Check your social media, email, and other accounts for suspicious logins or devices that you don't recognize. For example, you can use Google's Activity Log to see if anyone is logged into your Gmail account and then force them to sign out.Unusual account activity like emails marked as read that you didn't read, emails in your Sent Folder that you didn't send, or contacts receiving unusual messages from your account can also indicate a hacked email account.If attackers obtain physical access to your phone or computer, they can install malicious software and monitor the device's screen activity.
Can hackers be detected : Hacker attacks may use a single specific exploit, several exploits at the same time, a misconfiguration in one of the system components or even a backdoor from an earlier attack. Due to this, detecting hacker attacks is not an easy task, especially for an inexperienced user.
What is the first thing you do when you get hacked
Immediately change all your passwords on any accounts you think might have been affected. If you use the same password across several accounts, make sure they're unique from now on. Regularly changing your passwords is also a good habit to get into.
How do hackers view your phone : Keylogging: In the hands of a hacker, keylogging works like a stalker by snooping information as you type, tap, and even talk on your phone. Trojans: Trojans are types of malware that can be disguised in your phone to extract important data, such as credit card account details or personal information.
Hackers can also use keyloggers and other tracking software to capture your phone's keystrokes and record what you type, such as search queries, login credentials, passwords, credit card details, and other sensitive information. Criminal Penalties Under the CFAA
Offense
Penalties (Prison Sentence)
Accessing a Computer and Obtaining Information
First conviction: Up to one year Second conviction: Up to 10 years
Intentionally Damaging by Knowing Transmission
First conviction: Up to 10 years Second conviction: Up to 20 years
How do hackers find you
Social media: Hackers can build a profile on someone simply by studying their public social media profiles. These profiles often include the person's name, workplace, names of relatives and friends, birthdate, etc. A common form of hacking includes the impersonation of someone they have profiled.If you're a victim of identity theft, it can have a direct affect on anything from your social media and email accounts to your personal finances, and could also make it difficult for you to get things like loans, credit cards or a mortgage until the problem is resolved.If attackers obtain physical access to your phone or computer, they can install malicious software and monitor the device's screen activity. Yes, hackers can potentially gain access to your phone's screen and see what you're doing, especially if your phone is infected with malware or if you've installed a compromised app.
Can you remove a hacker from your phone : Get a hacker off your phone with antivirus software
Android antivirus software promptly quarantines malicious code used to compromise your phone, then safely removes it so it can do no harm.
Do hackers actually get caught : So, How Do Hackers Get Caught Despite what may seem like an insurmountable task, hackers are human and make mistakes. It's often these careless errors that will trip the criminals up and leave a trail of evidence that the police can follow.
Is it illegal to be a hacker
Computer Fraud and Abuse Act. In 1986, Congress passed the Computer Fraud and Abuse Act (CFAA), now codified under Title 18 U.S. Code § 1030. This law makes it a federal crime to gain unauthorized access to “protected” computers (otherwise known as “hacking”) with the intent to defraud or do damage. Hackers are always eager to infect your device with malware and trojans. By installing keyloggers on your phone, a cybercriminal can monitor your activity and secretly view your login data for websites and apps.In some cases, hackers use scareware and phishing tactics to install illegitimate apps that contain spyware on people's phones. Then, the spyware runs in the background, allowing the hacker to continuously monitor and record the user's activity, including everything they type.
Can hackers go to jail : Practically speaking, any computer connected to the internet is a protected computer. Hacking a protected computer is a federal crime. So, the federal government, through its federal prosecutors, may bring charges against hackers. Depending on the computer hacking charges, it may result in a felony or misdemeanor.
Antwort How will I know if I’m hacked? Weitere Antworten – Where can I check if I have been hacked
Check your social media, email, and other accounts for suspicious logins or devices that you don't recognize. For example, you can use Google's Activity Log to see if anyone is logged into your Gmail account and then force them to sign out.Unusual account activity like emails marked as read that you didn't read, emails in your Sent Folder that you didn't send, or contacts receiving unusual messages from your account can also indicate a hacked email account.If attackers obtain physical access to your phone or computer, they can install malicious software and monitor the device's screen activity.
Can hackers be detected : Hacker attacks may use a single specific exploit, several exploits at the same time, a misconfiguration in one of the system components or even a backdoor from an earlier attack. Due to this, detecting hacker attacks is not an easy task, especially for an inexperienced user.
What is the first thing you do when you get hacked
Immediately change all your passwords on any accounts you think might have been affected. If you use the same password across several accounts, make sure they're unique from now on. Regularly changing your passwords is also a good habit to get into.
How do hackers view your phone : Keylogging: In the hands of a hacker, keylogging works like a stalker by snooping information as you type, tap, and even talk on your phone. Trojans: Trojans are types of malware that can be disguised in your phone to extract important data, such as credit card account details or personal information.
Hackers can also use keyloggers and other tracking software to capture your phone's keystrokes and record what you type, such as search queries, login credentials, passwords, credit card details, and other sensitive information.

Criminal Penalties Under the CFAA
How do hackers find you
Social media: Hackers can build a profile on someone simply by studying their public social media profiles. These profiles often include the person's name, workplace, names of relatives and friends, birthdate, etc. A common form of hacking includes the impersonation of someone they have profiled.If you're a victim of identity theft, it can have a direct affect on anything from your social media and email accounts to your personal finances, and could also make it difficult for you to get things like loans, credit cards or a mortgage until the problem is resolved.If attackers obtain physical access to your phone or computer, they can install malicious software and monitor the device's screen activity.

