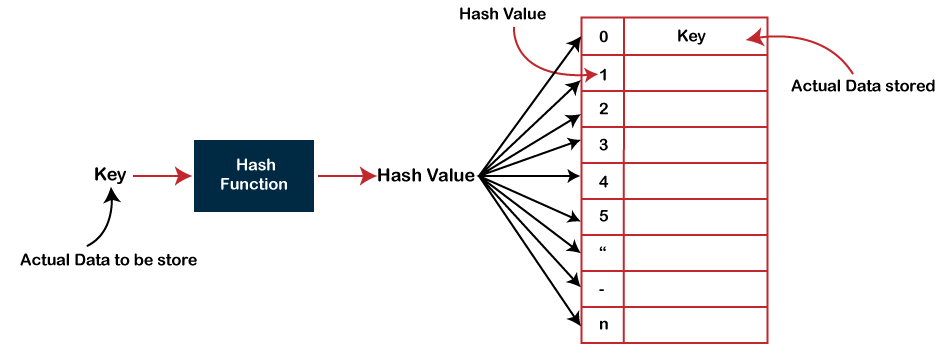
Hashing is a technique that is used to uniquely identify a specific object from a group of similar objects. Some examples of how hashing is used in our lives include: In universities, each student is assigned a unique roll number that can be used to retrieve information about them.Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.A hash table is a type of data structure in which information is stored in an easy-to-retrieve and efficient manner. In the key-value method, keys are assigned random indexes where their values are stored in an array. The index is the information of where exactly in the array the value is stored.
What are hashes used for : The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is a real life example of hashing
Database indexing: Hashing is used to index and retrieve data efficiently in databases and other data storage systems. Password storage: Hashing is used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password.
What is a real life example of a hash function : Password verification
To authenticate a user, the password presented by the user is hashed and compared with the stored hash. A password reset method is required when password hashing is performed; original passwords cannot be recalculated from the stored hash value.
Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data. For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
What is an example of a hash function in real life
Applications of Hashing Algorithms
Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity.
Signature generation and verification.
Password verification.
Proof-of-work.
File or data identifier.
To use the hash sign, we will write “=” in another cell, followed by the cell reference of the first value in our spill array. As soon as we select the last value of this spill array, Excel will automatically change the reference syntax to the cell reference and the # sign. Press enter.These functions are used in many applications, including cryptography, data integrity checking, data indexing, and data fingerprinting. For instance, in cryptography, hash functions are used to generate digital signatures, which can be used to verify the authenticity of a message or document. The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function. It is the fastest of all the . NET hashing algorithms, but it uses a smaller 128-bit hash value, making it the most vulnerable to attack over the long term.
Is hashed data readable : Hashing is a method of turning readable data into unique but unreadable data — this can be applied to PII to protect the values in a way that they can still be used to link datasets.
What is the most commonly used hash function : Commonly used hash functions:
SHA-1: SHA-1 is a 160-bit hash function that was widely used for digital signatures and other applications.
SHA-2: SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512.
What is the most popular hash functions
Commonly used hash functions:
SHA-1: SHA-1 is a 160-bit hash function that was widely used for digital signatures and other applications.
SHA-2: SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512.
How it works. You create a customer data file based on information shared by your customers. To keep your data secure, you can hash your customer data yourself using the SHA256 algorithm, or Google Ads will hash the data for you using the same SHA256 algorithm, which is the industry standard for one-way hashing.This function will create a hash value for each row of data. In the new column you created, type “=SHA256(cell)” where “cell” is the cell that contains the data you want to hash. For example, if your data is in column A and your first row of data is in row 2, the formula would be “=SHA256(A2)”.
What are the most common hashes : Common hashing algorithms include:
MD-5. This is one of the first algorithms to gain widespread approval.
RIPEMD-160. The RACE Integrity Primitives Evaluation Message Digest (or RIPEMD-160) was developed in Belgium in the mid-1990s.
SHA. Algorithms in the SHA family are considered slightly more secure.
Antwort What is an example of hashed data? Weitere Antworten – What is an example of hashing
Hashing is a technique that is used to uniquely identify a specific object from a group of similar objects. Some examples of how hashing is used in our lives include: In universities, each student is assigned a unique roll number that can be used to retrieve information about them.Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.A hash table is a type of data structure in which information is stored in an easy-to-retrieve and efficient manner. In the key-value method, keys are assigned random indexes where their values are stored in an array. The index is the information of where exactly in the array the value is stored.
What are hashes used for : The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is a real life example of hashing
Database indexing: Hashing is used to index and retrieve data efficiently in databases and other data storage systems. Password storage: Hashing is used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password.
What is a real life example of a hash function : Password verification
To authenticate a user, the password presented by the user is hashed and compared with the stored hash. A password reset method is required when password hashing is performed; original passwords cannot be recalculated from the stored hash value.
Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
For example, if the input is 123,456,789 and the hash table size 10,000, squaring the key produces 15,241,578,750,190,521, so the hash code is taken as the middle 4 digits of the 17-digit number (ignoring the high digit) 8750.
What is an example of a hash function in real life
Applications of Hashing Algorithms
To use the hash sign, we will write “=” in another cell, followed by the cell reference of the first value in our spill array. As soon as we select the last value of this spill array, Excel will automatically change the reference syntax to the cell reference and the # sign. Press enter.These functions are used in many applications, including cryptography, data integrity checking, data indexing, and data fingerprinting. For instance, in cryptography, hash functions are used to generate digital signatures, which can be used to verify the authenticity of a message or document.
:max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png)
The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function. It is the fastest of all the . NET hashing algorithms, but it uses a smaller 128-bit hash value, making it the most vulnerable to attack over the long term.
Is hashed data readable : Hashing is a method of turning readable data into unique but unreadable data — this can be applied to PII to protect the values in a way that they can still be used to link datasets.
What is the most commonly used hash function : Commonly used hash functions:
What is the most popular hash functions
Commonly used hash functions:
How it works. You create a customer data file based on information shared by your customers. To keep your data secure, you can hash your customer data yourself using the SHA256 algorithm, or Google Ads will hash the data for you using the same SHA256 algorithm, which is the industry standard for one-way hashing.This function will create a hash value for each row of data. In the new column you created, type “=SHA256(cell)” where “cell” is the cell that contains the data you want to hash. For example, if your data is in column A and your first row of data is in row 2, the formula would be “=SHA256(A2)”.
What are the most common hashes : Common hashing algorithms include: