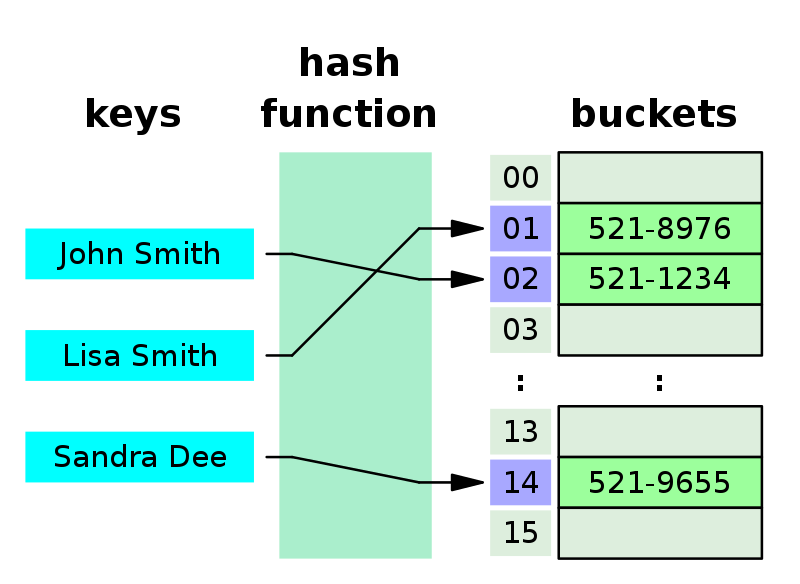
Hashing uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map. For example, in hash tables, developers store data — perhaps a customer record — in the form of key and value pairs.Hashing is implemented in two steps: An element is converted into an integer by using a hash function. This element can be used as an index to store the original element, which falls into the hash table. The element is stored in the hash table where it can be quickly retrieved using hashed key.The hash function translates the key associated with each datum or record into a hash code, which is used to index the hash table. When an item is to be added to the table, the hash code may index an empty slot (also called a bucket), in which case the item is added to the table there.
What is hashing in simple terms : Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.
How is hashCode generated
Hashcode is a unique code generated by the JVM at time of object creation. It can be used to perform some operation on hashing related algorithms like hashtable, hashmap etc. An object can also be searched with this unique code. Returns: It returns an integer value which represents hashCode value for this Method.
Are all hash codes unique : A hash code (MD5, SHA-1, SHA-256) is of a fixed length, so it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the likelihood of a collision (two distinct files with the same hash value).
HashMap Internal Working
The hash code is used to determine the index in the array where the key-value pair should be stored. The hash code is typically used to compute the remainder of the hash code divided by the size of the array, which ensures that the index is within the bounds of the array. Hashing algorithms can be used to authenticate data. The writer uses a hash to secure the document when it's complete. The hash works a bit like a seal of approval. A recipient can generate a hash and compare it to the original.
How do hash functions work
A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).This can be accomplished with a quick application of a conditional operator, as seen below. public final class Boolean { private final boolean value; … public int hashCode() { return hashCode(value); } … public static int hashCode(boolean value) { return value 1231 : 1237; } … }One, hashing is a one-way function. It can be used on any input data to generate a hash value. But, applying a hash function to a hash value will not reveal the input data. Second, hashing always produces a fixed-length hash value, irrespective of the length/ size of the input. Understanding How hashCode() Works
Simply put, hashCode() returns an integer value, generated by a hashing algorithm. Objects that are equal (according to their equals()) must return the same hash code.
How are hash functions generated : A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).
Can two hash codes be equal : If two objects have the same hashcode then they are NOT necessarily equal. Otherwise you will have discovered the perfect hash function. But the opposite is true: if the objects are equal, then they must have the same hashcode .
Is every SHA256 hash unique
Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique. What is a Hashing Algorithm Hashes are the output of a hashing algorithm like MD5 (Message Digest 5) or SHA (Secure Hash Algorithm). These algorithms essentially aim to produce a unique, fixed-length string – the hash value, or “message digest” – for any given piece of data or “message”.Hashing is simply passing some data through a formula that produces a result, called a hash. That hash is usually a string of characters and the hashes generated by a formula are always the same length, regardless of how much data you feed into it. For example, the MD5 formula always produces 32 character-long hashes.
How does hashing work mathematically : What is a Hash Function A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).
Antwort How hash code works? Weitere Antworten – How do hash codes work
Hashing uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map. For example, in hash tables, developers store data — perhaps a customer record — in the form of key and value pairs.Hashing is implemented in two steps: An element is converted into an integer by using a hash function. This element can be used as an index to store the original element, which falls into the hash table. The element is stored in the hash table where it can be quickly retrieved using hashed key.The hash function translates the key associated with each datum or record into a hash code, which is used to index the hash table. When an item is to be added to the table, the hash code may index an empty slot (also called a bucket), in which case the item is added to the table there.
What is hashing in simple terms : Hashing is an important concept in cybersecurity as it allows for the safe encryption of data. This guide explains its principles and applications. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security.
How is hashCode generated
Hashcode is a unique code generated by the JVM at time of object creation. It can be used to perform some operation on hashing related algorithms like hashtable, hashmap etc. An object can also be searched with this unique code. Returns: It returns an integer value which represents hashCode value for this Method.
Are all hash codes unique : A hash code (MD5, SHA-1, SHA-256) is of a fixed length, so it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the likelihood of a collision (two distinct files with the same hash value).
HashMap Internal Working
The hash code is used to determine the index in the array where the key-value pair should be stored. The hash code is typically used to compute the remainder of the hash code divided by the size of the array, which ensures that the index is within the bounds of the array.

Hashing algorithms can be used to authenticate data. The writer uses a hash to secure the document when it's complete. The hash works a bit like a seal of approval. A recipient can generate a hash and compare it to the original.
How do hash functions work
A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).This can be accomplished with a quick application of a conditional operator, as seen below. public final class Boolean { private final boolean value; … public int hashCode() { return hashCode(value); } … public static int hashCode(boolean value) { return value 1231 : 1237; } … }One, hashing is a one-way function. It can be used on any input data to generate a hash value. But, applying a hash function to a hash value will not reveal the input data. Second, hashing always produces a fixed-length hash value, irrespective of the length/ size of the input.
Understanding How hashCode() Works
Simply put, hashCode() returns an integer value, generated by a hashing algorithm. Objects that are equal (according to their equals()) must return the same hash code.
How are hash functions generated : A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).
Can two hash codes be equal : If two objects have the same hashcode then they are NOT necessarily equal. Otherwise you will have discovered the perfect hash function. But the opposite is true: if the objects are equal, then they must have the same hashcode .
Is every SHA256 hash unique
Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.

What is a Hashing Algorithm Hashes are the output of a hashing algorithm like MD5 (Message Digest 5) or SHA (Secure Hash Algorithm). These algorithms essentially aim to produce a unique, fixed-length string – the hash value, or “message digest” – for any given piece of data or “message”.Hashing is simply passing some data through a formula that produces a result, called a hash. That hash is usually a string of characters and the hashes generated by a formula are always the same length, regardless of how much data you feed into it. For example, the MD5 formula always produces 32 character-long hashes.
How does hashing work mathematically : What is a Hash Function A hash function is a mathematical function or algorithm that simply takes a variable number of characters (called a ”message”) and converts it into a string with a fixed number of characters (called a hash value or simply, a hash).