The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
SHA-256 (Secure Hash Algorithm 256-bit)
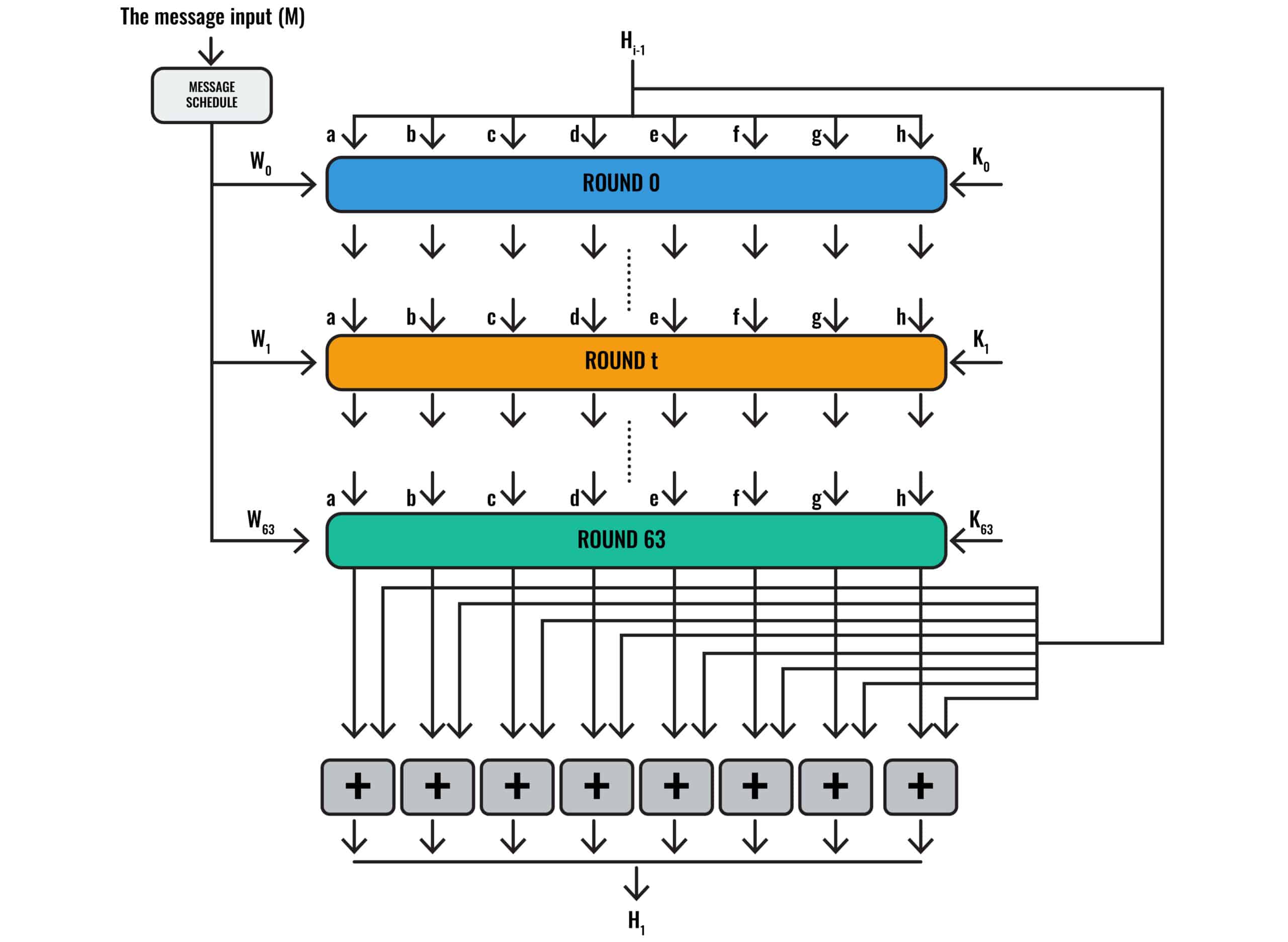
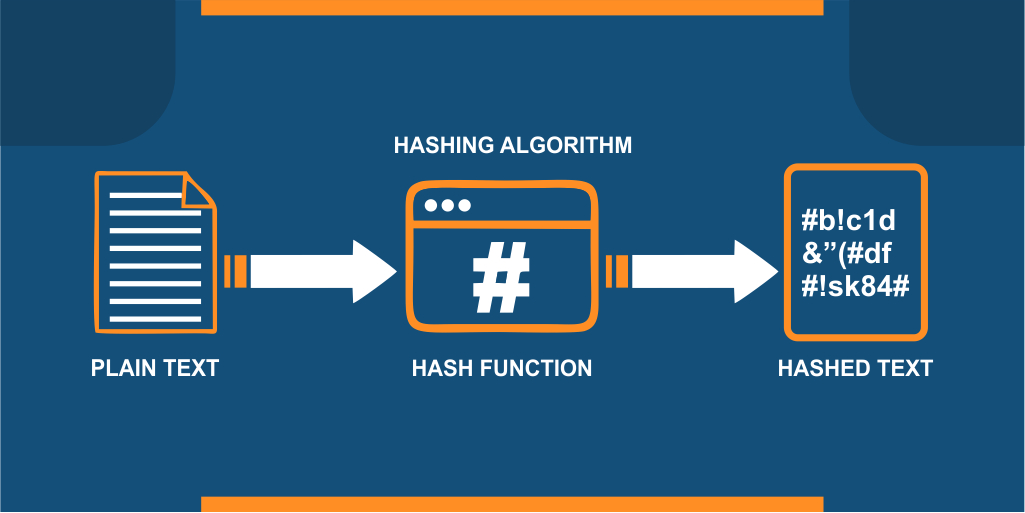
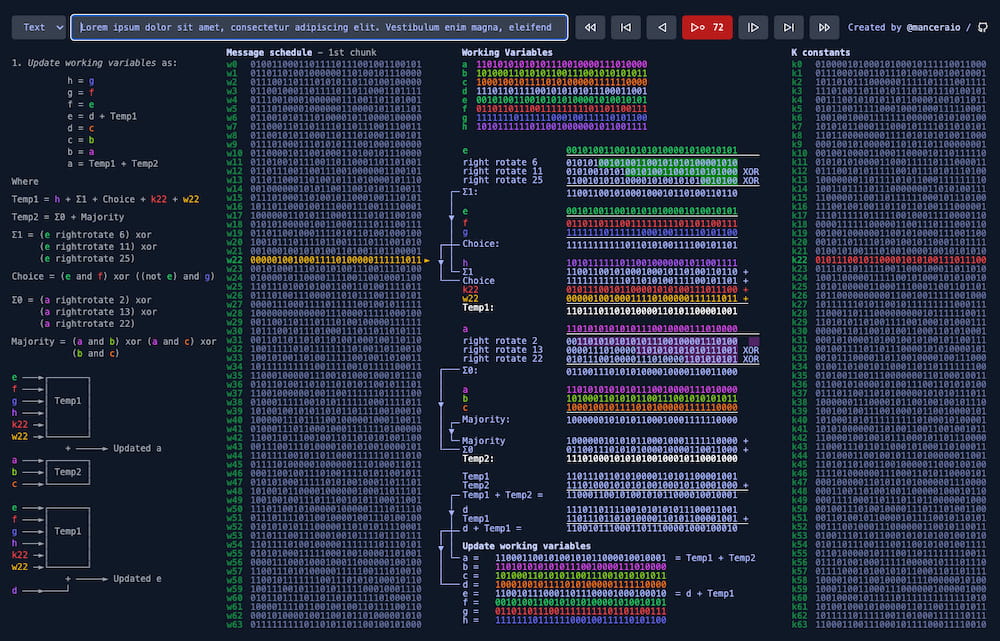
SHA-256 refers to a cryptographic hash function that belongs to the SHA-2 (Secure Hash Algorithm 2) family. It generates a fixed-size 256-bit (32-byte) hash value from input data of arbitrary length. SHA-256 is widely used in cryptography and data integrity verification.
Can you decrypt SHA-256 : SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Is SHA-256 hash unique
Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.
Is SHA a type of hash function : SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.
