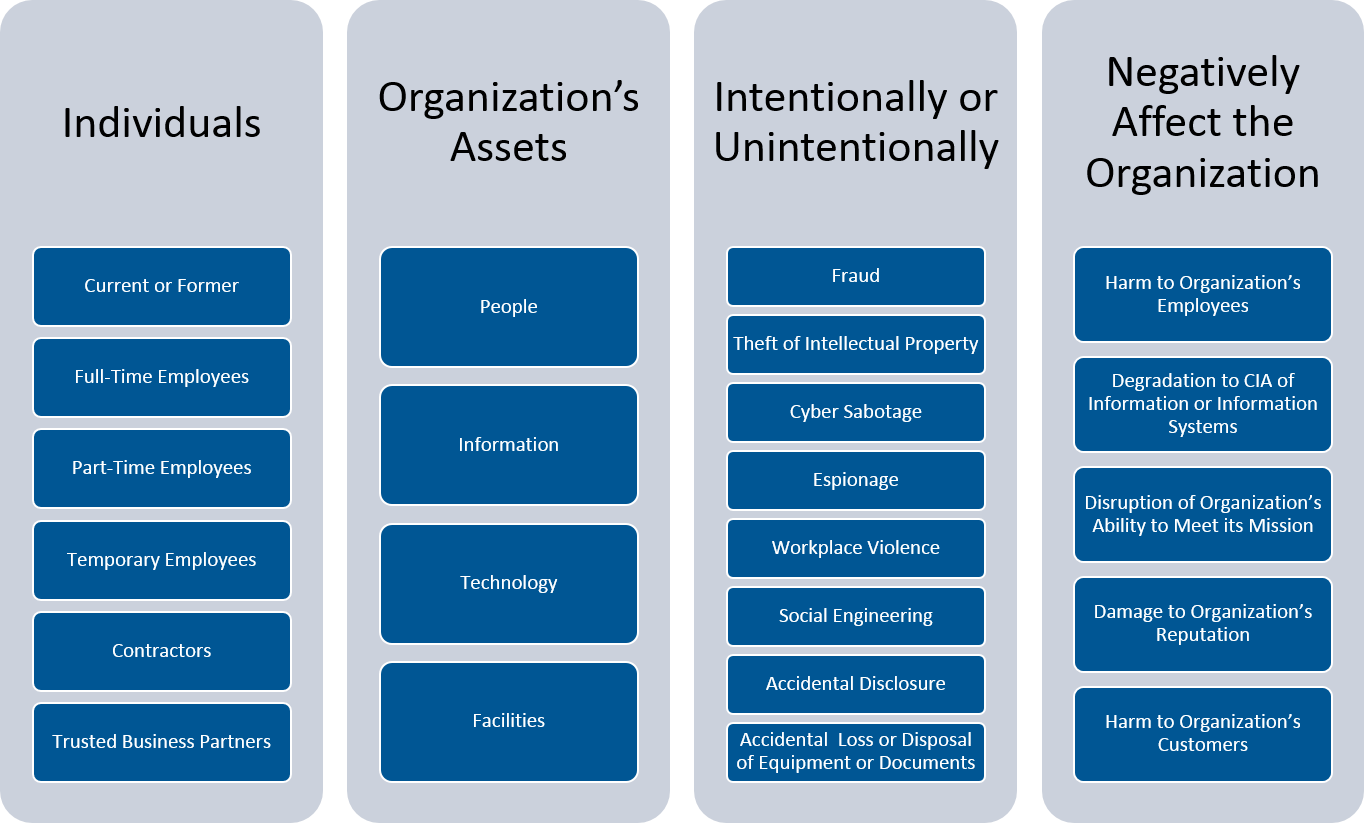
Insider threats manifest in various ways: violence, espionage, sabotage, theft, and cyber acts. Expressions of insider threat are defined in detail below. Violence – This action includes the threat of violence, as well as other threatening behaviors that create an intimidating, hostile, or abusive environment.Insider threats can be unintentional or malicious, depending on the threat's intent. Unintentional insider threats can arise from a negligent employee falling victim to a phishing attack. Examples of malicious threats include intentional data theft, corporate espionage, or data destruction.The CISA defines two types of insider threats: intentional and unintentional. They can both cause significant harm to a network despite their differences in intent and execution.
What is an example of computer sabotage : With regard to computers, sabotage is the deliberate damage to equipment. Infecting a website with malware is an example of information sabotage. A more extreme example is causing the power grid in a nation to go down. See cyberattack.
What is illegal sabotage
(a) Whoever, with intent to injure, interfere with, or obstruct the national defense of the United States, willfully injures, destroys, contaminates or infects, or attempts to so injure, destroy, contaminate or infect any national-defense material, national-defense premises, or national-defense utilities, shall be …
What are the three types of sabotages : Research indicates that there are three dimensions to sabotage activities: the forms – destruction, inaction and wastage; the overt and covert styles (modes of operation) used in their expressions; and, the motives for their occurrence and meanings attributed to them.
Threats can be classified in four categories: direct, indirect, veiled, or conditional. SABOTAGE: Sabotage of computers results in destruction or damage of computer hardware. This type of computer crime often resembles traditional sabotage because the computer itself is not used to carry out the destruction.
What are the types of threats
Threats can be classified into four different categories; direct, indirect, veiled, conditional. A direct threat identifies a specific target and is delivered in a straightforward, clear, and explicit manner.6 Most Common Insider Threats
Excessive Privileged Access. One of the most common and easily preventable risks is granting employees privileges that go beyond their job role.
