Secure Hash Algorithm 256-bit (SHA-256) is a widely used cryptographic hash function that produces a fixed-size output of 256 bits when given different inputs. It belongs to the SHA-2 family of hash functions, which was preceded by the earliest SHA-1 hash functions.Government’s National Security Agency (NSA)
Originally published in 2001, SHA-256 was developed by the US Government's National Security Agency (NSA). What is SHA-256 used for This algorithm is commonly used in SSL certificates for websites and in the DKIM message signing standard for email clients.SHA-256 refers to the bit size of the hash output. In other words, the resulting hash value from SHA-256 is 256 bits long, which provides a significantly larger search space compared to its predecessor, making it computationally infeasible to reverse engineer the original input from the hash value.
Is SHA-256 safe : On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
What does SHA-256 stand for
Secure Hash Algorithm 256-bit
SHA-256 stands for Secure Hash Algorithm 256-bit and it's used for cryptographic security. Cryptographic hash algorithms produce irreversible and unique hashes. The larger the number of possible hashes, the smaller the chance that two values will create the same hash.
Is SHA-256 unique : Since it produces only 2256 numbers simply if you try more than so many inputs that produce a different result you will certainly get the same SHA256. This makes it non unique.
Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash. The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. Currently, SHA-2 hashing is widely used, as it is considered the most secure hashing algorithm in the cryptographic arena.
Can SHA-256 be hacked
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.SHA256 provides better security and is the recommended hash function for these use cases. If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one. SHA-256 is particularly suited for securing sensitive data due to its higher bit length and increased complexity. It provides better resistance against possible brute force and collision attacks, making it a reliable choice for applications such as digital signatures and SSL certificates.
Is SHA-256 bad : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
What is the point of SHA-256 : The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.
Is SHA-256 secure in 2024
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1. Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
Is SHA-256 still safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
Antwort What does 256 mean in SHA? Weitere Antworten – What is SHA-256 Bitcoin
Secure Hash Algorithm 256-bit (SHA-256) is a widely used cryptographic hash function that produces a fixed-size output of 256 bits when given different inputs. It belongs to the SHA-2 family of hash functions, which was preceded by the earliest SHA-1 hash functions.Government’s National Security Agency (NSA)
Originally published in 2001, SHA-256 was developed by the US Government's National Security Agency (NSA). What is SHA-256 used for This algorithm is commonly used in SSL certificates for websites and in the DKIM message signing standard for email clients.SHA-256 refers to the bit size of the hash output. In other words, the resulting hash value from SHA-256 is 256 bits long, which provides a significantly larger search space compared to its predecessor, making it computationally infeasible to reverse engineer the original input from the hash value.
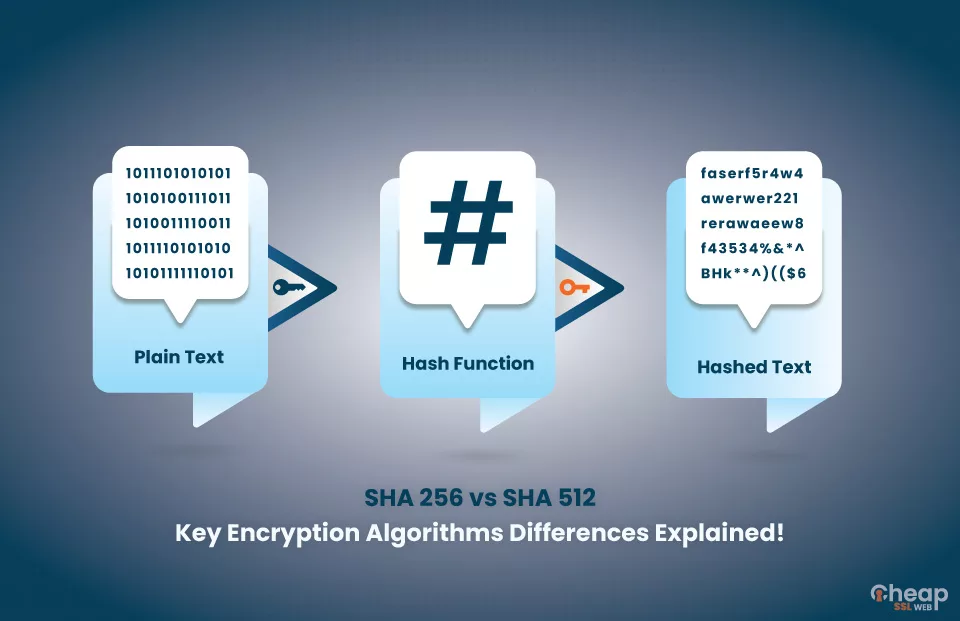
Is SHA-256 safe : On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
What does SHA-256 stand for
Secure Hash Algorithm 256-bit
SHA-256 stands for Secure Hash Algorithm 256-bit and it's used for cryptographic security. Cryptographic hash algorithms produce irreversible and unique hashes. The larger the number of possible hashes, the smaller the chance that two values will create the same hash.
