The reason why SHA-512 is faster than SHA-256 on 64-bit machines is that has 37.5% less rounds per byte (80 rounds operating on 128 byte blocks) compared to SHA- 256 (64 rounds operating on 64 byte blocks), where the operations use 64-bit integer arithmetic.Robustness and Resistance to various cryptographic attacks — SHA-512 produces a fixed-size 512-bit hash value, providing a vast number of possible output combinations, which enhances its resistance to collision attacks.SHA-2 Family – SHA-512 and SHA384 provide stronger collision resistance at the cost of slower calculation and larger output size. 3. BLAKE2 (BLAKE2s and BLAKE2b) – Faster than SHA256 while offering comparable collision resistance, making them suitable for performance-critical applications.
What is the difference between SHA-1 256 and 512 : Speed and Security
The SHA-1 vs. SHA-256 speed metrics differ, with SHA-1 being the oldest and the fastest but least secure. SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security.
Is SHA-512 overkill
SHA512 is probably overkill. "for a while" suggests that this was ever a recommended choice, which is not the case. As others have pointed out, for password hashing you want a specialized algorithm, not a general purpose cryptographic hash function.
Is SHA-256 outdated : "SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
SHA-512 is vulnerable to pre-image attacks. Two variants of SHA-512, which are SHA-512/224 and SHA-512/256, are also susceptible to collision attacks. Among MD4, MD5, SHA1, and SHA256, SHA256 is considered the strongest hash function in terms of security and cryptographic strength. It provides a higher level of security compared to MD4, MD5, and SHA1, making it more resistant to potential attacks.
Is SHA 512 overkill
SHA512 is probably overkill. "for a while" suggests that this was ever a recommended choice, which is not the case. As others have pointed out, for password hashing you want a specialized algorithm, not a general purpose cryptographic hash function.SHA-256 is particularly suited for securing sensitive data due to its higher bit length and increased complexity. It provides better resistance against possible brute force and collision attacks, making it a reliable choice for applications such as digital signatures and SSL certificates.Password Hash Security Considerations
The SHA1, SHA256, and SHA512 functions are no longer considered secure, either, and PBKDF2 is considered acceptable. The most secure current hash functions are BCRYPT, SCRYPT, and Argon2. In addition to the hash function, the scheme should always use a salt. SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.
Why is SHA-256 not secure : A good hash algorithm makes it impossible to reverse the hash value to compute the original text. However, passwords are very, very short. By making a guess at a password, the attacker can compare the output of his SHA-256 against the SHA-256 that he finds in the database.
Has SHA512 been broken : There are no known attacks against SHA-512, not against collision resistance and certainly not against first or second preimage resistance.
Why is SHA-256 unbreakable
Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash. Final Thoughts on What Is the Most Secure Hashing Algorithm
To the time of writing, SHA-256 is still the most secure hashing algorithm out there.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Is SHA-512 weak : Strengths and Weaknesses of SHA-512
SHA-512 typically delivers a slower performance compared to SHA-256. However, regarding security, SHA-512 takes the upper hand with its longer hash output size. Therefore, the choice between SHA-256 and SHA-512 depends on balancing performance needs and security requirements.
Antwort Is SHA-512 better than SHA-256? Weitere Antworten – What is better, SHA-256 or SHA-512
The reason why SHA-512 is faster than SHA-256 on 64-bit machines is that has 37.5% less rounds per byte (80 rounds operating on 128 byte blocks) compared to SHA- 256 (64 rounds operating on 64 byte blocks), where the operations use 64-bit integer arithmetic.Robustness and Resistance to various cryptographic attacks — SHA-512 produces a fixed-size 512-bit hash value, providing a vast number of possible output combinations, which enhances its resistance to collision attacks.SHA-2 Family – SHA-512 and SHA384 provide stronger collision resistance at the cost of slower calculation and larger output size. 3. BLAKE2 (BLAKE2s and BLAKE2b) – Faster than SHA256 while offering comparable collision resistance, making them suitable for performance-critical applications.
What is the difference between SHA-1 256 and 512 : Speed and Security
The SHA-1 vs. SHA-256 speed metrics differ, with SHA-1 being the oldest and the fastest but least secure. SHA-2 (including SHA-256) offers a nice balance between speed and security, while SHA-512 has a larger hash size and is slower but offers higher security.
Is SHA-512 overkill
SHA512 is probably overkill. "for a while" suggests that this was ever a recommended choice, which is not the case. As others have pointed out, for password hashing you want a specialized algorithm, not a general purpose cryptographic hash function.
Is SHA-256 outdated : "SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
SHA-512 is vulnerable to pre-image attacks. Two variants of SHA-512, which are SHA-512/224 and SHA-512/256, are also susceptible to collision attacks.

Among MD4, MD5, SHA1, and SHA256, SHA256 is considered the strongest hash function in terms of security and cryptographic strength. It provides a higher level of security compared to MD4, MD5, and SHA1, making it more resistant to potential attacks.
