All objects that are . equals , must have the same hashCode.
hashCode values should be spread as evenly as possible over all ints.
hashCode should be relatively quick to compute.
hashCode must be deterministic (not random).
A hash function is used to quickly generate a number (hash code) that corresponds to the value of an object. Hash functions are usually specific to each type and, for uniqueness, must use at least one of the instance fields as input. Hash codes should not be computed by using the values of static fields.A hashing algorithm is used to generate the hash code (an integer value) accepting the identification of the nodes as the input. Improved Cross-Layer Detection and Prevention of Sinkhole Attack in WSN.
How do I prepare for hash code : You can find some free, useful, and accessible courses on various platforms online like Coding Ninjas to help you solve these problems better and prepare for the final rounds of the Google HashCode.
Is hash code unique
The hashCode method is designed to return an integer that represents the value of the object. This integer is not unique, but it is generated in a way that helps minimize collisions (two different objects producing the same hash code).
How to generate a hash code for a string : Using a bitwise XOR operation to generate a hash from a string. It iterates over each character, XORs its Unicode value with the current hash, updating it. This approach offers simplicity and efficiency in creating a unique hash.
Hash Tool is a utility to calculate the hash of multiple files. A file hash can be said to be the 'signature' of a file and is used in many applications, including checking the integrity of downloaded files. This compact application helps you quickly and easily list the hashes of your files. Hashing is implemented in two steps:
An element is converted into an integer by using a hash function. This element can be used as an index to store the original element, which falls into the hash table.
The element is stored in the hash table where it can be quickly retrieved using hashed key. hash = hashfunc(key)
How to create a unique hash
To create a unique hash from a specific string, it can be implemented using its own string-to-hash converting function. It will return the hash equivalent of a string. Also, a library named Crypto can be used to generate various types of hashes like SHA1, MD5, SHA256, and many more.Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.The hash code for a String object is computed as s [ 0 ] ∗ 31 n − 1 + s [ 1 ] ∗ 31 n − 2 + . . . + s [ n − 1 ] using int arithmetic, where s[i] is the i th character of the string, and n is the length of the string. (The hash value of the empty string is zero.)” hashCode() method of String class can be used to convert a string into hash code. hashCode() method will return either negative or positive integer hash values. The returned hash value cannot be re-converted back to string once hashed.
How are hashes generated : As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.
How to create file hash : Creating a File Hash List
Go to Policies > File.
Click New File Profile.
In the Add File Profile window, click File Hash.
Select the type of hash to scan for, such as SHA-256 and MD5, and enter the hash values.
Click Next.
Enter a name for the file profile.
Click Save.
Click Apply Changes.
How is hash generated
A hash function generates new values according to a mathematical hashing algorithm, known as a hash value or simply a hash. To prevent the conversion of hash back into the original key, a good hash always uses a one-way hashing algorithm. An MD5 hash is created by taking a string of an any length and encoding it into a 128-bit fingerprint. Encoding the same string using the MD5 algorithm will always result in the same 128-bit hash output.A hash function generates new values according to a mathematical hashing algorithm, known as a hash value or simply a hash. To prevent the conversion of hash back into the original key, a good hash always uses a one-way hashing algorithm.
Is SHA-256 truly random : If you feed SHA-256 with too little entropy (or even smaller input than 256 bits), the output may appear random, but it is not.
Antwort How to generate hash code? Weitere Antworten – How to make a good hash code
A hash function is used to quickly generate a number (hash code) that corresponds to the value of an object. Hash functions are usually specific to each type and, for uniqueness, must use at least one of the instance fields as input. Hash codes should not be computed by using the values of static fields.A hashing algorithm is used to generate the hash code (an integer value) accepting the identification of the nodes as the input. Improved Cross-Layer Detection and Prevention of Sinkhole Attack in WSN.
