Hashing is a technique that is used to uniquely identify a specific object from a group of similar objects. Some examples of how hashing is used in our lives include: In universities, each student is assigned a unique roll number that can be used to retrieve information about them.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
What is a hash table with an example : A hash table is a type of data structure in which information is stored in an easy-to-retrieve and efficient manner. In the key-value method, keys are assigned random indexes where their values are stored in an array. The index is the information of where exactly in the array the value is stored.
What is an example of hashed data
Hashing can turn PII (such as the name “John” or an SSN) into an indecipherable but uniform string of characters. For example, using the SHA 256 hashing algorithm, “John” hashed becomes “a8cfcd74832004951b4408cdb0a5dbcd8c7e52d43f7fe- 244bf720582e05241da”.
Does Bitcoin use hashing : Bitcoin uses the SHA-256 hash algorithm to generate verifiably “random” numbers in a way that requires a predictable amount of CPU effort. Generating a SHA-256 hash with a value less than the current target solves a block and wins you some coins.
Applications of Hashing Algorithms
Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity.
Signature generation and verification.
Password verification.
Proof-of-work.
File or data identifier.
Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common.
When to use hashing
Hashing is commonly used to ensure data integrity. By generating a hash value for an amount of data, such as a file or message, a user can later compare it with the hash value of the received data to verify if any changes or corruption occurred during transmission.If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.Say we are given keys in the range 0 to 999, and have a hash table of size 10. In this case, a possible hash function might simply divide the key value by 100. Thus, all keys in the range 0 to 99 would hash to slot 0, keys 100 to 199 would hash to slot 1, and so on. A good example is Bitcoin's Secure Hashing Algorithm 256 (commonly shortened to SHA-256). Hashing using SHA-256 always gives an output result of a fixed length, which has a 256-bits length (the output is 32 bytes).
Are cookies hashed : The cookie is hashed, for privacy and security. The cookie is stored by your browser on your local device. On your next visit to the same website, the website reads the cookie and remembers your settings, preferences and activity. Only the website that created a cookie hash can unhash it in order to read it.
Do all Blockchains use hashing : Hashing is an integral part of all blockchain-based transactions, including the trading of cryptocurrency. Hash functions are necessary in everything from mining blocks to signing transactions to generating private keys. A hash function is a mathematical algorithm used to calculate the hash.
Does ethereum use hashing
The most commonly used hash function on Ethereum is Keccak256. However, it's crucial to exercise caution, as some libraries may refer to Keccak256 as SHA-256, which is a distinct hash function. SHA-256 is a variant of SHA-2 (Secure Hash Algorithm 2) with a 256-bit output and is extensively employed by Bitcoin. Some of the most common applications of hashing in cybersecurity are: Message integrity. File integrity. Password validation.The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function.
Does Google use hashing : How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.
Antwort What are some examples of hashing? Weitere Antworten – What is an example of hashing
Hashing is a technique that is used to uniquely identify a specific object from a group of similar objects. Some examples of how hashing is used in our lives include: In universities, each student is assigned a unique roll number that can be used to retrieve information about them.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.Hashing is the process of using a mathematical function to convert input data into a fixed-length output. Businesses use hashing functions to ensure that the data stored on servers and cloud storage systems remain unreadable even if malicious hackers gain access to the data.
What is a hash table with an example : A hash table is a type of data structure in which information is stored in an easy-to-retrieve and efficient manner. In the key-value method, keys are assigned random indexes where their values are stored in an array. The index is the information of where exactly in the array the value is stored.
What is an example of hashed data
Hashing can turn PII (such as the name “John” or an SSN) into an indecipherable but uniform string of characters. For example, using the SHA 256 hashing algorithm, “John” hashed becomes “a8cfcd74832004951b4408cdb0a5dbcd8c7e52d43f7fe- 244bf720582e05241da”.
Does Bitcoin use hashing : Bitcoin uses the SHA-256 hash algorithm to generate verifiably “random” numbers in a way that requires a predictable amount of CPU effort. Generating a SHA-256 hash with a value less than the current target solves a block and wins you some coins.
Applications of Hashing Algorithms
Storing passwords as simple hashes is now considered insecure, although unfortunately it is still very common.
When to use hashing
Hashing is commonly used to ensure data integrity. By generating a hash value for an amount of data, such as a file or message, a user can later compare it with the hash value of the received data to verify if any changes or corruption occurred during transmission.If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.Say we are given keys in the range 0 to 999, and have a hash table of size 10. In this case, a possible hash function might simply divide the key value by 100. Thus, all keys in the range 0 to 99 would hash to slot 0, keys 100 to 199 would hash to slot 1, and so on.
