A Blockchain hash is a digitized fingerprint of a document or set of data. It is used to verify whether or not that information has been tampered with or changed in any way. A Blockchain hash is generated via a cryptographic function that compares an input block of data with a previously generated hash value.At the heart of Bitcoin mining is the hash. The hash is a 64-digit hexadecimal number that is the result of sending the information contained in a block through the SHA256 hashing algorithm.SHA-256
SHA-256: This is one of the most commonly used hash functions in distributed ledgers, and it is the one used by Bitcoin. SHA-256 generates a 256-bit hash value that is unique to the data being hashed.
What is the difference between hash and crypto : Basically, encryption is the process of scrambling plaintext into unreadable ciphertext, which you can decrypt with a relevant key, while hashing turns plain text into a unique code, which can't be reverted into a readable form.
How much is crypto hash
Hash price is a term coined by Bitcoin mining services firm Luxor, referring to the expected value of 1 PH/s or 1 TH/s of hashing power per day. The metric quantifies how much a miner can expect to earn from a specific quantity of hash rate.
Is crypto mining legal : Is Bitcoin Mining Legal In many jurisdictions, Bitcoin mining is legal. However, there are still some countries where it is illegal, so it's important to check the activity's status in your country before you start mining.
You can also use a blockchain explorer to look up the transaction hash. A blockchain explorer is a tool that allows you to view the transaction history and other details for a specific cryptocurrency address. By entering the address for the transaction, you can find the corresponding hash. Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.
What is a cryptographic hash function
A cryptographic hash function (CHF) is an equation used to verify the validity of data. It has many applications, notably in information security (e.g. user authentication). A CHF translates data of various lengths — the message — into a fixed size numerical string — the hash.Ethereum uses the Keccak-256 cryptographic hash function in many places.md5-crypt hashes
$1$ is the prefix used to identify md5-crypt hashes, following the Modular Crypt Format. salt is 0-8 characters drawn from the regexp range [./0-9A-Za-z] ; providing a 48-bit salt ( 5pZSV9va in the example). The output size in bits is given by the extension to the "SHA" name, so SHA-224 has an output size of 224 bits (28 bytes); SHA-256, 32 bytes; SHA-384, 48 bytes; and SHA-512, 64 bytes.
Is crypto mining like gambling : Some 'analysts' have even compared Bitcoin 'mining' to gold mining. However, put bluntly, Bitcoin is a volatile gamble meant for those who can afford to lose money.
Is anyone still mining crypto : There are many people and wealthy organizations engaged in the activity, making it difficult for all but a few to reap the legendary rewards mining bitcoin used to promise. However, this doesn't mean you can't make money mining bitcoin—it just won't be as lucrative as you would like.
What is crypto ID hash
What is a transaction hash/hash ID A transaction hash is a string of letters and numbers that is generated when a cryptocurrency transaction is initiated. It is a unique identifier that is used to track the transaction on the blockchain. What's the Most Secure Hashing Algorithm SHA-256. SHA-256 (secure hash algorithm) is an algorithm that takes an input of any length and uses it to create a 256-bit fixed-length hash value.SHA-256 is one of the successor hash functions to SHA-1 (collectively referred to as SHA-2), and is one of the strongest hash functions available. SHA-256 is not much more complex to code than SHA-1, and has not yet been compromised in any way. The 256-bit key makes it a good partner-function for AES.
What type of cryptography is hashing : A cryptographic hash function is a mathematical function used in cryptography. Typical hash functions take inputs of variable lengths to return outputs of a fixed length. A cryptographic hash function combines the message-passing capabilities of hash functions with security properties.
Antwort Is crypto a hash? Weitere Antworten – What is hash in cryptocurrency
A Blockchain hash is a digitized fingerprint of a document or set of data. It is used to verify whether or not that information has been tampered with or changed in any way. A Blockchain hash is generated via a cryptographic function that compares an input block of data with a previously generated hash value.At the heart of Bitcoin mining is the hash. The hash is a 64-digit hexadecimal number that is the result of sending the information contained in a block through the SHA256 hashing algorithm.SHA-256
SHA-256: This is one of the most commonly used hash functions in distributed ledgers, and it is the one used by Bitcoin. SHA-256 generates a 256-bit hash value that is unique to the data being hashed.
