Hashed File stages represent a hashed file, that is, a file that uses a hashing algorithm for distributing records in one or more groups on disk. Use a Hashed File stage to access UniVerse files. The server engine can host UniVerse files locally.HashMyFiles.exe is a lightweight and portable utility developed by Nir Sofer that allows users to calculate the hash value of files in their computer. This tool supports multiple hash algorithms, including MD5, SHA1, SHA256, and CRC32, and provides a simple interface for users to select files or folders to analyze.You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
Why check the hash of a file : Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
What is the file hash or MD5
MD5 (message-digest algorithm) is a cryptographic protocol used for authenticating messages as well as content verification and digital signatures. MD5 is based on a hash function that verifies that a file you sent matches the file received by the person you sent it to.
Are hash files encrypted : Basically, encryption is the process of scrambling plaintext into unreadable ciphertext, which you can decrypt with a relevant key, while hashing turns plain text into a unique code, which can't be reverted into a readable form.
Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. The most common hash functions used in digital forensics are Message Digest 5 (MD5), and Secure Hashing Algorithm (SHA) 1 and 2.
How to get sha256 for a file
SHA-256 checksum tool is called sha256sum.
Go to the directory where your downloaded file is stored, e.g.: cd home/downloads.
Use the following command to generate the checksum: sha256sum my_file.exe.
Compare the generated value to the checksum of the file in Rublon Downloads.
Description. HashMyFiles is small utility that allows you to calculate the MD5 and SHA1 hashes of one or more files in your system. You can easily copy the MD5/SHA1 hashes list into the clipboard, or save them into text/html/xml file.In practice, yes. A hash code (MD5, SHA-1, SHA-256) is of a fixed length, so it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the likelihood of a collision (two distinct files with the same hash value). An MD5 checksum is a mathematical algorithm is usually a set of 32-character hexadecimal letters and numbers that are computed on a file with a tool. These numbers are generated using special tools that employ “cryptographic hash function producing a 128-bit (16-byte) hash value”.
What is MD5 vs SHA-256 : MD5 produces a 128-bit output, and SHA256 produces a 256-bit output. Generally, the longer the output, the more secure the hash function, as it reduces the chances of collisions (two different inputs producing the same output).
Which is better MD5 or SHA-256 file hash : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
Can you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted. Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.A hash is a mathematical function that converts an input of arbitrary length into an encrypted output of a fixed length. Thus, regardless of the original amount of data or file size involved, its unique hash will always be the same size.
When would you use a hash : Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
Antwort What is a file hash? Weitere Antworten – What is a hashed file
Hashed File stages represent a hashed file, that is, a file that uses a hashing algorithm for distributing records in one or more groups on disk. Use a Hashed File stage to access UniVerse files. The server engine can host UniVerse files locally.HashMyFiles.exe is a lightweight and portable utility developed by Nir Sofer that allows users to calculate the hash value of files in their computer. This tool supports multiple hash algorithms, including MD5, SHA1, SHA256, and CRC32, and provides a simple interface for users to select files or folders to analyze.You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Why check the hash of a file : Hashes are a fundamental tool in computer security as they can reliably tell us when two files are identical, so long as we use secure hashing algorithms that avoid collisions.
What is the file hash or MD5
MD5 (message-digest algorithm) is a cryptographic protocol used for authenticating messages as well as content verification and digital signatures. MD5 is based on a hash function that verifies that a file you sent matches the file received by the person you sent it to.
Are hash files encrypted : Basically, encryption is the process of scrambling plaintext into unreadable ciphertext, which you can decrypt with a relevant key, while hashing turns plain text into a unique code, which can't be reverted into a readable form.
Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.

The most common hash functions used in digital forensics are Message Digest 5 (MD5), and Secure Hashing Algorithm (SHA) 1 and 2.
How to get sha256 for a file
SHA-256 checksum tool is called sha256sum.
Description. HashMyFiles is small utility that allows you to calculate the MD5 and SHA1 hashes of one or more files in your system. You can easily copy the MD5/SHA1 hashes list into the clipboard, or save them into text/html/xml file.In practice, yes. A hash code (MD5, SHA-1, SHA-256) is of a fixed length, so it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the likelihood of a collision (two distinct files with the same hash value).
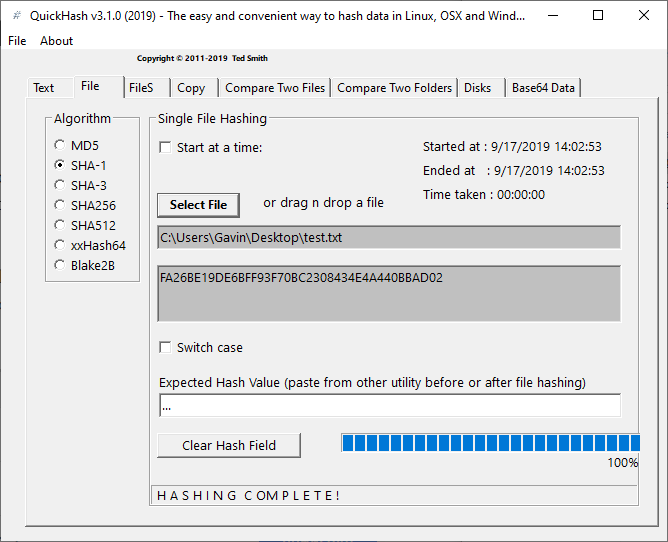
An MD5 checksum is a mathematical algorithm is usually a set of 32-character hexadecimal letters and numbers that are computed on a file with a tool. These numbers are generated using special tools that employ “cryptographic hash function producing a 128-bit (16-byte) hash value”.
What is MD5 vs SHA-256 : MD5 produces a 128-bit output, and SHA256 produces a 256-bit output. Generally, the longer the output, the more secure the hash function, as it reduces the chances of collisions (two different inputs producing the same output).
Which is better MD5 or SHA-256 file hash : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
Can you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.A hash is a mathematical function that converts an input of arbitrary length into an encrypted output of a fixed length. Thus, regardless of the original amount of data or file size involved, its unique hash will always be the same size.
When would you use a hash : Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.