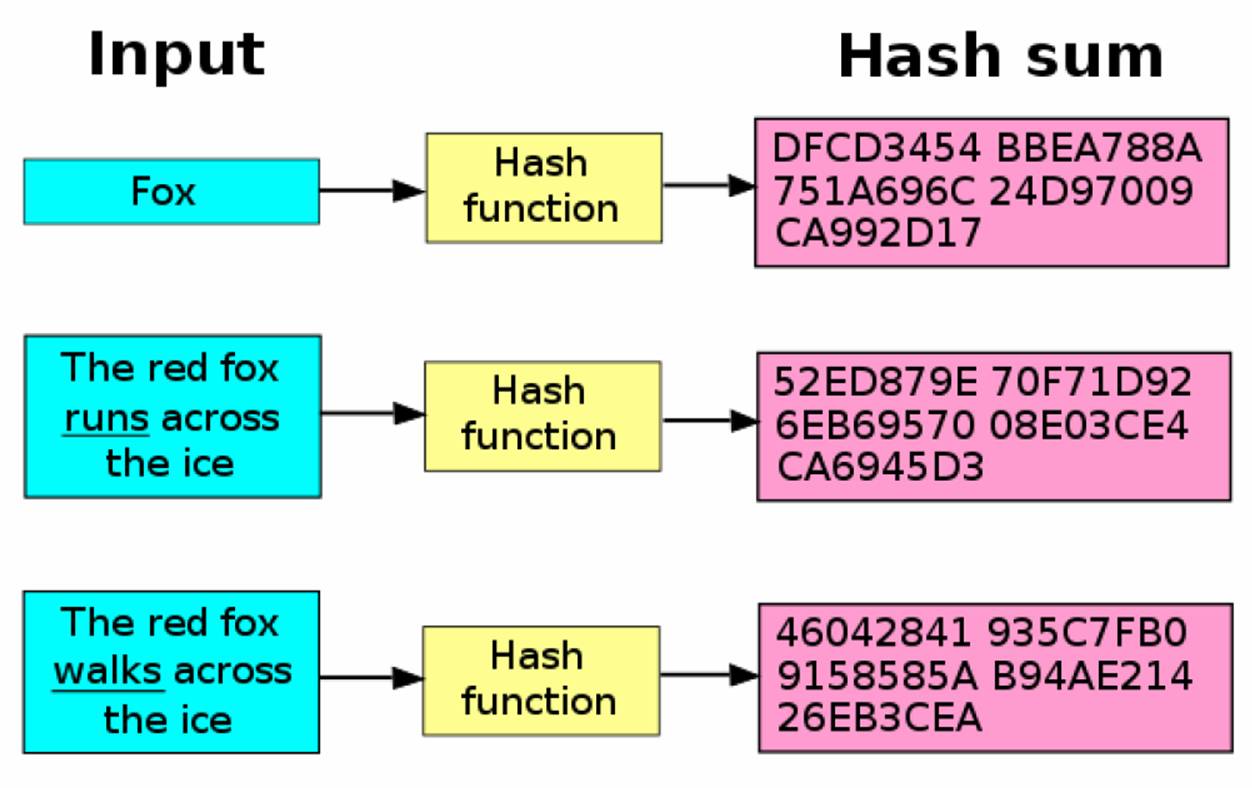
A good example is Bitcoin's Secure Hashing Algorithm 256 (commonly shortened to SHA-256). Hashing using SHA-256 always gives an output result of a fixed length, which has a 256-bits length (the output is 32 bytes).
Are cookies hashed : The cookie is hashed, for privacy and security. The cookie is stored by your browser on your local device. On your next visit to the same website, the website reads the cookie and remembers your settings, preferences and activity. Only the website that created a cookie hash can unhash it in order to read it.
Do all Blockchains use hashing : Hashing is an integral part of all blockchain-based transactions, including the trading of cryptocurrency. Hash functions are necessary in everything from mining blocks to signing transactions to generating private keys. A hash function is a mathematical algorithm used to calculate the hash.
Does ethereum use hashing
The most commonly used hash function on Ethereum is Keccak256. However, it's crucial to exercise caution, as some libraries may refer to Keccak256 as SHA-256, which is a distinct hash function. SHA-256 is a variant of SHA-2 (Secure Hash Algorithm 2) with a 256-bit output and is extensively employed by Bitcoin.
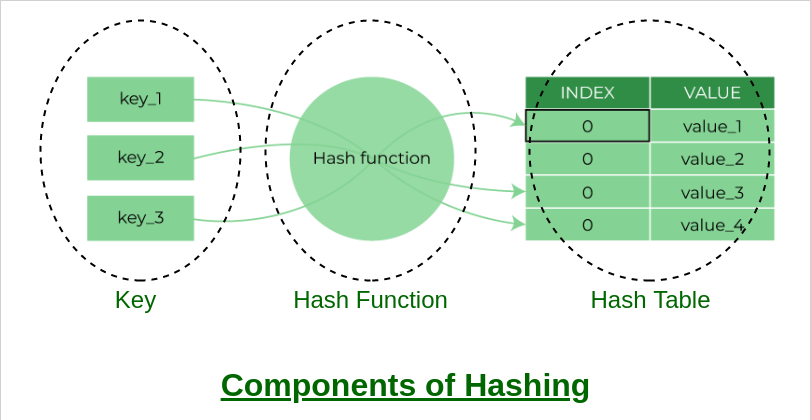
Some of the most common applications of hashing in cybersecurity are: Message integrity. File integrity. Password validation.The MD5 algorithm, defined in RFC 1321, is probably the most well-known and widely used hash function.
Does Google use hashing : How are passwords detected and stored When users sign in to specific sign-in pages, Chrome generates a password fingerprint. Using scrypt, Chrome hashes the password and shortens it to 37 bits, which is enough to identify the password if it's reused on dangerous or disallowed websites.