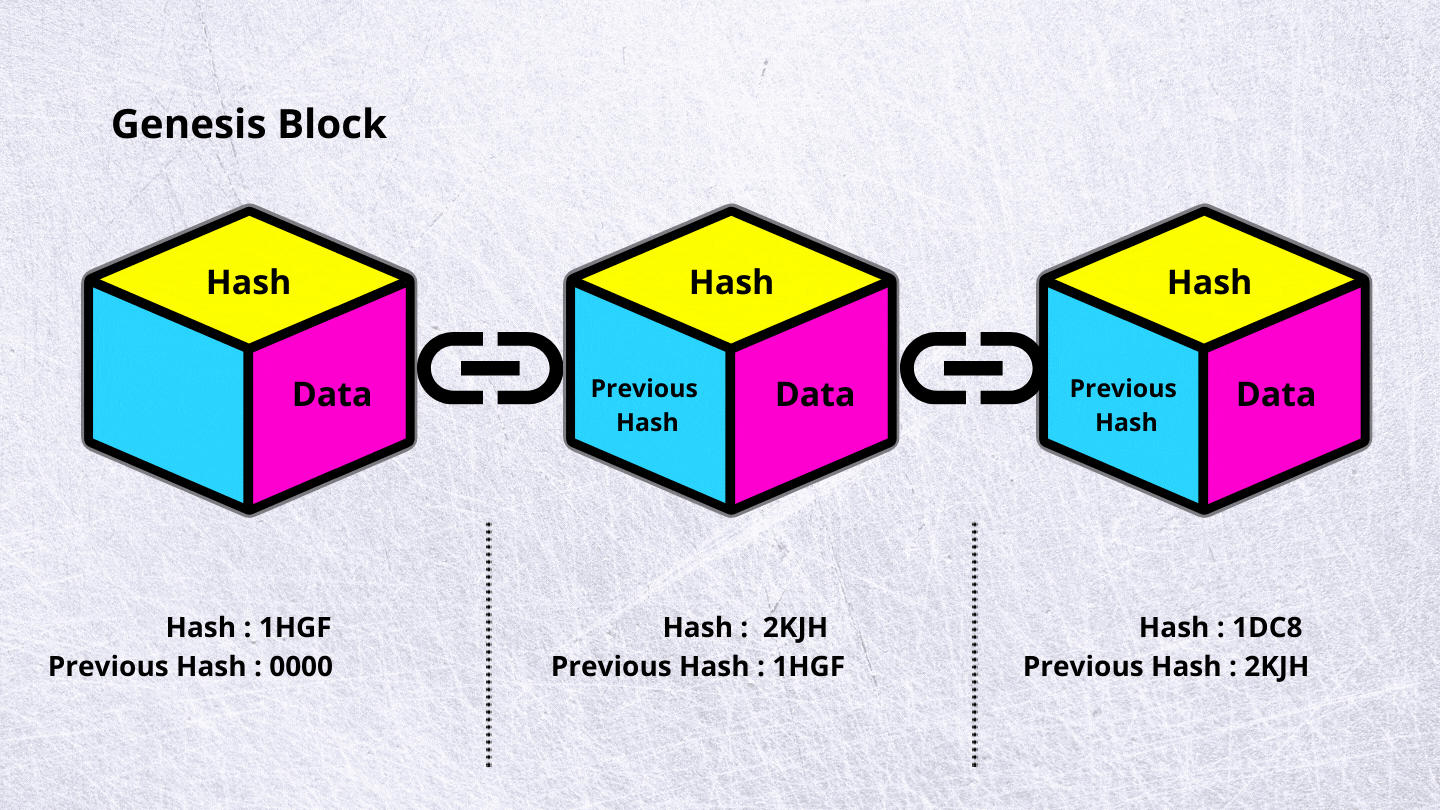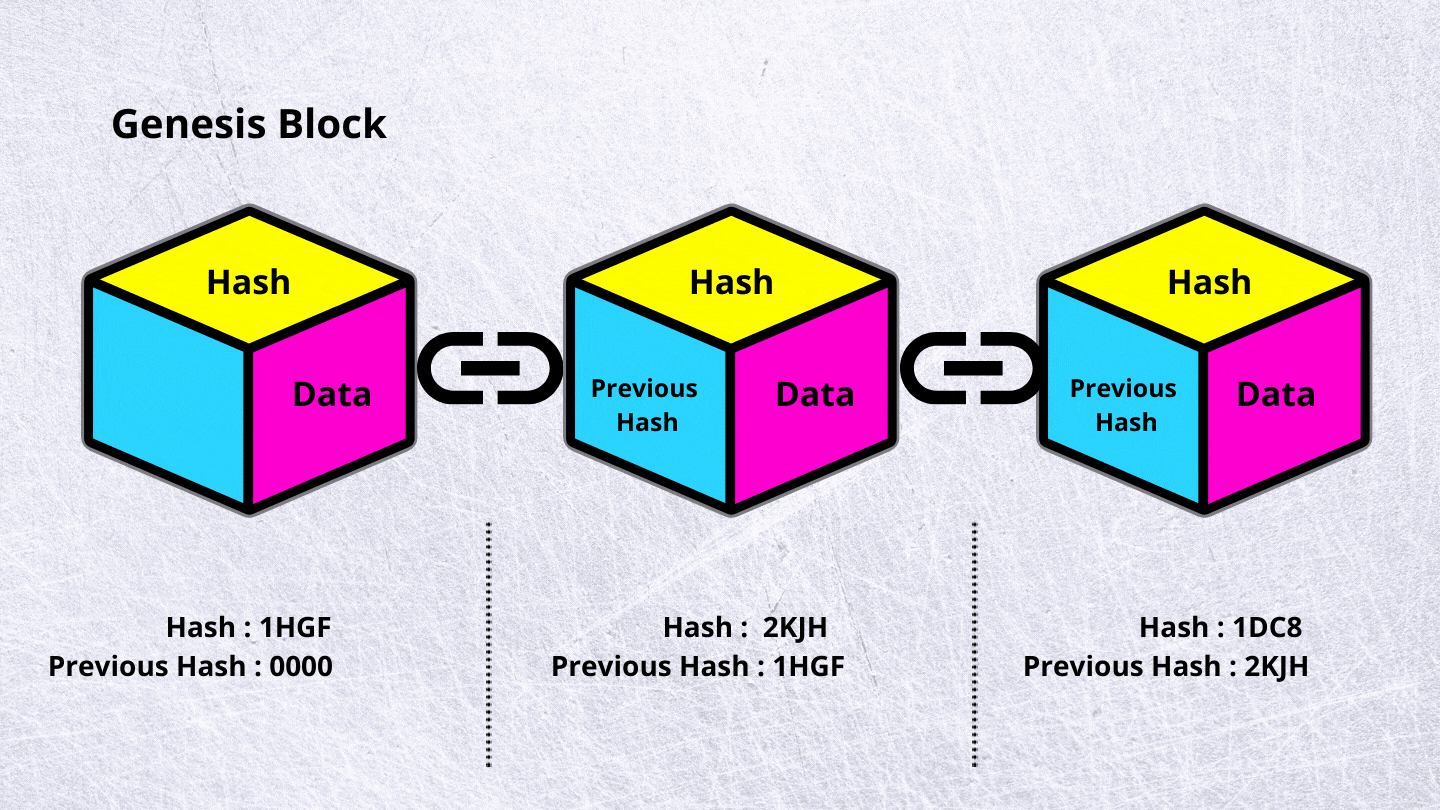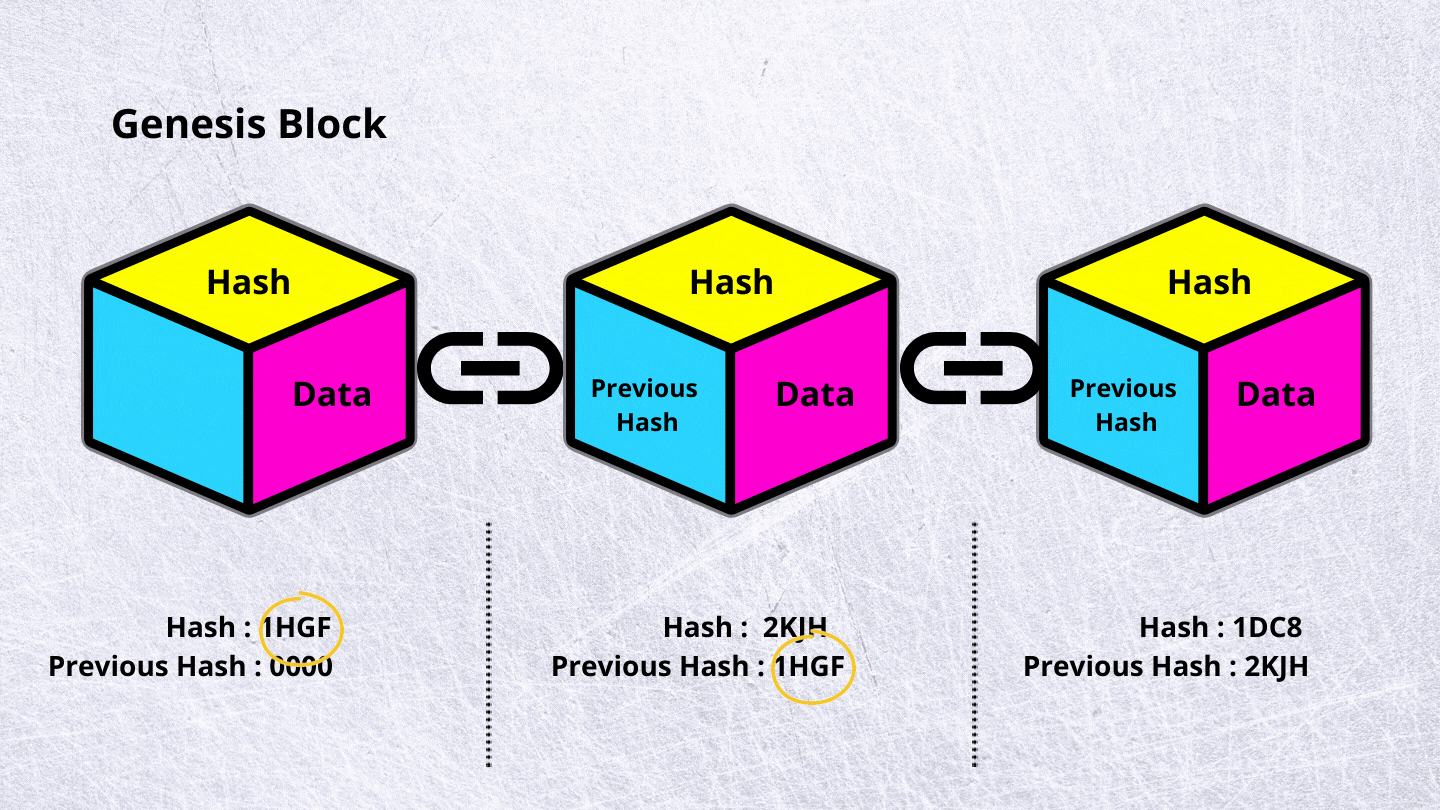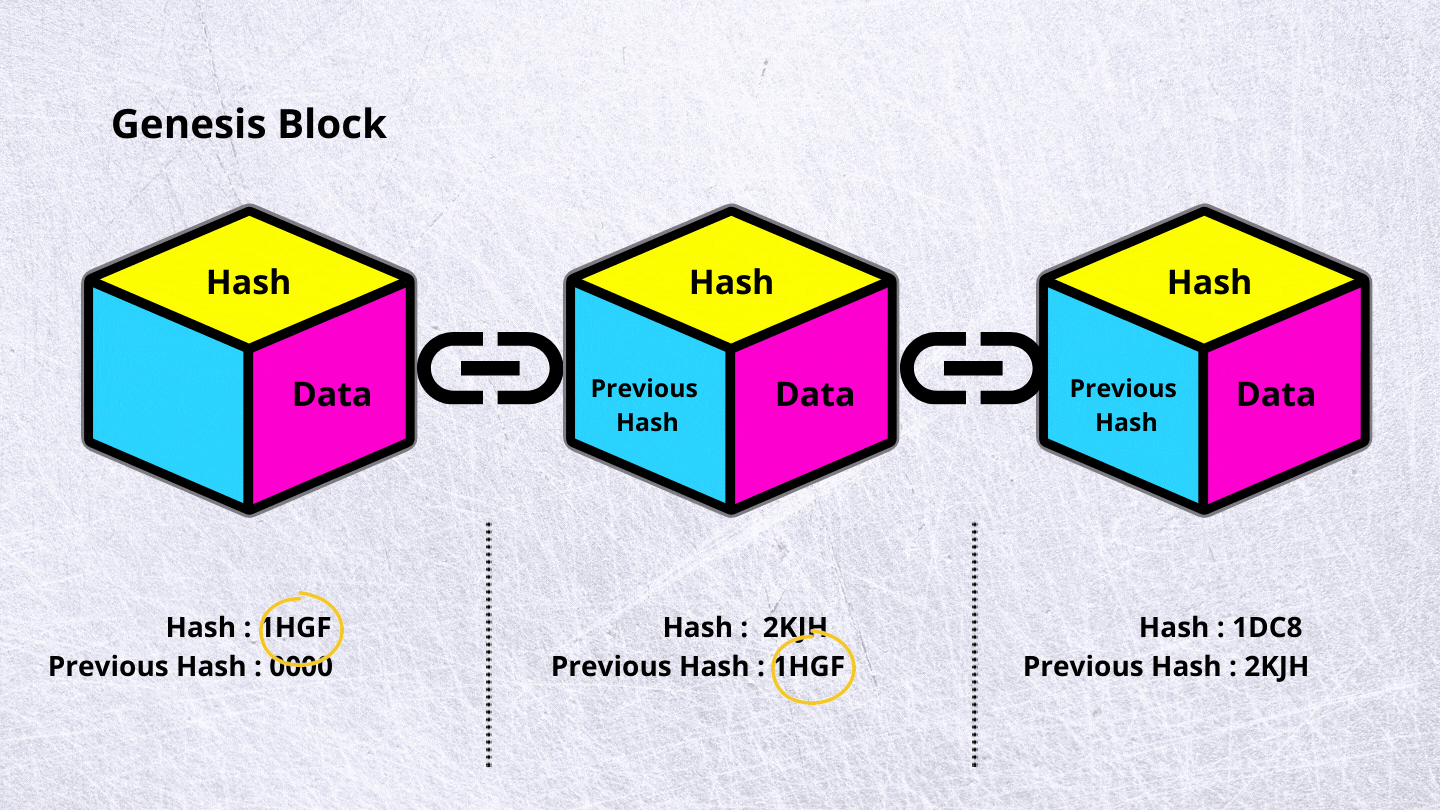
What is the difference between hash and crypto : Basically, encryption is the process of scrambling plaintext into unreadable ciphertext, which you can decrypt with a relevant key, while hashing turns plain