SHA256 provides better security and is the recommended hash function for these use cases. If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one.SHA-256 is not a secure password hashing algorithm. SHA-512 neither, regardless of how good it has been salted.Bitcoin's SHA256 encryption algorithm is still safe despite Chinese researchers' claims of cracking RSA encryption with existing quantum computers. A group of 24 Chinese researchers said they could factor a 48-bit number using a 10-qubit quantum computer.
Is SHA-512 more secure than SHA-256 : SHA-256 is a secure algorithm and is the most widely used. It is computed with 32-bit words. SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.
Is SHA256 secure in 2024
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.
Is SHA256 deprecated : "SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue. Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.
Is SHA-256 secure in 2024
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.SHA512 is probably overkill. "for a while" suggests that this was ever a recommended choice, which is not the case. As others have pointed out, for password hashing you want a specialized algorithm, not a general purpose cryptographic hash function.Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm, 512 bits in SHA-512, and so on. Bigger digests usually suggest significantly more calculations at the cost of speed and space. Irreversible: By design, all hash functions such as the SHA 256 are irreversible. "SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
Can 256 encryption be hacked : Is AES-256 Encryption Crackable AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities. However, no encryption standard or system is completely secure.
How easy is it to crack SHA-256 : Hashing is an algorithm that generates a fixed-length string from an input. There are many different hash algorithms with different properties, for example, SHA-256. Hashes have a special property: they are easy to compute but difficult to reverse: given the hash above, it difficult to find its origin, “secret”.
Is SHA-256 enough
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack. For example, if you had to defend against a DDoS attack, you could use SHA-256 to authenticate and verify the integrity of incoming network traffic. Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.Furthermore, with SSL, 256-bit encryption is pretty strong. And, by the time an attacker using the latest computer tries cracking 256-bit encryption, it'll get discarded, and, likely, your SSL certificate will also get replaced with the newer one.
Has AES-128 been cracked : Hence, it is safe to say that AES-128 encryption is safe against brute-force attacks. AES has never been cracked yet and it would take large amounts of computational power to crack this key. Governmental organizations and businesses trust the AES for securing sensitive information.
Antwort Is SHA-256 still secure? Weitere Antworten – Is SHA-256 still good
