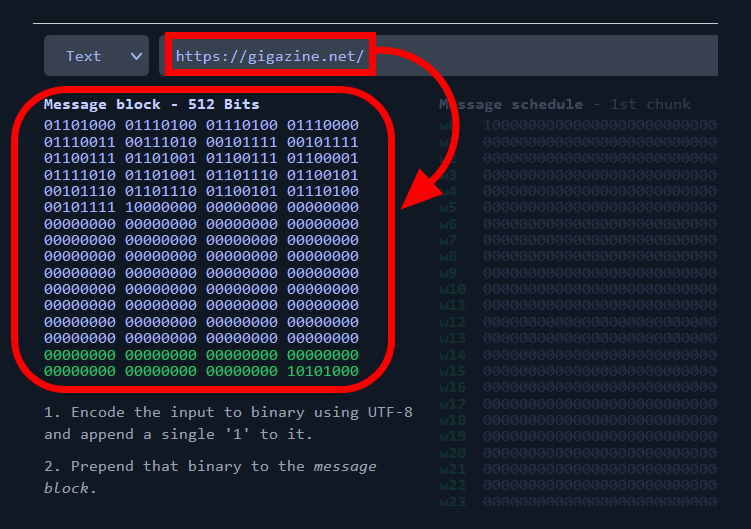
There is a difference between hashing and encryption. SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Is SHA-256 unbreakable
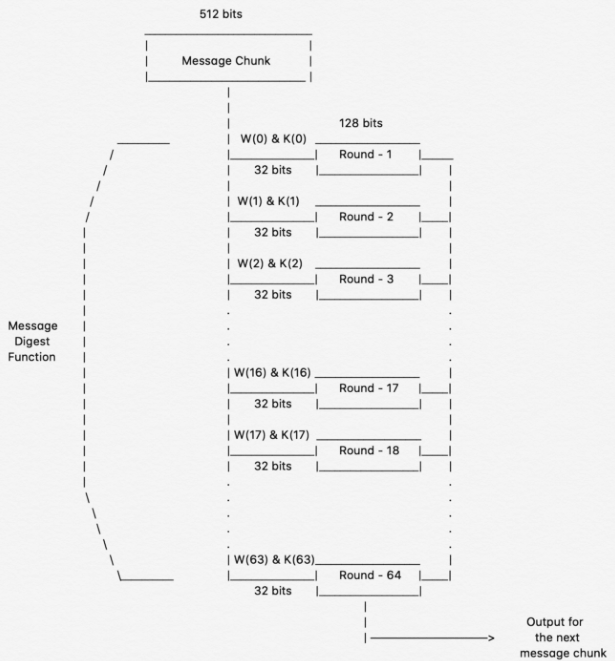
Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.The reason why SHA-512 is faster than SHA-256 on 64-bit machines is that has 37.5% less rounds per byte (80 rounds operating on 128 byte blocks) compared to SHA- 256 (64 rounds operating on 64 byte blocks), where the operations use 64-bit integer arithmetic.
SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.
What is SHA-256 Bitcoin : Secure Hash Algorithm 256-bit (SHA-256) is a widely used cryptographic hash function that produces a fixed-size output of 256 bits when given different inputs. It belongs to the SHA-2 family of hash functions, which was preceded by the earliest SHA-1 hash functions.
How to get sha-256 key : To generate SHA-1 and SHA-256 keys
What is an example of a SHA256 password
For example, the SHA256 hash of "12345" is "5994471abb01112afcc18159f6cc74b4f511b99806da59b3caf5a9c173cacfc5" . If this hash is seen in a database, we know that the user's password is "12345" 2. In fact, there is an entire database of precomputed hashes which can be checked against. These are called rainbow tables.
256-bit encryption is a data/file encryption technique that uses a 256-bit key to encrypt and decrypt data or files. It is one of the most secure encryption methods after 128- and 192-bit encryption, and is used in most modern encryption algorithms, protocols and technologies including AES and SSL.We can use the sha256sum command in two modes, binary and text (the default). On Linux, both modes generate the same SHA-256 hash, so the default mode is used throughout this article. We're using the -n option to instruct echo not to output the trailing newline (\n).
How to detect SHA-256 : How to find out a file's SHA-256 hash