text into a unique code, which can't be reverted into a readable form.
How much is crypto hash
Hash price is a term coined by Bitcoin mining services firm Luxor, referring to the expected value of 1 PH/s or 1 TH/s of hashing power per day. The metric quantifies how much a miner can expect to earn from a specific quantity of hash rate.
Is crypto mining legal : Is Bitcoin Mining Legal In many jurisdictions, Bitcoin mining is legal. However, there are still some countries where it is illegal, so it's important to check the activity's status in your country before you start mining.
You can also use a blockchain explorer to look up the transaction hash. A blockchain explorer is a tool that allows you to view the transaction history and other details for a specific cryptocurrency address. By entering the address for the transaction, you can find the corresponding hash.
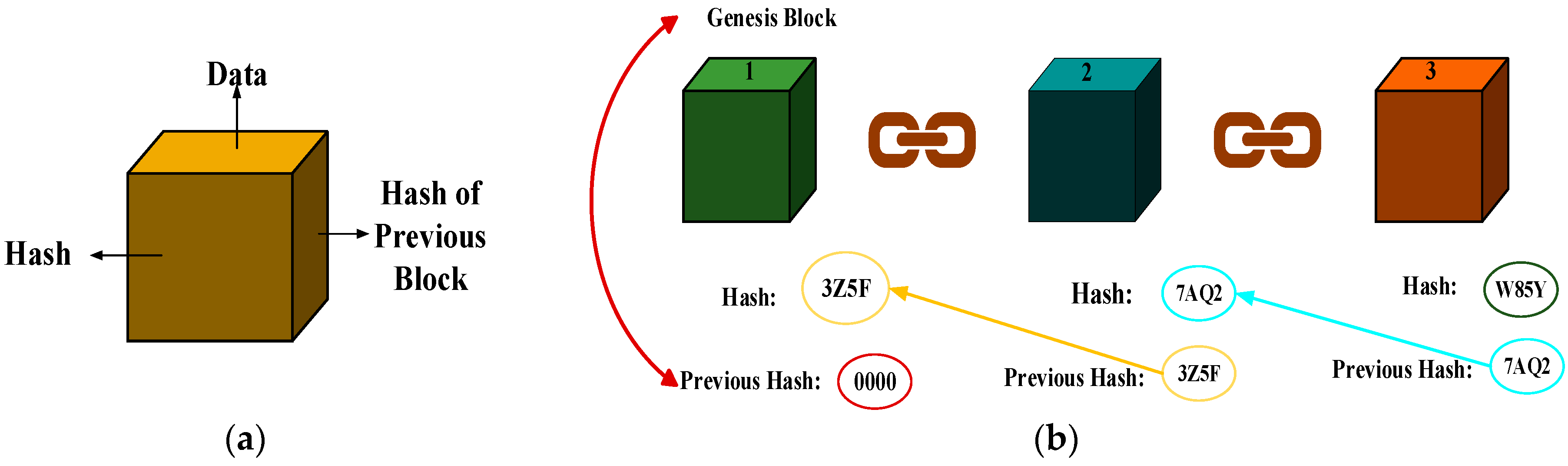
Hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. For example, if we have a list of 10,000 words of English and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match.
