SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.The speed of MD5 is fast in comparison of SHA1's speed. While the speed of SHA1 is slow in comparison of MD5's speed.Advantages and Disadvantages
Advantages
Disadvantages
SHA-256 provides a high level of security, making it practically impossible to derive the original data from its hash value.
Although rare, there is a theoretical possibility of hash collisions, where two different inputs produce the same hash value.
What is the difference between sha512 and MD5 : Considering MD5 uses 128 bits (32 bytes in HEX, 16 bytes in binary), and SHA 512 is only 4x the space but virtually eliminates the collision ratio by giving you 2^384 more possible IDs… Go with SHA-512, every time.
Why is MD5 not recommended
Weak security: MD5 produces a fixed-sized 128-bit hash value, which is significantly shorter than modern secure hash functions like SHA-256 or SHA-3. A shorter hash length reduces the resistance against brute-force and collision attacks, increasing the risk of an attacker successfully compromising the data.
Is MD5 still good : As of 2010, the CMU Software Engineering Institute considers MD5 "cryptographically broken and unsuitable for further use", and most U.S. government applications now require the SHA-2 family of hash functions.
A major concern with MD5 is the potential it has for message collisions when message hash codes are inadvertently duplicated. MD5 hash code strings also are limited to 128 bits. This makes them easier to breach than other hash code algorithms that followed. As of 2019, MD5 continues to be widely used, despite its well-documented weaknesses and deprecation by security experts. A collision attack exists that can find collisions within seconds on a computer with a 2.6 GHz Pentium 4 processor (complexity of 224.1).
What are the advantages of SHA-256 over MD5
MD5 produces a 128-bit output, and SHA256 produces a 256-bit output. Generally, the longer the output, the more secure the hash function, as it reduces the chances of collisions (two different inputs producing the same output).collision attacks
Weak security: MD5 produces a fixed-sized 128-bit hash value, which is significantly shorter than modern secure hash functions like SHA-256 or SHA-3. A shorter hash length reduces the resistance against brute-force and collision attacks, increasing the risk of an attacker successfully compromising the data.In terms of speed, the MD5 is slightly faster than SHA-2. Therefore, the MD5 is often used as a checksum for verifying files integrity. To sum up, in most cases, SHA-2 will do better than MD5. It's more secure, reliable, and less likely to be broken. Vulnerabilities: The MD5 algorithm has long been considered insecure for cryptographic purposes due to significant vulnerabilities. Researchers have demonstrated practical collision attacks against MD5, which allows for the creation of different inputs that produce the same hash value.
Is MD5 still usable : MD5 is still being used today as a hash function even though it has been exploited for years.
Why is MD5 no longer used : Historically it was widely used as a cryptographic hash function; however it has been found to suffer from extensive vulnerabilities.
How fast is SHA-256 vs MD5
The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits. While not quite perfect, current research indicates it is considerably more secure than either MD5 or SHA-1. Performance-wise, a SHA-256 hash is about 20-30% slower to calculate than either MD5 or SHA-1 hashes. The conclusion is that SHA-2 does better than MD5 in most cases, especially regarding security. On the other hand, MD5 can be used in solutions that don't require a high level of security and when speed is the main criteria.Probably the one most commonly used is SHA-256, which the National Institute of Standards and Technology (NIST) recommends using instead of MD5 or SHA-1. The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits.
Why is MD5 good : Meanwhile, MD5 is a secure hash algorithm and a cryptographic hash function that can detect some data corruption but is primarily intended for the secure encryption of data that is being transmitted and the verification of digital certificates.
Antwort Is MD5 better than SHA-256? Weitere Antworten – Is SHA256 better than MD5
SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.The speed of MD5 is fast in comparison of SHA1's speed. While the speed of SHA1 is slow in comparison of MD5's speed.Advantages and Disadvantages
What is the difference between sha512 and MD5 : Considering MD5 uses 128 bits (32 bytes in HEX, 16 bytes in binary), and SHA 512 is only 4x the space but virtually eliminates the collision ratio by giving you 2^384 more possible IDs… Go with SHA-512, every time.
Why is MD5 not recommended
Weak security: MD5 produces a fixed-sized 128-bit hash value, which is significantly shorter than modern secure hash functions like SHA-256 or SHA-3. A shorter hash length reduces the resistance against brute-force and collision attacks, increasing the risk of an attacker successfully compromising the data.
Is MD5 still good : As of 2010, the CMU Software Engineering Institute considers MD5 "cryptographically broken and unsuitable for further use", and most U.S. government applications now require the SHA-2 family of hash functions.
A major concern with MD5 is the potential it has for message collisions when message hash codes are inadvertently duplicated. MD5 hash code strings also are limited to 128 bits. This makes them easier to breach than other hash code algorithms that followed.
