Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.Hash Tables: The most common use of hash functions in DSA is in hash tables, which provide an efficient way to store and retrieve data. Data Integrity: Hash functions are used to ensure the integrity of data by generating checksums.The importance of hash functions is evident in their widespread use in various applications such as digital signatures, password storage, and message authentication codes. These functions have proven to be a reliable method for protecting data and ensuring that it has not been tampered with or altered.
Where are hash functions used : Hash functions are mathematical functions that transform or "map" a given data set into a bit string of fixed size, also known as the "hash value." Hash functions are used in cryptography and have variable levels of complexity and difficulty.
What are some uses of hashing algorithms
Hashing protects data at rest, so even if someone gains access to your server, the items stored there remain unreadable. Hashing can also help you prove that data isn't adjusted or altered after the author is finished with it. And some people use hashing to help them make sense of reams of data.
What are the commonly used hash function in data structure : In data structures, a hash function is used to calculate the hash value of a key, which is then used to store and retrieve the corresponding data. Hash functions are often used in conjunction with an array, where the hash value is used as an index in the array.
The primary types of hash functions are: Division Method. Mid Square Method. Folding Method. SHA
SHA is perhaps the most widely used family of hash functions.
What are the three most common applications for hashing
Applications of Hashing Algorithms
Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity.
Signature generation and verification.
Password verification.
Proof-of-work.
File or data identifier.
Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications. There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is the most used hash algorithm : SHA-256
SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
Why do we need hashing : Hashing enables efficient data retrieval in hash tables, especially when dealing with large data sets. It uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map.
Why use hash function in cryptography
Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification. Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.Banks typically use strong encryption algorithms to secure user passwords and protect sensitive information. Some commonly used encryption algorithms in the banking industry include: Secure Hash Algorithm (SHA): Banks may use SHA-256 or SHA-512, which are widely accepted and secure hash functions.
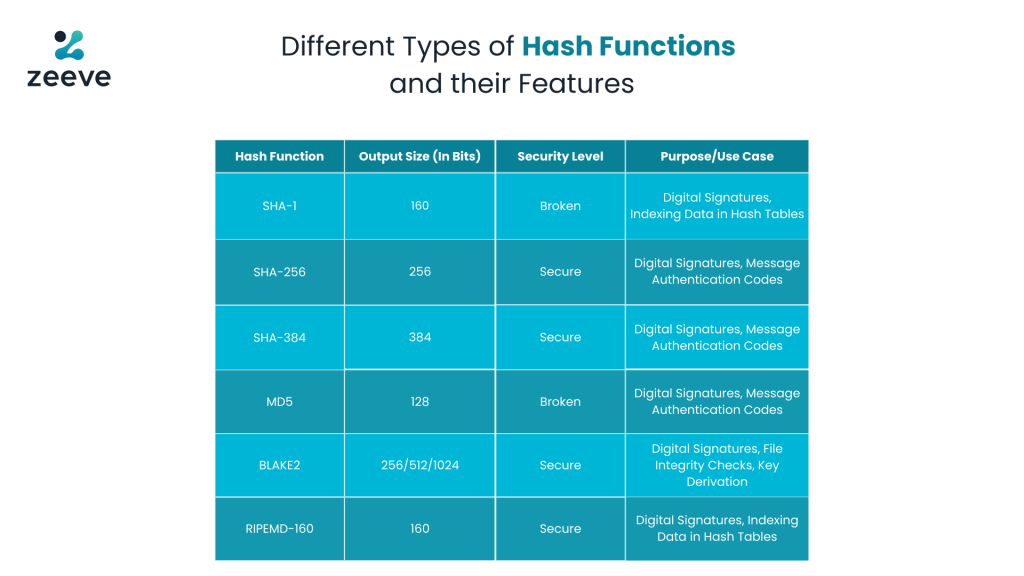
What is an example of a hash function : Other examples of common hashing algorithms include: Message Digest (MD) Algorithm — MD2, MD4, MD5, and MD6. MD5 was long considered a go-to hashing algorithm, but it's now considered broken because of hash collisions. Windows NTHash — Also known as a Unicode hash or NTLM, this hash is commonly used by Windows systems.
Antwort What are 5 common uses applications of hash functions? Weitere Antworten – What are the applications of hash function
Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.Hash Tables: The most common use of hash functions in DSA is in hash tables, which provide an efficient way to store and retrieve data. Data Integrity: Hash functions are used to ensure the integrity of data by generating checksums.The importance of hash functions is evident in their widespread use in various applications such as digital signatures, password storage, and message authentication codes. These functions have proven to be a reliable method for protecting data and ensuring that it has not been tampered with or altered.
Where are hash functions used : Hash functions are mathematical functions that transform or "map" a given data set into a bit string of fixed size, also known as the "hash value." Hash functions are used in cryptography and have variable levels of complexity and difficulty.
What are some uses of hashing algorithms
Hashing protects data at rest, so even if someone gains access to your server, the items stored there remain unreadable. Hashing can also help you prove that data isn't adjusted or altered after the author is finished with it. And some people use hashing to help them make sense of reams of data.
What are the commonly used hash function in data structure : In data structures, a hash function is used to calculate the hash value of a key, which is then used to store and retrieve the corresponding data. Hash functions are often used in conjunction with an array, where the hash value is used as an index in the array.
The primary types of hash functions are: Division Method. Mid Square Method. Folding Method.

SHA
SHA is perhaps the most widely used family of hash functions.
What are the three most common applications for hashing
Applications of Hashing Algorithms
Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.Hashing is applicable to data searching and retrieving, digital signatures, cybersecurity, and cryptography, among many other applications.
There are many practical examples of hash tables used in every-day life. A popular example is in username-password databases. Every time someone signs up on a website using a username and password, that information must be stored somewhere for later retrieval.
What is the most used hash algorithm : SHA-256
SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
Why do we need hashing : Hashing enables efficient data retrieval in hash tables, especially when dealing with large data sets. It uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map.
Why use hash function in cryptography
Hash functions are a way to ensure data integrity in public key cryptography. What I mean by that is that hash functions serve as a check-sum, or a way for someone to identify whether data has been tampered with after it's been signed. It also serves as a means of identity verification.

Hash functions are also referred to as hashing algorithms or message digest functions. They are used across many areas of computer science, for example: To encrypt communication between web servers and browsers, and generate session IDs for internet applications and data caching.Banks typically use strong encryption algorithms to secure user passwords and protect sensitive information. Some commonly used encryption algorithms in the banking industry include: Secure Hash Algorithm (SHA): Banks may use SHA-256 or SHA-512, which are widely accepted and secure hash functions.
What is an example of a hash function : Other examples of common hashing algorithms include: Message Digest (MD) Algorithm — MD2, MD4, MD5, and MD6. MD5 was long considered a go-to hashing algorithm, but it's now considered broken because of hash collisions. Windows NTHash — Also known as a Unicode hash or NTLM, this hash is commonly used by Windows systems.