Click on the output box to get copy the code to your clipboard.
You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
Step-by-Step Process of SHA-256
Input: The process starts with the input data—be it a password, a file, or a message.
Padding: The binary data is 'padded' to ensure it fits into a 512-bit block.
Dividing: Next, the padded data is divided into 512-bit blocks.
How to get SHA-256 hash of file in Linux : Linux
Go to the directory where your downloaded file is stored, e.g.: cd home/downloads.
Use the following command to generate the checksum: sha256sum my_file.exe. Make sure to replace my_file.exe with the actual name of the file.
Compare the generated value to the checksum of the file in Rublon Downloads.
Is SHA-256 still secure
It is worth noting again that SHA256 is not the only secure hash function available. There are other hash functions, such as SHA3, that provide even better security than SHA256. However, SHA256 is widely used and has been extensively tested, making it a good choice for most use cases.
What is a SHA-256 hash generator : SHA-256 is an algorithm that converts a string of text into another string, called a hash. The hash is always the same length: exactly 64 hexadecimal characters long.
How to Hash a File in One Minute
Open Windows Command Line. In your Start bar, type CMD and press Enter to open Windows Command Line.
Decide which hashing algorithm you want to use. Different hash functions (i.e., hashing algorithms) suit different needs and purposes.
Hash a file using the certutil -hashfile command.
The key k will be the constant value between 0 and 1, and A will be any constant value between 0 and 1. Both k and A are multiplied, and their fractional part is separated using the modulus operator. This is then multiplied with n to get the hash value.
Is SHA-256 a hash algorithm
The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.
Open a command prompt window by clicking Start >> Run, and typing in CMD.exe and hitting Enter.
Navigate to the path of the sha256sum.exe application.
Enter sha256.exe and enter the filename of the file you are checking.
Hit enter, a string of 64 characters will be displayed.
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. Currently, SHA-2 hashing is widely used, as it is considered the most secure hashing algorithm in the cryptographic arena.
SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
Is SHA-256 strong enough : SHA-256, a SHA-2 (Secure Hash Algorithm 2) family member, is a robust and secure hash function compared to SHA-1. It produces a hash value of 256 bits. The double length of the output results in a stronger secure hash function, making it more secure against brute force attacks.
Can we hash a file : As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.
How to MD5 hash a file
Solution:
Open the Windows command line. Press Windows + R, type cmd and press Enter.
Go to the folder that contains the file whose MD5 checksum you want to check and verify. Command: Type cd followed by the path to the folder.
Type the command below certutil -hashfile <file> MD5.
Press Enter.
Most hashing algorithms follow this process:
Create the message. A user determines what should be hashed.
Choose the type. Dozens of hashing algorithms exist, and the user might decide which works best for this message.
Enter the message.
Start the hash.
Store or share.
The simplest example of a hash function encodes the input in the same way as the output range and then discards all that exceeds the output range. For example if the output range of the hash function is 0–9 then we can interpret all input as an (base 10) integer and discard all but the last digit.
Why use SHA-256 hash : The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.
Antwort How to hash using SHA-256? Weitere Antworten – How to create a hash using SHA-256
How to use the SHA-256 hash generator
You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Step-by-Step Process of SHA-256
How to get SHA-256 hash of file in Linux : Linux
Is SHA-256 still secure
It is worth noting again that SHA256 is not the only secure hash function available. There are other hash functions, such as SHA3, that provide even better security than SHA256. However, SHA256 is widely used and has been extensively tested, making it a good choice for most use cases.
What is a SHA-256 hash generator : SHA-256 is an algorithm that converts a string of text into another string, called a hash. The hash is always the same length: exactly 64 hexadecimal characters long.
How to Hash a File in One Minute
The key k will be the constant value between 0 and 1, and A will be any constant value between 0 and 1. Both k and A are multiplied, and their fractional part is separated using the modulus operator. This is then multiplied with n to get the hash value.
Is SHA-256 a hash algorithm
The secure hash algorithm with a digest size of 256 bits, or the SHA 256 algorithm, is one of the most widely used hash algorithms. While there are other variants, SHA 256 has been at the forefront of real-world applications.
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. Currently, SHA-2 hashing is widely used, as it is considered the most secure hashing algorithm in the cryptographic arena.
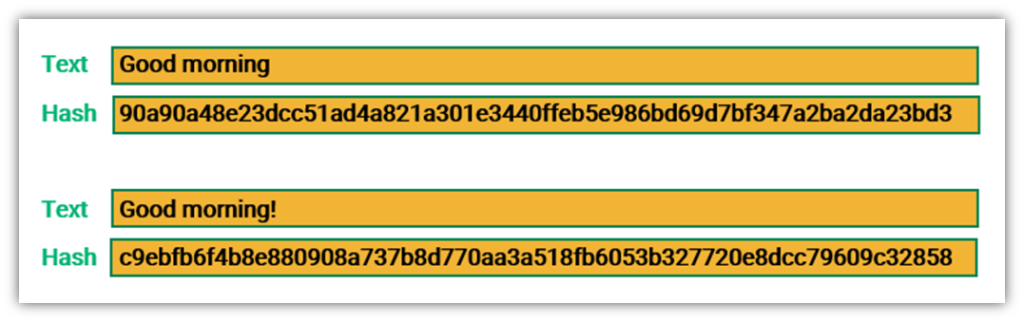
SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
Is SHA-256 strong enough : SHA-256, a SHA-2 (Secure Hash Algorithm 2) family member, is a robust and secure hash function compared to SHA-1. It produces a hash value of 256 bits. The double length of the output results in a stronger secure hash function, making it more secure against brute force attacks.
Can we hash a file : As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.
How to MD5 hash a file
Solution:
Most hashing algorithms follow this process:
The simplest example of a hash function encodes the input in the same way as the output range and then discards all that exceeds the output range. For example if the output range of the hash function is 0–9 then we can interpret all input as an (base 10) integer and discard all but the last digit.
Why use SHA-256 hash : The main reason technology leaders use SHA-256 is that it doesn't have any known vulnerabilities that make it insecure and it has not been “broken” unlike some other popular hashing algorithms. To better understand what this means, we need to look at the history of some other popular hashing algorithms.