It is deterministic, meaning that a specific input (or file) will always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file. If two people independently (and correctly) check the hash value of a file, they will always get the same answer. While SHA256 is a cryptographic hash function that generates a fixed-size output (256 bits) from any input data, AES256 is a symmetric encryption algorithm that utilizes a 256-bit key for data encryption and decryption. These two cryptographic algorithms play distinct roles in the realm of cybersecurity.
Can you fake SHA-256
you can't – a hash by definition is non-reversible: in that you can't take a hash value and retrieve the input file. the sha256 hash is by definition 256 bits 'wide' – that is 32 bytes. which means at most it has 2^{256} possible values. That is all.Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.The SHA-256 (as well as any cryptographically secure hash algorithm) produces output that will appear like an uniformly random sequence to observer who does not know the input. The basic difference between SHA1 vs. SHA256 or SHA1 vs SHA2 is the length of the key used to encrypt the data transferred online. SHA1 uses 160 bit long key to encrypt data while SHA256 uses 256 bit long key to encrypt data. SHA2 is a family of algorithms developed by the US government to secure the data online.
Is SHA hash unique : An SHA value (any version) is not unique, it cannot be, because it maps an infinite number of inputs (an input of any length) to a finite number of outputs.
Is SHA-256 hash always unique : Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.
Is SHA-256 better than AES
SHA256 is primarily employed for data integrity checks and digital signatures. On the other hand, AES256 is widely utilized for safeguarding sensitive information during storage and transmission. AES is used for encryption and decryption to protect data confidentiality, while SHA-256 is used for hashing to ensure data integrity and authenticity. Both play essential roles in modern cryptography and security protocols.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Is SHA-256 truly random : If you feed SHA-256 with too little entropy (or even smaller input than 256 bits), the output may appear random, but it is not.
Antwort Is SHA-256 a hash? Weitere Antworten – Is SHA-256 a hash
The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.You can use Windows Powershell to calculate the SHA-256 checksum for a file.
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 refers to a cryptographic hash function that belongs to the SHA-2 (Secure Hash Algorithm 2) family. It generates a fixed-size 256-bit (32-byte) hash value from input data of arbitrary length. SHA-256 is widely used in cryptography and data integrity verification.

Can you decrypt SHA-256 : SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Is SHA-256 hash unique
Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.
Is SHA a type of hash function : SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.
It is deterministic, meaning that a specific input (or file) will always deliver the same hash value (number string). This means that it is easy to verify the authenticity of a file. If two people independently (and correctly) check the hash value of a file, they will always get the same answer.
While SHA256 is a cryptographic hash function that generates a fixed-size output (256 bits) from any input data, AES256 is a symmetric encryption algorithm that utilizes a 256-bit key for data encryption and decryption. These two cryptographic algorithms play distinct roles in the realm of cybersecurity.
Can you fake SHA-256
you can't – a hash by definition is non-reversible: in that you can't take a hash value and retrieve the input file. the sha256 hash is by definition 256 bits 'wide' – that is 32 bytes. which means at most it has 2^{256} possible values. That is all.Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.The SHA-256 (as well as any cryptographically secure hash algorithm) produces output that will appear like an uniformly random sequence to observer who does not know the input.
The basic difference between SHA1 vs. SHA256 or SHA1 vs SHA2 is the length of the key used to encrypt the data transferred online. SHA1 uses 160 bit long key to encrypt data while SHA256 uses 256 bit long key to encrypt data. SHA2 is a family of algorithms developed by the US government to secure the data online.
Is SHA hash unique : An SHA value (any version) is not unique, it cannot be, because it maps an infinite number of inputs (an input of any length) to a finite number of outputs.
Is SHA-256 hash always unique : Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.
Is SHA-256 better than AES
SHA256 is primarily employed for data integrity checks and digital signatures. On the other hand, AES256 is widely utilized for safeguarding sensitive information during storage and transmission.
AES is used for encryption and decryption to protect data confidentiality, while SHA-256 is used for hashing to ensure data integrity and authenticity. Both play essential roles in modern cryptography and security protocols.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Is SHA-256 truly random : If you feed SHA-256 with too little entropy (or even smaller input than 256 bits), the output may appear random, but it is not.