$1$ is the prefix used to identify md5-crypt hashes, following the Modular Crypt Format. salt is 0-8 characters drawn from the regexp range [./0-9A-Za-z] ; providing a 48-bit salt ( 5pZSV9va in the example).The MD5 (message-digest algorithm) hashing algorithm is a one-way cryptographic function that accepts a message of any length as input and returns as output a fixed-length digest value to be used for authenticating the original message.bcrypt
$2a$ : The hash algorithm identifier (bcrypt) 12 : Input cost (212 i.e. 4096 rounds) R9h/cIPz0gi.URNNX3kh2O : A base-64 encoding of the input salt.
What hash type is $5 : SHA-256
$5$ is 256-bit Secure Hash Algorithm (SHA-256)
Is MD5 safe
Vulnerabilities: The MD5 algorithm has long been considered insecure for cryptographic purposes due to significant vulnerabilities. Researchers have demonstrated practical collision attacks against MD5, which allows for the creation of different inputs that produce the same hash value.
What is SHA1 hash value : In cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits.
$2y is the hash algorithm (Blowfish in this case) $10 is the cost (or complexity/time) XElWz9WPwSLK3y0jUP6KhO is the salt (always 22 characters) bcrypt
$2b — this indicates that the hash is generated according to the OpenBSD implementation of bcrypt. 10$ — this is the "cost" parameter, indicating that the password is hashed with 210 (i.e. 1024) iterations of the blowfish cipher.
What is a hash starting with $2 Y $10
$2y is the hash algorithm (Blowfish in this case) $10 is the cost (or complexity/time) XElWz9WPwSLK3y0jUP6KhO is the salt (always 22 characters)SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.In December 2008, a group of researchers used this technique to fake SSL certificate validity. As of 2010, the CMU Software Engineering Institute considers MD5 "cryptographically broken and unsuitable for further use", and most U.S. government applications now require the SHA-2 family of hash functions. 1 HASH = 0.0003362 USD.
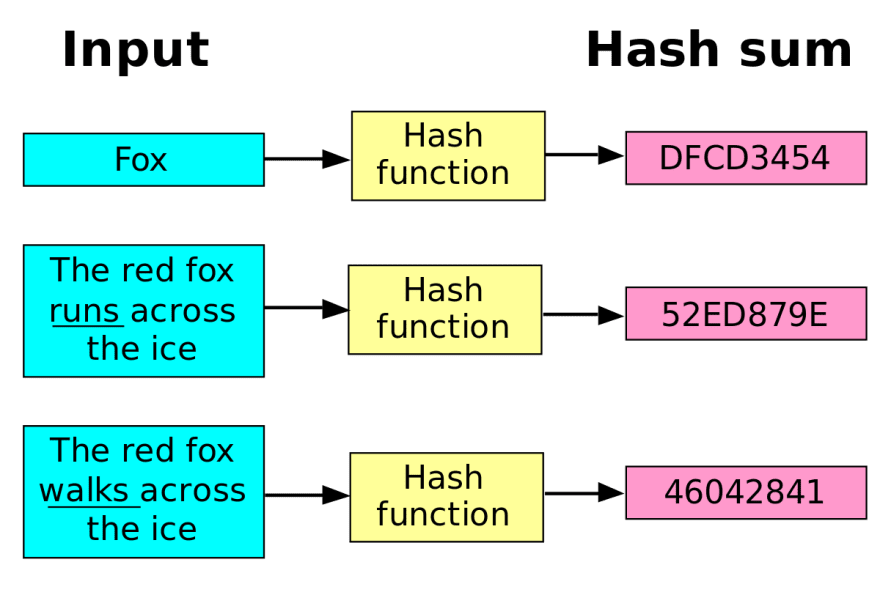
What is a hashed value : A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures.
What hash is $2 a : bcrypt
$2a$ : The hash algorithm identifier (bcrypt) 12 : Input cost (212 i.e. 4096 rounds) R9h/cIPz0gi.URNNX3kh2O : A base-64 encoding of the input salt.