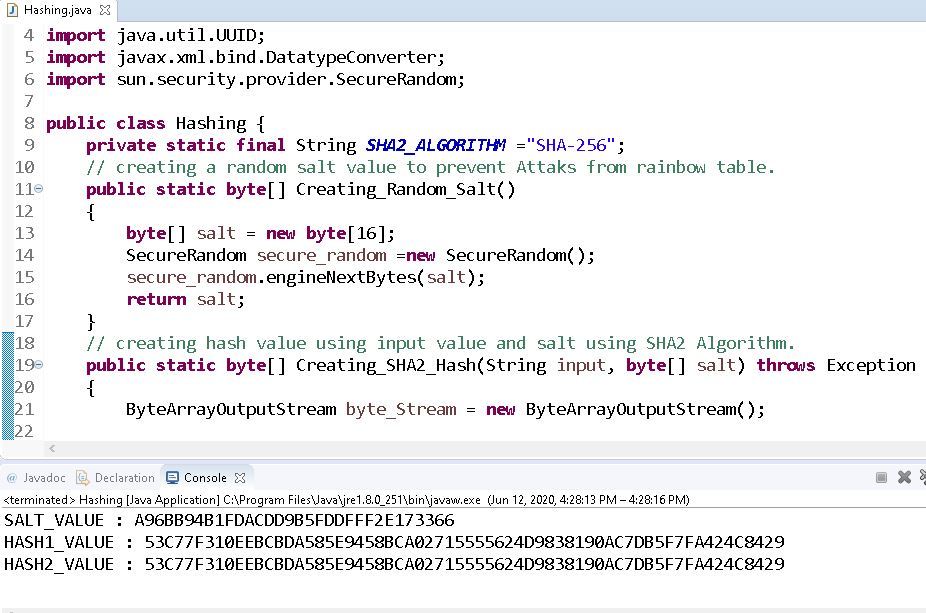
How do I prepare for hash code : You can find some free, useful, and accessible courses on various platforms online like Coding Ninjas to help you solve these problems better and prepare for the final rounds of the Google HashCode.
Is hash code unique
The hashCode method is designed to return an integer that represents the value of the object. This integer is not unique, but it is generated in a way that helps minimize collisions (two different objects producing the same hash code).
How to generate a hash code for a string : Using a bitwise XOR operation to generate a hash from a string. It iterates over each character, XORs its Unicode value with the current hash, updating it. This approach offers simplicity and efficiency in creating a unique hash.
Hash Tool is a utility to calculate the hash of multiple files. A file hash can be said to be the 'signature' of a file and is used in many applications, including checking the integrity of downloaded files. This compact application helps you quickly and easily list the hashes of your files.
Hashing is implemented in two steps:
How to create a unique hash
To create a unique hash from a specific string, it can be implemented using its own string-to-hash converting function. It will return the hash equivalent of a string. Also, a library named Crypto can be used to generate various types of hashes like SHA1, MD5, SHA256, and many more.Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.The hash code for a String object is computed as s [ 0 ] ∗ 31 n − 1 + s [ 1 ] ∗ 31 n − 2 + . . . + s [ n − 1 ] using int arithmetic, where s[i] is the i th character of the string, and n is the length of the string. (The hash value of the empty string is zero.)”

hashCode() method of String class can be used to convert a string into hash code. hashCode() method will return either negative or positive integer hash values. The returned hash value cannot be re-converted back to string once hashed.
How are hashes generated : As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.
How to create file hash : Creating a File Hash List
How is hash generated
A hash function generates new values according to a mathematical hashing algorithm, known as a hash value or simply a hash. To prevent the conversion of hash back into the original key, a good hash always uses a one-way hashing algorithm.

An MD5 hash is created by taking a string of an any length and encoding it into a 128-bit fingerprint. Encoding the same string using the MD5 algorithm will always result in the same 128-bit hash output.A hash function generates new values according to a mathematical hashing algorithm, known as a hash value or simply a hash. To prevent the conversion of hash back into the original key, a good hash always uses a one-way hashing algorithm.
Is SHA-256 truly random : If you feed SHA-256 with too little entropy (or even smaller input than 256 bits), the output may appear random, but it is not.