SHA256 provides better security and is the recommended hash function for these use cases. If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one.SHA-256 is not a secure password hashing algorithm. SHA-512 neither, regardless of how good it has been salted.Bitcoin's SHA256 encryption algorithm is still safe despite Chinese researchers' claims of cracking RSA encryption with existing quantum computers. A group of 24 Chinese researchers said they could factor a 48-bit number using a 10-qubit quantum computer.
Is SHA-512 more secure than SHA-256 : SHA-256 is a secure algorithm and is the most widely used. It is computed with 32-bit words. SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words.
Is SHA256 secure in 2024
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.
Is SHA256 deprecated : "SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
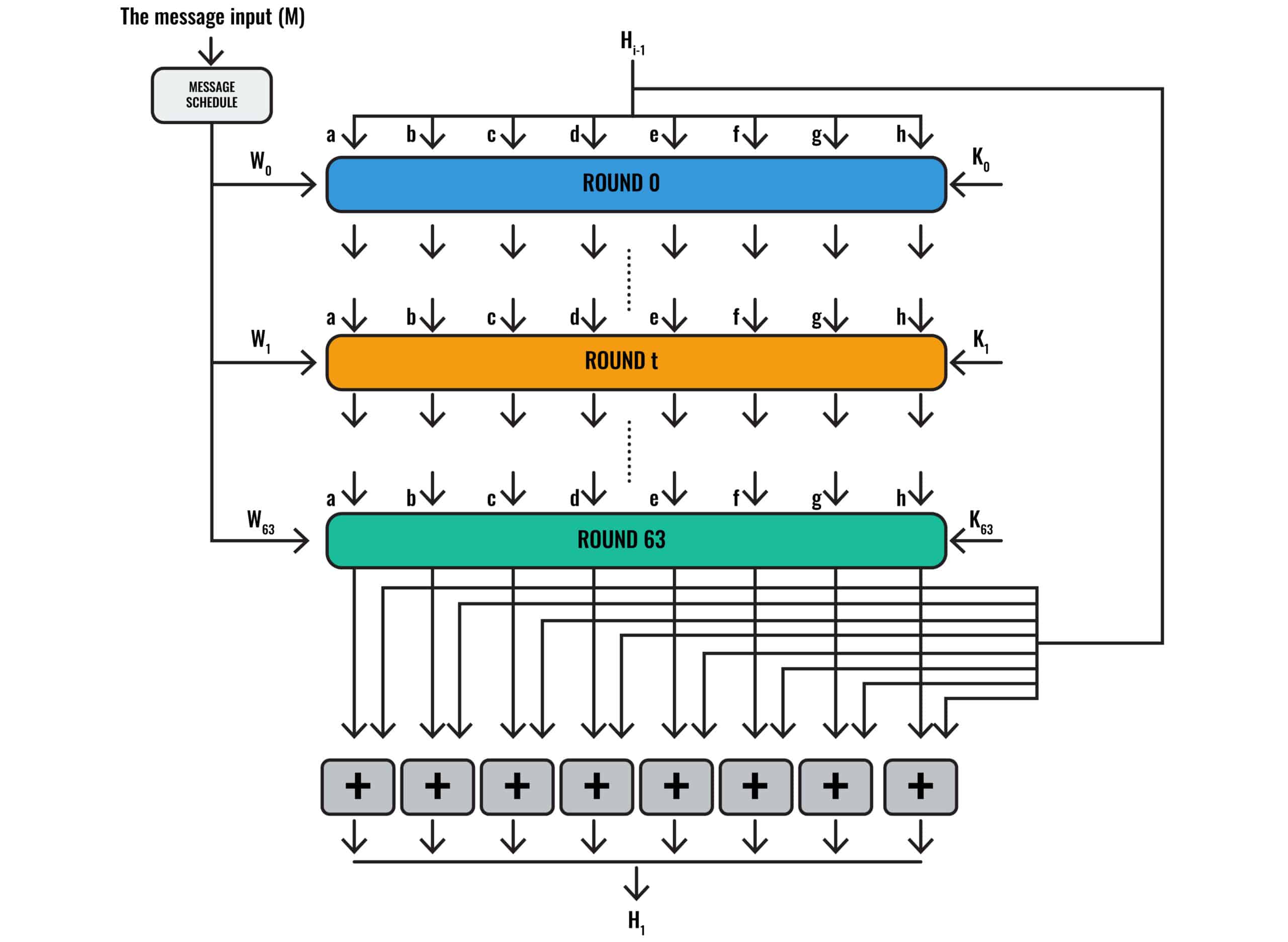
Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.
Is SHA-256 secure in 2024
SHA-256 is secure due to its 256-bit hash output, making it exponentially more complex and harder to crack than SHA-1.SHA512 is probably overkill. "for a while" suggests that this was ever a recommended choice, which is not the case. As others have pointed out, for password hashing you want a specialized algorithm, not a general purpose cryptographic hash function.Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm, 512 bits in SHA-512, and so on. Bigger digests usually suggest significantly more calculations at the cost of speed and space. Irreversible: By design, all hash functions such as the SHA 256 are irreversible.
"SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
Can 256 encryption be hacked : Is AES-256 Encryption Crackable AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities. However, no encryption standard or system is completely secure.
How easy is it to crack SHA-256 : Hashing is an algorithm that generates a fixed-length string from an input. There are many different hash algorithms with different properties, for example, SHA-256. Hashes have a special property: they are easy to compute but difficult to reverse: given the hash above, it difficult to find its origin, “secret”.
Is SHA-256 enough
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack. For example, if you had to defend against a DDoS attack, you could use SHA-256 to authenticate and verify the integrity of incoming network traffic.
Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.Furthermore, with SSL, 256-bit encryption is pretty strong. And, by the time an attacker using the latest computer tries cracking 256-bit encryption, it'll get discarded, and, likely, your SSL certificate will also get replaced with the newer one.
Has AES-128 been cracked : Hence, it is safe to say that AES-128 encryption is safe against brute-force attacks. AES has never been cracked yet and it would take large amounts of computational power to crack this key. Governmental organizations and businesses trust the AES for securing sensitive information.