Block Cipher provides several advantages, including security and confidentiality, speed and efficiency, and widespread adoption and standardization. It ensures that data is protected against unauthorized access or modification, and its widespread adoption makes it easy to integrate into existing systems.Block ciphers are more complex and robust than stream ciphers, as they can provide various security properties, such as diffusion, confusion, and resistance to different types of attacks.Block ciphers have the advantage of high diffusion and strong tamper resistance without detection. They have the disadvantage of slower encryption speed since the entire block must be captured for encryption/decryption. Block ciphers also breed errors since a mistake in just one symbol could alter the whole block.
Where are block ciphers used : They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption. A block cipher uses blocks as an unvarying transformation. Even a secure block cipher is suitable for the encryption of only a single block of data at a time, using a fixed key.
What are the advantages of cipher block chaining
CBC has the advantage over the ECB mode in that the XORing process hides plaintext patterns. Even if the first plaintext block and third plaintext block were the exact same segment of plaintext, it is highly unlikely that the first ciphertext block and third ciphertext block would be the same.
How secure is block cipher : The block cipher modes ECB, CBC, OFB, CFB, CTR, and XTS provide confidentiality, but they do not protect against accidental modification or malicious tampering. Modification or tampering can be detected with a separate message authentication code such as CBC-MAC, or a digital signature.
A ciphertext should never leak any information about the plaintext used to create it, so ECB mode is insecure and should never be used. CBC mode, on the other hand, is one of the most commonly used block cipher modes of operation due to its ease of implementation and support for parallelized decryption. The most common block cipher algorithms
Advanced Encryption Standard (AES). One of the most popular block cipher variants, AES can be used in various applications and many different industries, stretching from IT and cybersecurity to finance.
Data Encryption Standard (DES).
Triple Data Encryption Algorithm (Triple DES).
What are the advantages of stream ciphers
Speed of encryption tops the list of advantages for stream ciphers. Once a stream cipher makes a key, the encryption and decryption process is almost instantaneous. This is largely due to the simplicity of operation, a basic XOR function using two distinct data bits.The main advantage of symmetric encryption over asymmetric encryption is that it is fast and efficient for large amounts of data; the disadvantage is the need to keep the key secret – this can be especially challenging where encryption and decryption take place in different locations, requiring the key to be moved …AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. AES-256 encryption AES-256 encryption is extremely secure. It is the most secure encryption algorithm available today and is used extensively in government and military applications, as well as by businesses operating in highly regulated industries.
Are block ciphers safe : Operation modes
Let's look at the most prevalent block cipher modes: Electronic codebook (ECB). It's one of the weakest operation modes because it encrypts and decrypts data blocks independently in the same exact way, making it easy for hackers to detect patterns.
What is the most effective cipher : Best Encryption Algorithms
AES. The Advanced Encryption Standard (AES) is the trusted standard algorithm used by the United States government, as well as other organizations.
Triple DES.
RSA.
Blowfish.
Twofish.
Rivest-Shamir-Adleman (RSA).
What are the weakness of stream ciphers
Stream ciphers are vulnerable to attack if the same key is used twice (depth of two) or more. Say we send messages A and B of the same length, both encrypted using same key, K. The stream cipher produces a string of bits C(K) the same length as the messages. Like OTP, stream ciphers take a predetermined key k which never changes. Unlike OTP, you can now use this key multiple times. Each time you need to encrypt some data, you rely on a special algorithm to expand your key into a new and unique encryption key.The benefits of asymmetric cryptography include the following:
The key distribution problem is eliminated because there's no need for exchanging keys.
Security is increased since the private keys don't ever have to be transmitted or revealed to anyone.
What is the most safe cipher : The Advanced Encryption Standard (AES) The Advanced Encryption Standard (AES) is currently considered the most secure and widely used encryption algorithm.
Antwort What are the advantages of block cipher? Weitere Antworten – What are the benefits of block cipher
Block Cipher provides several advantages, including security and confidentiality, speed and efficiency, and widespread adoption and standardization. It ensures that data is protected against unauthorized access or modification, and its widespread adoption makes it easy to integrate into existing systems.Block ciphers are more complex and robust than stream ciphers, as they can provide various security properties, such as diffusion, confusion, and resistance to different types of attacks.Block ciphers have the advantage of high diffusion and strong tamper resistance without detection. They have the disadvantage of slower encryption speed since the entire block must be captured for encryption/decryption. Block ciphers also breed errors since a mistake in just one symbol could alter the whole block.
Where are block ciphers used : They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption. A block cipher uses blocks as an unvarying transformation. Even a secure block cipher is suitable for the encryption of only a single block of data at a time, using a fixed key.