Is SHA 512 overkill
SHA512 is probably overkill. "for a while" suggests that this was ever a recommended choice, which is not the case. As others have pointed out, for password hashing you want a specialized algorithm, not a general purpose cryptographic hash function.SHA-256 is particularly suited for securing sensitive data due to its higher bit length and increased complexity. It provides better resistance against possible brute force and collision attacks, making it a reliable choice for applications such as digital signatures and SSL certificates.Password Hash Security Considerations
The SHA1, SHA256, and SHA512 functions are no longer considered secure, either, and PBKDF2 is considered acceptable. The most secure current hash functions are BCRYPT, SCRYPT, and Argon2. In addition to the hash function, the scheme should always use a salt.
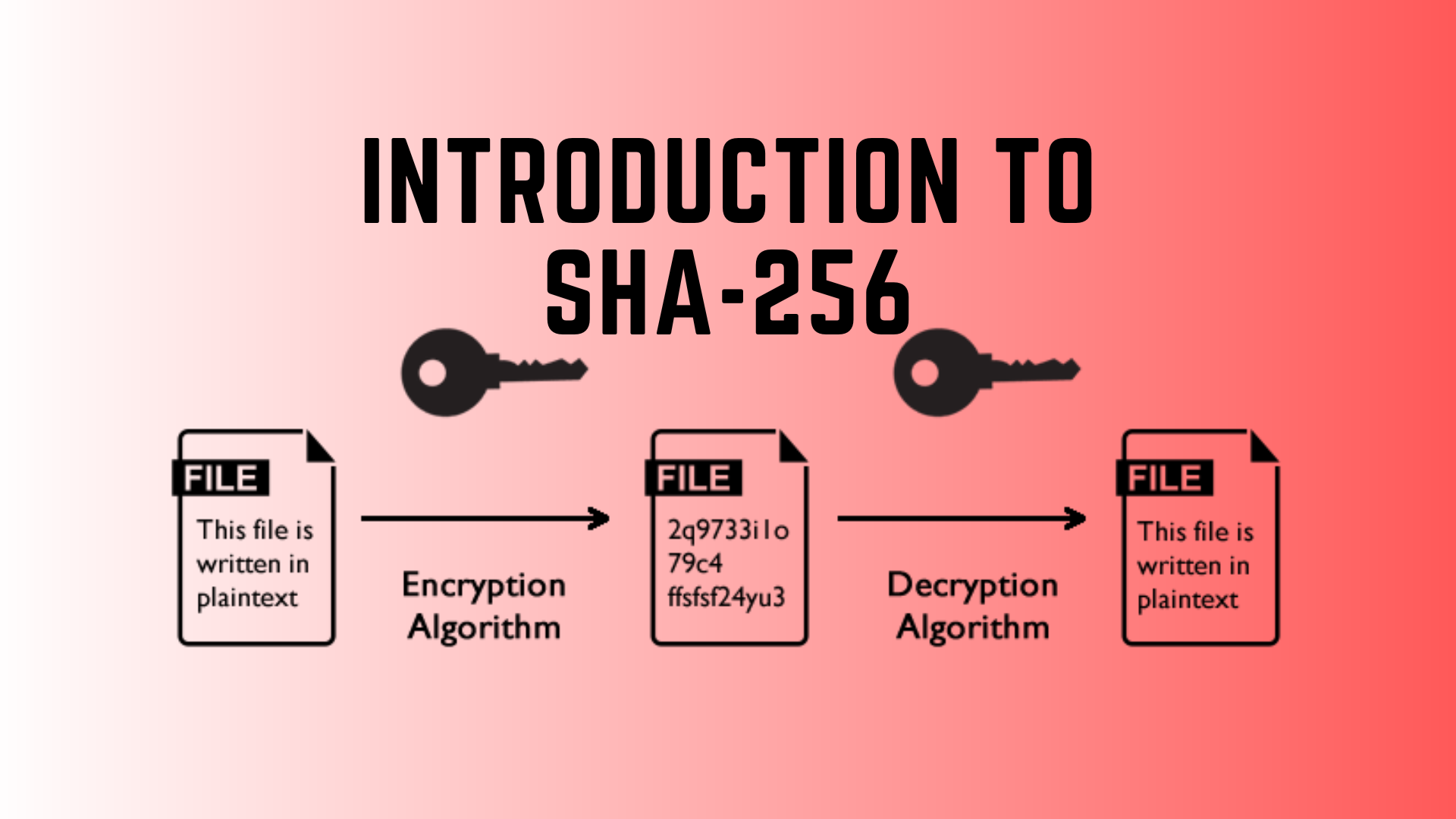
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.
Why is SHA-256 not secure : A good hash algorithm makes it impossible to reverse the hash value to compute the original text. However, passwords are very, very short. By making a guess at a password, the attacker can compare the output of his SHA-256 against the SHA-256 that he finds in the database.
Has SHA512 been broken : There are no known attacks against SHA-512, not against collision resistance and certainly not against first or second preimage resistance.
Why is SHA-256 unbreakable
Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.

Final Thoughts on What Is the Most Secure Hashing Algorithm
To the time of writing, SHA-256 is still the most secure hashing algorithm out there.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Is SHA-512 weak : Strengths and Weaknesses of SHA-512
SHA-512 typically delivers a slower performance compared to SHA-256. However, regarding security, SHA-512 takes the upper hand with its longer hash output size. Therefore, the choice between SHA-256 and SHA-512 depends on balancing performance needs and security requirements.