Hashes provide security to an organization's cyber system so that hackers cannot steal it; for example, email passwords stored on servers.For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
Is hashing one-way encryption : Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value.
Is sha256 hash safe
Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
How is hashing safe : Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation. Even if an attacker obtains the hashed password, they cannot use it to log in as the victim.
No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity. Hashing is generally a one-way function, which means that it is easy to convert a message into a hash but very difficult to “reverse hash” a hash value back to its original message as it requires a massive amount of computing power.
Is hashed data GDPR compliant
Under the European General Data Protection Regulation (GDPR), hashed passwords are categorized as personal information. GDPR and the National Institute of Standards and Technology (NIST) advise against using some hash algorithms. Conversely, U.S. law recognizes hashing as a secure, de-identified data point.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken". Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.
Why is hashing insecure : Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.
Can hashed data be recovered : Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.
Can hashed passwords be hacked
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted. Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.One of the most misunderstood topics in privacy is what it means to provide “anonymous” access to data. One often hears references to “hashing” as a way of rendering data anonymous. As it turns out, hashing is vastly overrated as an “anonymization” technique.
Is SHA-256 still safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
Antwort Is hashed data safe? Weitere Antworten – Are hashes secure
Hashes provide security to an organization's cyber system so that hackers cannot steal it; for example, email passwords stored on servers.For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
Is hashing one-way encryption : Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value.
Is sha256 hash safe
Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.
How is hashing safe : Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation. Even if an attacker obtains the hashed password, they cannot use it to log in as the victim.
No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
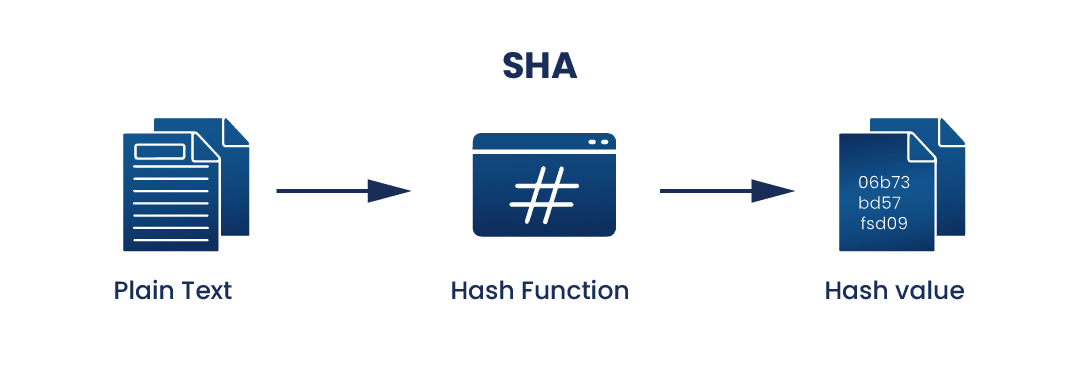
Hashing is generally a one-way function, which means that it is easy to convert a message into a hash but very difficult to “reverse hash” a hash value back to its original message as it requires a massive amount of computing power.
Is hashed data GDPR compliant
Under the European General Data Protection Regulation (GDPR), hashed passwords are categorized as personal information. GDPR and the National Institute of Standards and Technology (NIST) advise against using some hash algorithms. Conversely, U.S. law recognizes hashing as a secure, de-identified data point.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
:max_bytes(150000):strip_icc()/hash.asp-final-f341f429ebc1421ab167f2f97609b5eb.png)
Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.
Why is hashing insecure : Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.
Can hashed data be recovered : Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.
Can hashed passwords be hacked
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.

Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.One of the most misunderstood topics in privacy is what it means to provide “anonymous” access to data. One often hears references to “hashing” as a way of rendering data anonymous. As it turns out, hashing is vastly overrated as an “anonymization” technique.
Is SHA-256 still safe : Many consider SHA-256 to be one of the most secure hashing algorithms today. This is because it's great at preventing values from being reversed back to the original content. Another problem that it solves well is avoiding hashing collisions. This means that two separate inputs cannot produce an identical hash.