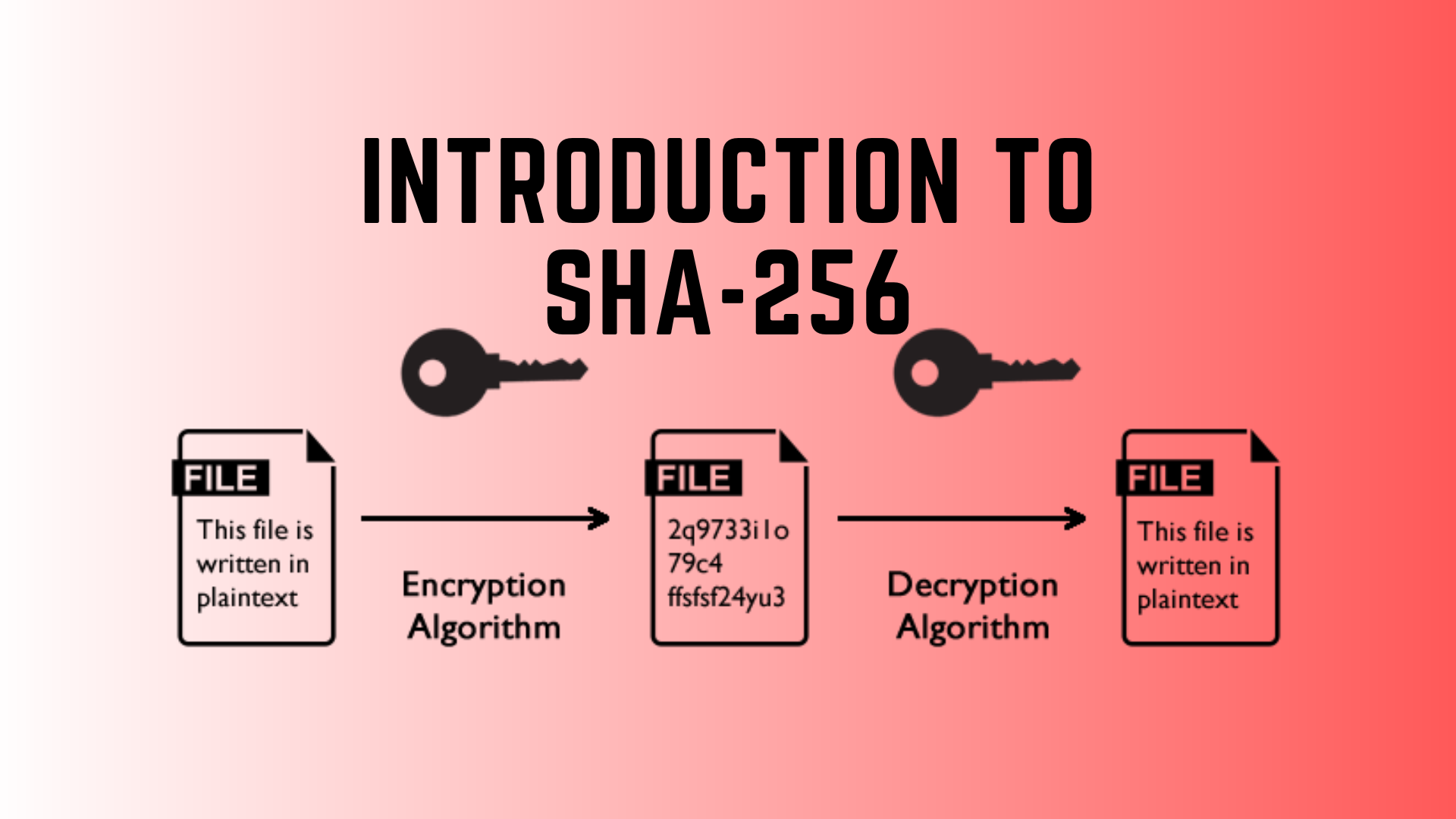
As of 2019, MD5 continues to be widely used, despite its well-documented weaknesses and deprecation by security experts. A collision attack exists that can find collisions within seconds on a computer with a 2.6 GHz Pentium 4 processor (complexity of 224.1).
What are the advantages of SHA-256 over MD5
MD5 produces a 128-bit output, and SHA256 produces a 256-bit output. Generally, the longer the output, the more secure the hash function, as it reduces the chances of collisions (two different inputs producing the same output).collision attacks
Weak security: MD5 produces a fixed-sized 128-bit hash value, which is significantly shorter than modern secure hash functions like SHA-256 or SHA-3. A shorter hash length reduces the resistance against brute-force and collision attacks, increasing the risk of an attacker successfully compromising the data.In terms of speed, the MD5 is slightly faster than SHA-2. Therefore, the MD5 is often used as a checksum for verifying files integrity. To sum up, in most cases, SHA-2 will do better than MD5. It's more secure, reliable, and less likely to be broken.
Vulnerabilities: The MD5 algorithm has long been considered insecure for cryptographic purposes due to significant vulnerabilities. Researchers have demonstrated practical collision attacks against MD5, which allows for the creation of different inputs that produce the same hash value.
Is MD5 still usable : MD5 is still being used today as a hash function even though it has been exploited for years.
Why is MD5 no longer used : Historically it was widely used as a cryptographic hash function; however it has been found to suffer from extensive vulnerabilities.
How fast is SHA-256 vs MD5
The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits. While not quite perfect, current research indicates it is considerably more secure than either MD5 or SHA-1. Performance-wise, a SHA-256 hash is about 20-30% slower to calculate than either MD5 or SHA-1 hashes.

The conclusion is that SHA-2 does better than MD5 in most cases, especially regarding security. On the other hand, MD5 can be used in solutions that don't require a high level of security and when speed is the main criteria.Probably the one most commonly used is SHA-256, which the National Institute of Standards and Technology (NIST) recommends using instead of MD5 or SHA-1. The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits.
Why is MD5 good : Meanwhile, MD5 is a secure hash algorithm and a cryptographic hash function that can detect some data corruption but is primarily intended for the secure encryption of data that is being transmitted and the verification of digital certificates.