You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.
What is the weakness of SHA-256 : Advantages and Disadvantages
Advantages
Disadvantages
SHA-256 provides a high level of security, making it practically impossible to derive the original data from its hash value.
Although rare, there is a theoretical possibility of hash collisions, where two different inputs produce the same hash value.
Is SHA-256 still secure
On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
How long does SHA-256 take to crack : SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it. Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Can you do SHA-256 by hand
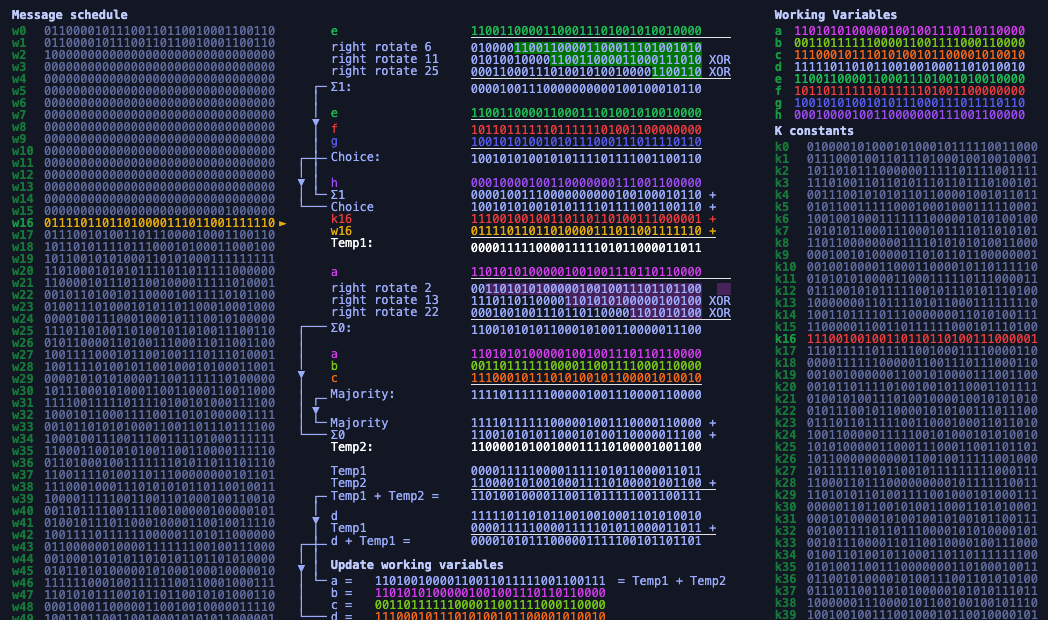
It turns out that the SHA-256 algorithm used for mining is pretty simple and can in fact be done by hand. Not surprisingly, the process is extremely slow compared to hardware mining and is entirely impractical. But performing the algorithm manually is a good way to understand exactly how it works.By making a guess at a password, the attacker can compare the output of his SHA-256 against the SHA-256 that he finds in the database. And because passwords are so short, testing many password guesses this way is easy for a computer.SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue. Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.
Why SHA-256 cannot be decrypted : There is a difference between hashing and encryption. SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Is it possible to crack 256-bit encryption : AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities.
How long does SHA256 take to crack
SHA-256 cracking performance with CPU machine. Using uppercase only character (u) it takes 15sec for 6-character long password HELLO to crack where 8-character long password “MYSECRET” takes 20 mins and it finishes checking all the combination of 8 characters roughly in 38 mins. Since hash values tend to be a fixed length, typically 256 or 512 bits, there are more possible passwords than there are possible hash values, so some passwords must hash to the same value. This cannot be prevented without restricting the size of passwords and/or increasing the size of hash values.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Is Sha 256 still good : SHA256 provides better security and is the recommended hash function for these use cases. If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one.
Antwort How SHA-256 works step by step? Weitere Antworten – How to use SHA-256
You can use Windows Powershell to calculate the SHA-256 checksum for a file.
SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.
What is the weakness of SHA-256 : Advantages and Disadvantages
Is SHA-256 still secure
On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.
How long does SHA-256 take to crack : SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.

Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Can you do SHA-256 by hand
It turns out that the SHA-256 algorithm used for mining is pretty simple and can in fact be done by hand. Not surprisingly, the process is extremely slow compared to hardware mining and is entirely impractical. But performing the algorithm manually is a good way to understand exactly how it works.By making a guess at a password, the attacker can compare the output of his SHA-256 against the SHA-256 that he finds in the database. And because passwords are so short, testing many password guesses this way is easy for a computer.SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.
Why SHA-256 cannot be decrypted : There is a difference between hashing and encryption. SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Is it possible to crack 256-bit encryption : AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities.
How long does SHA256 take to crack
SHA-256 cracking performance with CPU machine. Using uppercase only character (u) it takes 15sec for 6-character long password HELLO to crack where 8-character long password “MYSECRET” takes 20 mins and it finishes checking all the combination of 8 characters roughly in 38 mins.

Since hash values tend to be a fixed length, typically 256 or 512 bits, there are more possible passwords than there are possible hash values, so some passwords must hash to the same value. This cannot be prevented without restricting the size of passwords and/or increasing the size of hash values.Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Is Sha 256 still good : SHA256 provides better security and is the recommended hash function for these use cases. If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one.