Yes, hackers can potentially gain access to your phone's screen and see what you're doing, especially if your phone is infected with malware or if you've installed a compromised app.
Can you remove a hacker from your phone : Get a hacker off your phone with antivirus software
Android antivirus software promptly quarantines malicious code used to compromise your phone, then safely removes it so it can do no harm.
Do hackers actually get caught : So, How Do Hackers Get Caught Despite what may seem like an insurmountable task, hackers are human and make mistakes. It's often these careless errors that will trip the criminals up and leave a trail of evidence that the police can follow.
Is it illegal to be a hacker
Computer Fraud and Abuse Act. In 1986, Congress passed the Computer Fraud and Abuse Act (CFAA), now codified under Title 18 U.S. Code § 1030. This law makes it a federal crime to gain unauthorized access to “protected” computers (otherwise known as “hacking”) with the intent to defraud or do damage.
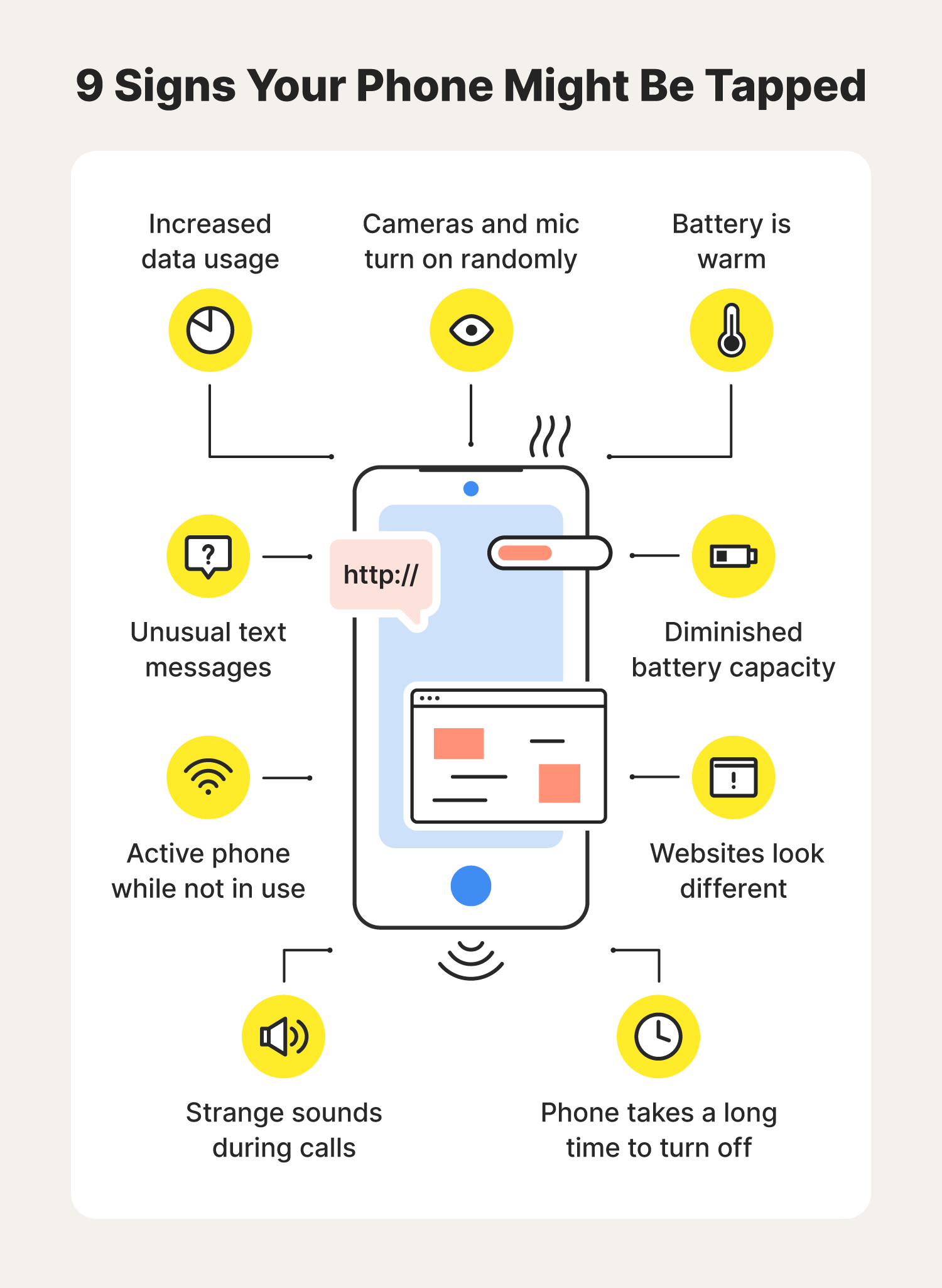
Hackers are always eager to infect your device with malware and trojans. By installing keyloggers on your phone, a cybercriminal can monitor your activity and secretly view your login data for websites and apps.In some cases, hackers use scareware and phishing tactics to install illegitimate apps that contain spyware on people's phones. Then, the spyware runs in the background, allowing the hacker to continuously monitor and record the user's activity, including everything they type.
Can hackers go to jail : Practically speaking, any computer connected to the internet is a protected computer. Hacking a protected computer is a federal crime. So, the federal government, through its federal prosecutors, may bring charges against hackers. Depending on the computer hacking charges, it may result in a felony or misdemeanor.