What are the advantages of cipher block chaining
CBC has the advantage over the ECB mode in that the XORing process hides plaintext patterns. Even if the first plaintext block and third plaintext block were the exact same segment of plaintext, it is highly unlikely that the first ciphertext block and third ciphertext block would be the same.
How secure is block cipher : The block cipher modes ECB, CBC, OFB, CFB, CTR, and XTS provide confidentiality, but they do not protect against accidental modification or malicious tampering. Modification or tampering can be detected with a separate message authentication code such as CBC-MAC, or a digital signature.
A ciphertext should never leak any information about the plaintext used to create it, so ECB mode is insecure and should never be used. CBC mode, on the other hand, is one of the most commonly used block cipher modes of operation due to its ease of implementation and support for parallelized decryption.

The most common block cipher algorithms
What are the advantages of stream ciphers
Speed of encryption tops the list of advantages for stream ciphers. Once a stream cipher makes a key, the encryption and decryption process is almost instantaneous. This is largely due to the simplicity of operation, a basic XOR function using two distinct data bits.The main advantage of symmetric encryption over asymmetric encryption is that it is fast and efficient for large amounts of data; the disadvantage is the need to keep the key secret – this can be especially challenging where encryption and decryption take place in different locations, requiring the key to be moved …AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today.
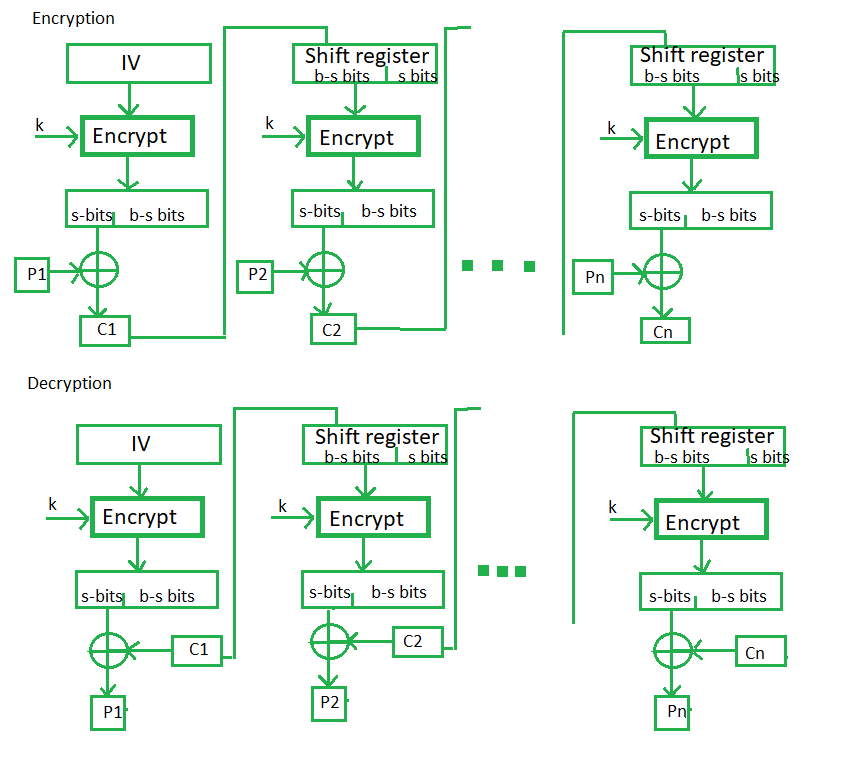
AES-256 encryption
AES-256 encryption is extremely secure. It is the most secure encryption algorithm available today and is used extensively in government and military applications, as well as by businesses operating in highly regulated industries.
Are block ciphers safe : Operation modes
Let's look at the most prevalent block cipher modes: Electronic codebook (ECB). It's one of the weakest operation modes because it encrypts and decrypts data blocks independently in the same exact way, making it easy for hackers to detect patterns.
What is the most effective cipher : Best Encryption Algorithms
What are the weakness of stream ciphers
Stream ciphers are vulnerable to attack if the same key is used twice (depth of two) or more. Say we send messages A and B of the same length, both encrypted using same key, K. The stream cipher produces a string of bits C(K) the same length as the messages.

Like OTP, stream ciphers take a predetermined key k which never changes. Unlike OTP, you can now use this key multiple times. Each time you need to encrypt some data, you rely on a special algorithm to expand your key into a new and unique encryption key.The benefits of asymmetric cryptography include the following:
What is the most safe cipher : The Advanced Encryption Standard (AES)
The Advanced Encryption Standard (AES) is currently considered the most secure and widely used encryption algorithm.