Is SHA-256 unique : Since it produces only 2256 numbers simply if you try more than so many inputs that produce a different result you will certainly get the same SHA256. This makes it non unique.
Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. Currently, SHA-2 hashing is widely used, as it is considered the most secure hashing algorithm in the cryptographic arena.
Can SHA-256 be hacked
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.SHA256 provides better security and is the recommended hash function for these use cases. If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one.
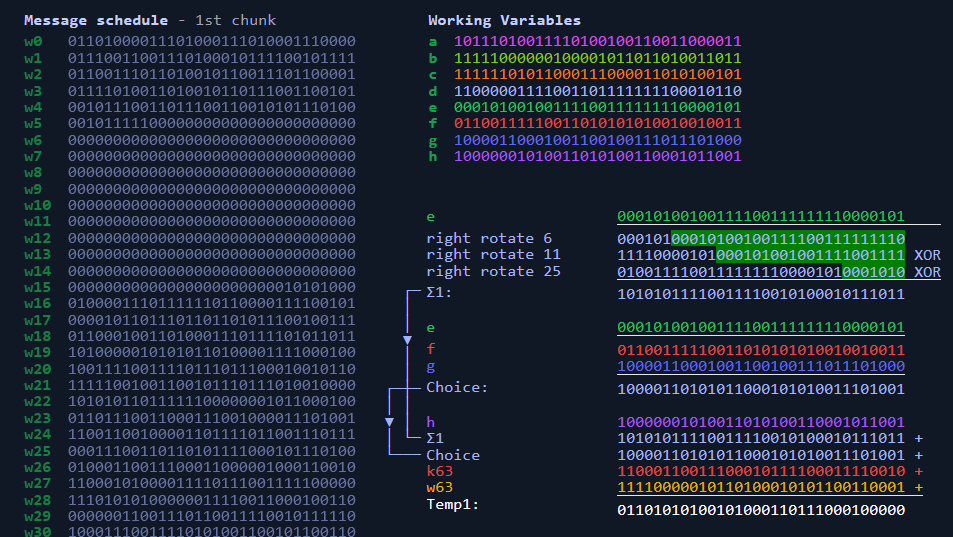
SHA-256 is particularly suited for securing sensitive data due to its higher bit length and increased complexity. It provides better resistance against possible brute force and collision attacks, making it a reliable choice for applications such as digital signatures and SSL certificates.
Is SHA-256 bad : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
What is the point of SHA-256 : The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.
Is SHA-256 secure in 2024
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.
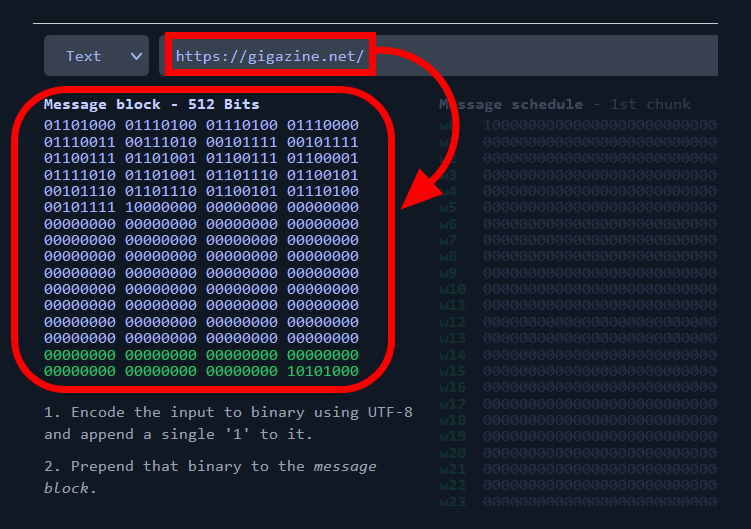
Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
Is SHA-256 still safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.