What is a cryptographic hash function
A cryptographic hash function (CHF) is an equation used to verify the validity of data. It has many applications, notably in information security (e.g. user authentication). A CHF translates data of various lengths — the message — into a fixed size numerical string — the hash.Ethereum uses the Keccak-256 cryptographic hash function in many places.md5-crypt hashes
$1$ is the prefix used to identify md5-crypt hashes, following the Modular Crypt Format. salt is 0-8 characters drawn from the regexp range [./0-9A-Za-z] ; providing a 48-bit salt ( 5pZSV9va in the example).
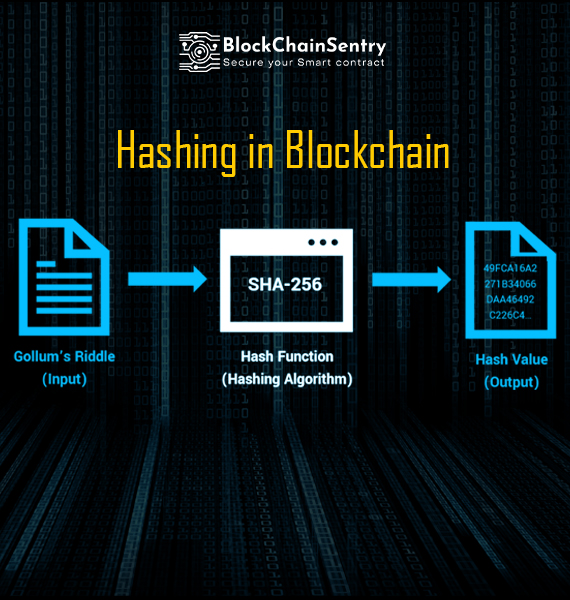
The output size in bits is given by the extension to the "SHA" name, so SHA-224 has an output size of 224 bits (28 bytes); SHA-256, 32 bytes; SHA-384, 48 bytes; and SHA-512, 64 bytes.
Is crypto mining like gambling : Some 'analysts' have even compared Bitcoin 'mining' to gold mining. However, put bluntly, Bitcoin is a volatile gamble meant for those who can afford to lose money.
Is anyone still mining crypto : There are many people and wealthy organizations engaged in the activity, making it difficult for all but a few to reap the legendary rewards mining bitcoin used to promise. However, this doesn't mean you can't make money mining bitcoin—it just won't be as lucrative as you would like.
What is crypto ID hash
What is a transaction hash/hash ID A transaction hash is a string of letters and numbers that is generated when a cryptocurrency transaction is initiated. It is a unique identifier that is used to track the transaction on the blockchain.

What's the Most Secure Hashing Algorithm SHA-256. SHA-256 (secure hash algorithm) is an algorithm that takes an input of any length and uses it to create a 256-bit fixed-length hash value.SHA-256 is one of the successor hash functions to SHA-1 (collectively referred to as SHA-2), and is one of the strongest hash functions available. SHA-256 is not much more complex to code than SHA-1, and has not yet been compromised in any way. The 256-bit key makes it a good partner-function for AES.
What type of cryptography is hashing : A cryptographic hash function is a mathematical function used in cryptography. Typical hash functions take inputs of variable lengths to return outputs of a fixed length. A cryptographic hash function combines the message-passing capabilities of hash functions with security properties.