Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use of hashing is for setting up hash tables.Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Hashing is not a type of encryption — it's a form of cryptographic security. Encryption works both ways, while hashing is a one-way function. Hashing boils down the original to a fixed set of characters. This is not the case with encrypted messages.
What is a hash key : a push button on a telephone or key on a computer keyboard that is marked with a hash mark (#); pound key ( def ). Computers. hash value.
What is a real life example of hashing
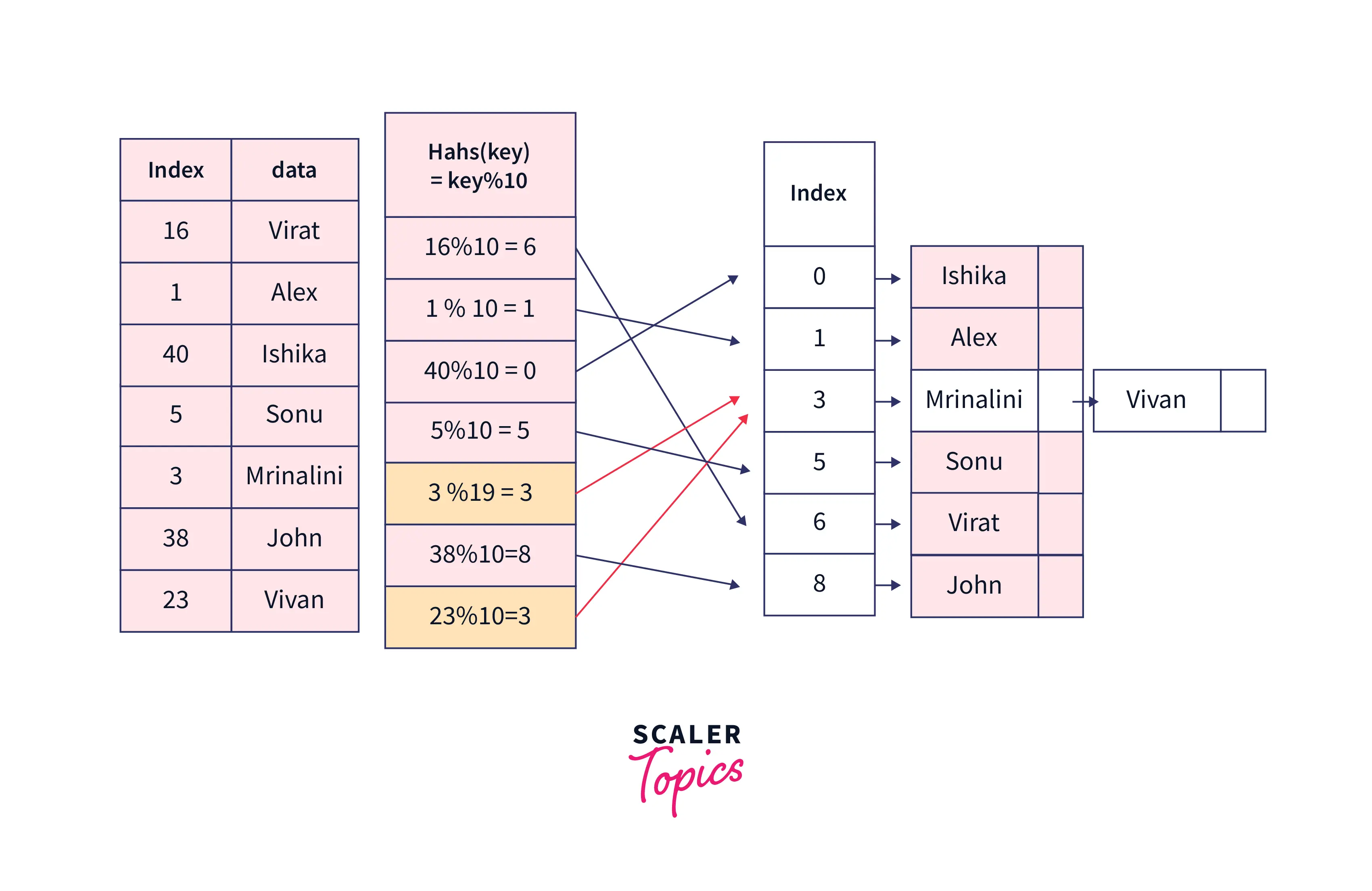
There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is an example of a hashing function : For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match. For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).
Are passwords hashed or encrypted
Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, NOT encrypted. Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation.For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.Hash can be soft and pliable or stiff and brittle. It may be red, black, brown, green, yellow, or blonde in color. Hash may also be used in cooking, as it is soluble in things like oils, butter, or cream and can therefore be made into foods like brownies. Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.
What is a good example of hash function : For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
What is an example of a simple hash : Here's a simple example: A hash of the string "Hello world!" is "Hel". If you're given "Hel", you cannot recreate "Hello world!", and yet it is likely not going to clash with many other strings.
What are two examples of the uses of hashing
Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching. For example, the input "password" might produce the hash "5f4dcc3b5aa765d61d8327deb882cf99", while the input "passw0rd" might produce the hash "6c569aabbf7775ef8fc5705a9f1f9b2f". Hashing is irreversible, meaning that you cannot recover the original input from the hash.How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.
What are the examples of hashing algorithms : Hashing algorithms are just as abundant as encryption algorithms, but there are a few that are used more often than others. Some common hashing algorithms include MD5, SHA-1, SHA-2, NTLM, and LANMAN.
Antwort What is an example of hashing? Weitere Antworten – What is meant by hashing
Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use of hashing is for setting up hash tables.Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Hashing is not a type of encryption — it's a form of cryptographic security. Encryption works both ways, while hashing is a one-way function. Hashing boils down the original to a fixed set of characters. This is not the case with encrypted messages.
What is a hash key : a push button on a telephone or key on a computer keyboard that is marked with a hash mark (#); pound key ( def ). Computers. hash value.
What is a real life example of hashing
There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is an example of a hashing function : For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.

For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).
Are passwords hashed or encrypted
Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, NOT encrypted. Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation.For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.Hash can be soft and pliable or stiff and brittle. It may be red, black, brown, green, yellow, or blonde in color. Hash may also be used in cooking, as it is soluble in things like oils, butter, or cream and can therefore be made into foods like brownies.

Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.
What is a good example of hash function : For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
What is an example of a simple hash : Here's a simple example: A hash of the string "Hello world!" is "Hel". If you're given "Hel", you cannot recreate "Hello world!", and yet it is likely not going to clash with many other strings.
What are two examples of the uses of hashing
Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.
For example, the input "password" might produce the hash "5f4dcc3b5aa765d61d8327deb882cf99", while the input "passw0rd" might produce the hash "6c569aabbf7775ef8fc5705a9f1f9b2f". Hashing is irreversible, meaning that you cannot recover the original input from the hash.How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.
What are the examples of hashing algorithms : Hashing algorithms are just as abundant as encryption algorithms, but there are a few that are used more often than others. Some common hashing algorithms include MD5, SHA-1, SHA-2, NTLM, and LANMAN.