Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.A hash is a mathematical function that converts an input of arbitrary length into an encrypted output of a fixed length. Thus, regardless of the original amount of data or file size involved, its unique hash will always be the same size.Hashing in the data structure is a technique that is used to quickly identify a specific value within a given array. It works by creating a unique hash code for each element in the array and then stores the hash code in lieu of the actual element.
Why is hash used : The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is meant by hash value
A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value.
Why are files hashed : Hashing has a large number of applications in cybersecurity, centering around the ability to verify that data is legitimate. With a secure hashing algorithm, one could verify that a downloaded file matched what was expected. In fact, many projects provide hashes alongside their downloads.
A hash value is a numeric value of a fixed length that uniquely identifies data. A hash function is any function that can be used to map data of arbitrary size to fixed-size values, though there are some hash functions that support variable length output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes.
What is an example of hashing
Hashing is a technique that is used to uniquely identify a specific object from a group of similar objects. Some examples of how hashing is used in our lives include: In universities, each student is assigned a unique roll number that can be used to retrieve information about them.A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.
What does hash my files do : HashMyFiles.exe is a lightweight and portable utility developed by Nir Sofer that allows users to calculate the hash value of files in their computer. This tool supports multiple hash algorithms, including MD5, SHA1, SHA256, and CRC32, and provides a simple interface for users to select files or folders to analyze.
Why is hashing not safe : Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible.
What hash represents
A hash is supposed to be a unique combination of values from 00 to FF (hexadecimal) that represents a certain piece of data, be it a file or a string of bytes. Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.
Is hashing still used : Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common.
Antwort What does hash mean in data? Weitere Antworten – What is a data hash
Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.A hash is a mathematical function that converts an input of arbitrary length into an encrypted output of a fixed length. Thus, regardless of the original amount of data or file size involved, its unique hash will always be the same size.Hashing in the data structure is a technique that is used to quickly identify a specific value within a given array. It works by creating a unique hash code for each element in the array and then stores the hash code in lieu of the actual element.
Why is hash used : The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
What is meant by hash value
A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value.
Why are files hashed : Hashing has a large number of applications in cybersecurity, centering around the ability to verify that data is legitimate. With a secure hashing algorithm, one could verify that a downloaded file matched what was expected. In fact, many projects provide hashes alongside their downloads.
A hash value is a numeric value of a fixed length that uniquely identifies data.

A hash function is any function that can be used to map data of arbitrary size to fixed-size values, though there are some hash functions that support variable length output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes.
What is an example of hashing
Hashing is a technique that is used to uniquely identify a specific object from a group of similar objects. Some examples of how hashing is used in our lives include: In universities, each student is assigned a unique roll number that can be used to retrieve information about them.A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
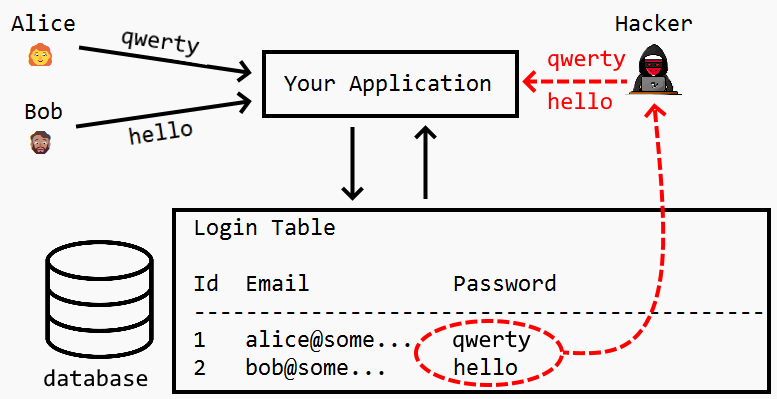
Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.
What does hash my files do : HashMyFiles.exe is a lightweight and portable utility developed by Nir Sofer that allows users to calculate the hash value of files in their computer. This tool supports multiple hash algorithms, including MD5, SHA1, SHA256, and CRC32, and provides a simple interface for users to select files or folders to analyze.
Why is hashing not safe : Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible.