What hash starts with $2$
bcrypt
$2a$ : The hash algorithm identifier (bcrypt) 12 : Input cost (212 i.e. 4096 rounds) R9h/cIPz0gi.URNNX3kh2O : A base-64 encoding of the input salt. PST9/PgBkqquzi.Ss7KIUgO2t0jWMUW : A base-64 encoding of the first 23 bytes of the computed 24 byte hash. xxHash is an extremely fast hashing algorithm that is not designed for cryptographic purposes, but provides excellent randomness and dispersion of output, and uniqueness of to minimize collisions.A hashrate is a measure of how many calculations can be performed per second and can be measured in billions, trillions, quadrillions, and quintillions. For example, a hashrate of 1TH/s means one trillion calculations can be performed every second. These calculations are being measured based on mining.
Antwort What does $1$ mean in hash? Weitere Antworten – What is the $1$ hash type
md5-crypt hashes
$1$ is the prefix used to identify md5-crypt hashes, following the Modular Crypt Format. salt is 0-8 characters drawn from the regexp range [./0-9A-Za-z] ; providing a 48-bit salt ( 5pZSV9va in the example).The MD5 (message-digest algorithm) hashing algorithm is a one-way cryptographic function that accepts a message of any length as input and returns as output a fixed-length digest value to be used for authenticating the original message.bcrypt
$2a$ : The hash algorithm identifier (bcrypt) 12 : Input cost (212 i.e. 4096 rounds) R9h/cIPz0gi.URNNX3kh2O : A base-64 encoding of the input salt.
What hash type is $5 : SHA-256
$5$ is 256-bit Secure Hash Algorithm (SHA-256)
Is MD5 safe
Vulnerabilities: The MD5 algorithm has long been considered insecure for cryptographic purposes due to significant vulnerabilities. Researchers have demonstrated practical collision attacks against MD5, which allows for the creation of different inputs that produce the same hash value.
What is SHA1 hash value : In cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits.
$2y is the hash algorithm (Blowfish in this case) $10 is the cost (or complexity/time) XElWz9WPwSLK3y0jUP6KhO is the salt (always 22 characters)
bcrypt
$2b — this indicates that the hash is generated according to the OpenBSD implementation of bcrypt. 10$ — this is the "cost" parameter, indicating that the password is hashed with 210 (i.e. 1024) iterations of the blowfish cipher.
What is a hash starting with $2 Y $10
$2y is the hash algorithm (Blowfish in this case) $10 is the cost (or complexity/time) XElWz9WPwSLK3y0jUP6KhO is the salt (always 22 characters)SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.In December 2008, a group of researchers used this technique to fake SSL certificate validity. As of 2010, the CMU Software Engineering Institute considers MD5 "cryptographically broken and unsuitable for further use", and most U.S. government applications now require the SHA-2 family of hash functions.

1 HASH = 0.0003362 USD.
What is a hashed value : A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures.
What hash is $2 a : bcrypt
$2a$ : The hash algorithm identifier (bcrypt) 12 : Input cost (212 i.e. 4096 rounds) R9h/cIPz0gi.URNNX3kh2O : A base-64 encoding of the input salt.
What hash starts with $2$
bcrypt
$2a$ : The hash algorithm identifier (bcrypt) 12 : Input cost (212 i.e. 4096 rounds) R9h/cIPz0gi.URNNX3kh2O : A base-64 encoding of the input salt. PST9/PgBkqquzi.Ss7KIUgO2t0jWMUW : A base-64 encoding of the first 23 bytes of the computed 24 byte hash.

xxHash is an extremely fast hashing algorithm that is not designed for cryptographic purposes, but provides excellent randomness and dispersion of output, and uniqueness of to minimize collisions.A hashrate is a measure of how many calculations can be performed per second and can be measured in billions, trillions, quadrillions, and quintillions. For example, a hashrate of 1TH/s means one trillion calculations can be performed every second. These calculations are being measured based on mining.
What hash is $2 : bcrypt
$2$ : Blowfish-based crypt ('bcrypt')