Privilege Abuse.
SQL Injection.
Weak Audit Trail.
Database Inconsistences.
Phishing Attacks.
How BSC Can Help.
Sabotage is defined as deliberate and malicious acts that result in the disruption of the normal processes and functions or the destruction or damage of equipment or information. Computer crimes can be classified into four broad categories: sabotage, theft of services, property crimes, and financial crimes. This section examines each of these categories and gives examples drawn from actual crimes. SABOTAGE: Sabotage of computers results in destruction or damage of computer hardware.
Is sabotaging a war crime : Although sabotage is not prohibited by international law, captured saboteurs face severe consequences under both international law and domestic criminal codes. Spies and saboteurs are not entitled to POW status if they are captured gathering intelligence or conducting attacks out of uniform.
What is a person that sabotages : One who engages in sabotage is a saboteur. Saboteurs typically try to conceal their identities because of the consequences of their actions and to avoid invoking legal and organizational requirements for addressing sabotage.
How do you identify sabotage
It can manifest in a number of different ways depending on your circumstances, but some common signs of self-sabotage include chronic lateness, need for immediate gratification, repeating unhealthy patterns, isolation, substance abuse and other unhealthy coping mechanisms, low self-esteem and negative self-talk, poor … There are essentially seven issues associated human security. These are economic security, food security, health security environmental security, personal security, community security, and political security.A veiled threat is a threat that isn't directly stated but is implied using disguised language or euphemisms, as in My brother didn't say so directly, but he made a veiled threat implying that I'd be in big trouble if I so much as scratch the paint on his car.
Is malware computer sabotage : Malware, short for malicious software, refers to any intrusive software developed by cybercriminals (often called hackers) to steal data and damage or destroy computers and computer systems. Examples of common malware include viruses, worms, Trojan viruses, spyware, adware, and ransomware.
Antwort What is a sabotage threat? Weitere Antworten – Is sabotage a threat
Insider threats manifest in various ways: violence, espionage, sabotage, theft, and cyber acts. Expressions of insider threat are defined in detail below. Violence – This action includes the threat of violence, as well as other threatening behaviors that create an intimidating, hostile, or abusive environment.Insider threats can be unintentional or malicious, depending on the threat's intent. Unintentional insider threats can arise from a negligent employee falling victim to a phishing attack. Examples of malicious threats include intentional data theft, corporate espionage, or data destruction.The CISA defines two types of insider threats: intentional and unintentional. They can both cause significant harm to a network despite their differences in intent and execution.
What is an example of computer sabotage : With regard to computers, sabotage is the deliberate damage to equipment. Infecting a website with malware is an example of information sabotage. A more extreme example is causing the power grid in a nation to go down. See cyberattack.
What is illegal sabotage
(a) Whoever, with intent to injure, interfere with, or obstruct the national defense of the United States, willfully injures, destroys, contaminates or infects, or attempts to so injure, destroy, contaminate or infect any national-defense material, national-defense premises, or national-defense utilities, shall be …
What are the three types of sabotages : Research indicates that there are three dimensions to sabotage activities: the forms – destruction, inaction and wastage; the overt and covert styles (modes of operation) used in their expressions; and, the motives for their occurrence and meanings attributed to them.
Threats can be classified in four categories: direct, indirect, veiled, or conditional.

SABOTAGE: Sabotage of computers results in destruction or damage of computer hardware. This type of computer crime often resembles traditional sabotage because the computer itself is not used to carry out the destruction.
What are the types of threats
Threats can be classified into four different categories; direct, indirect, veiled, conditional. A direct threat identifies a specific target and is delivered in a straightforward, clear, and explicit manner.6 Most Common Insider Threats
Sabotage is defined as deliberate and malicious acts that result in the disruption of the normal processes and functions or the destruction or damage of equipment or information.

Computer crimes can be classified into four broad categories: sabotage, theft of services, property crimes, and financial crimes. This section examines each of these categories and gives examples drawn from actual crimes. SABOTAGE: Sabotage of computers results in destruction or damage of computer hardware.
Is sabotaging a war crime : Although sabotage is not prohibited by international law, captured saboteurs face severe consequences under both international law and domestic criminal codes. Spies and saboteurs are not entitled to POW status if they are captured gathering intelligence or conducting attacks out of uniform.
What is a person that sabotages : One who engages in sabotage is a saboteur. Saboteurs typically try to conceal their identities because of the consequences of their actions and to avoid invoking legal and organizational requirements for addressing sabotage.
How do you identify sabotage
It can manifest in a number of different ways depending on your circumstances, but some common signs of self-sabotage include chronic lateness, need for immediate gratification, repeating unhealthy patterns, isolation, substance abuse and other unhealthy coping mechanisms, low self-esteem and negative self-talk, poor …
There are essentially seven issues associated human security. These are economic security, food security, health security environmental security, personal security, community security, and political security.A veiled threat is a threat that isn't directly stated but is implied using disguised language or euphemisms, as in My brother didn't say so directly, but he made a veiled threat implying that I'd be in big trouble if I so much as scratch the paint on his car.
Is malware computer sabotage : Malware, short for malicious software, refers to any intrusive software developed by cybercriminals (often called hackers) to steal data and damage or destroy computers and computer systems. Examples of common malware include viruses, worms, Trojan viruses, spyware, adware, and ransomware.