What hash represents
A hash is supposed to be a unique combination of values from 00 to FF (hexadecimal) that represents a certain piece of data, be it a file or a string of bytes.
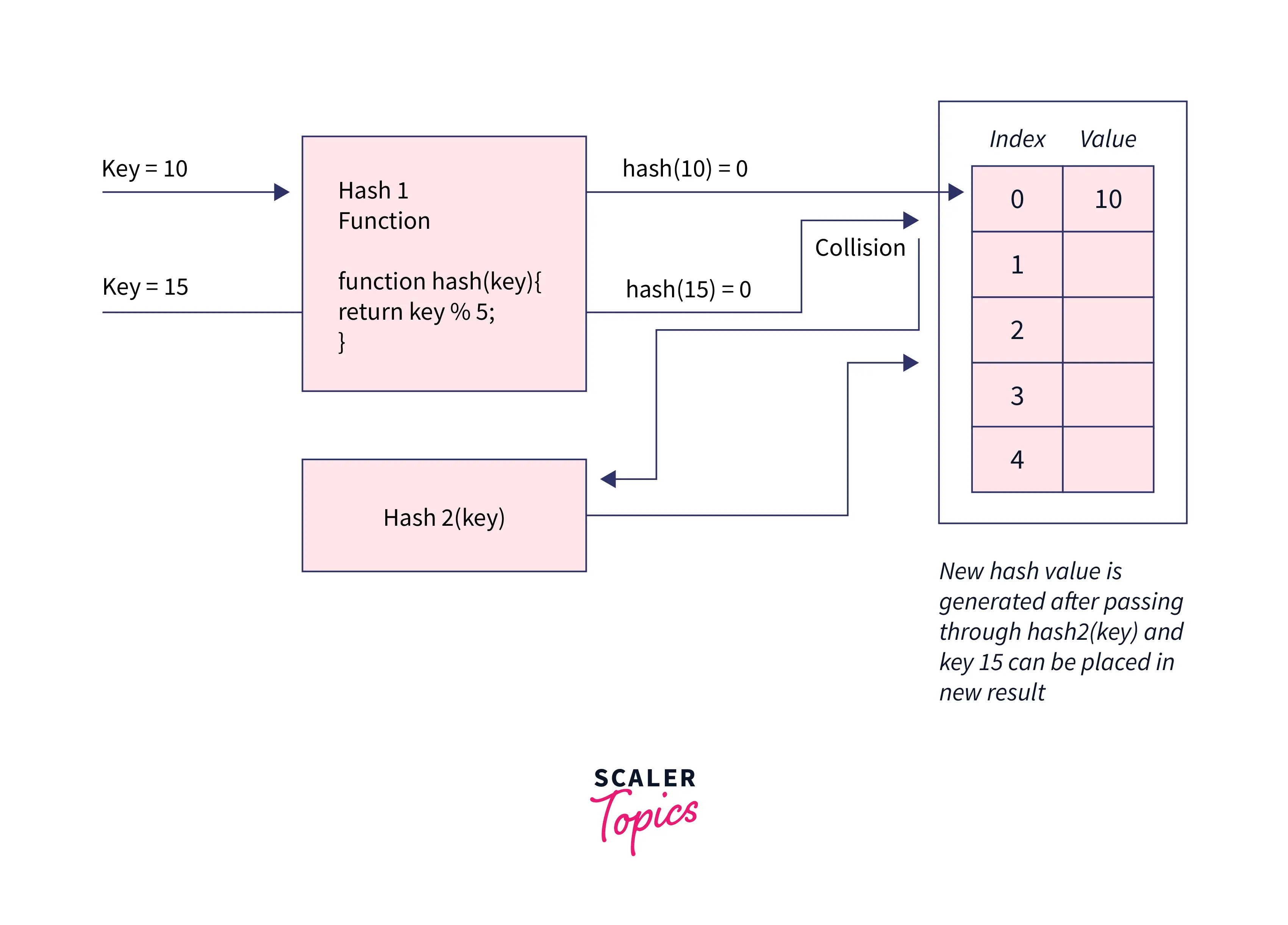
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.
Is hashing still used : Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common.