Because of the one-way nature of hashing algorithms, the only way to reveal the actual password from a hash is to guess via brute force techniques.Gauging the true security of bcrypt
While it may take time for a bcrypt hash to be created, it is deliberately intended to take time to crack. Cracking them is arduous for any threat actor and sets it apart from hashing algorithms MD5 and SHA-256.Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, NOT encrypted. Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation.
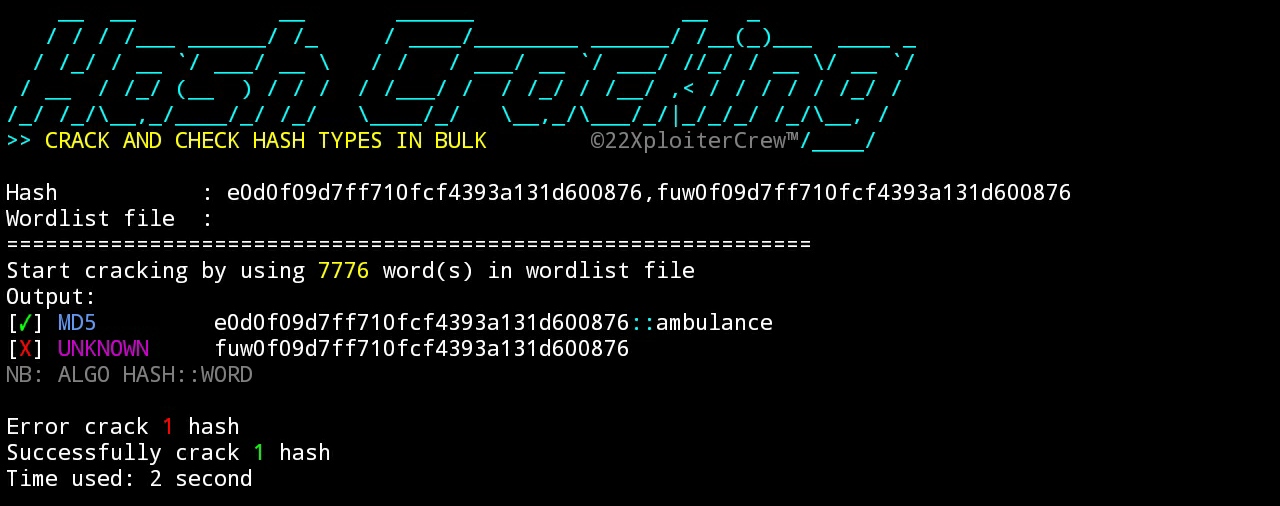
What does a password hash look like : Instead, they just get access to the encrypted unintelligible “hash” created by your password. A common hash function is md5(), which returns a 32-character string from any input. Below are a few examples of what a hash looks like: md5(helloworld) = fc5e038d38a57032085441e7fe7010b0.
Can hashing be broken
Indeed there are some cryptographic hash functions based on number-theoretical problems, such as x2(modN), that can be exponentially broken with a quantum computer. Here, N is the product of two large prime numbers N=p1×p2, and x is a binary representation of the string to be hashed.
Can a hashed password be unhashed : Unlike encrypted data, hashed data cannot be unhashed; the hashing process is irreversible, thanks to the algorithms used.
You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.
Another important detail is that SHA256 hashes don't include the salt element, which makes them more susceptible to dictionary-based cyberattacks. So while SHA256 is more suitable for applications that require frequent interaction, bcrypt is a better solution for safely storing passwords.
How secure is a hash
Password storage: Hash functions are useful for storing passwords in a secure manner. Hashing the password ensures that the original password cannot be recovered from the hash value, making it more difficult for attackers to access user accounts.The hashes start with a $2y$ identifier, this indicates the hash has been created using BCrypt ( $2*$ usually indicates BCrypt). The hashes also indicate they were generated using a somewhat decent work factor of 10.The prefix "$2a$" or "$2b$" (or "$2y$") in a hash string in a shadow password file indicates that hash string is a bcrypt hash in modular crypt format.
Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible. The way hashing works is with a hashing algorithm. This algorithm is most effective when it collision resistant.
Is it possible to decrypt a hash : Hashing is a one-way process that converts a password to ciphertext using hash algorithms. A hashed password cannot be decrypted, but a hacker can try to reverse engineer it.
How hard is it to reverse a hash : As hashing is extremely infeasible to reverse, hashing algorithms are used on passwords.
Can SHA256 hash be reversed
Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
Instead of simply hashing the given password, bcrypt adds a random piece of data, called salt, to create a unique hash that is almost impossible to break with automated guesses during hash dictionary and brute force attacks. Bcrypt also stands out among other hashing algorithms because it uses a cost factor."SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
Can hash be broken : For example, if a dedicated attack finds a collision of a certain hash function with computational complexity of less than 2n/2, it is considered that the hash function has a unique weakness and has been broken.
Antwort How hard is it to crack a hash? Weitere Antworten – Can a hashed password be cracked
Because of the one-way nature of hashing algorithms, the only way to reveal the actual password from a hash is to guess via brute force techniques.Gauging the true security of bcrypt
While it may take time for a bcrypt hash to be created, it is deliberately intended to take time to crack. Cracking them is arduous for any threat actor and sets it apart from hashing algorithms MD5 and SHA-256.Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, NOT encrypted. Because hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation.

What does a password hash look like : Instead, they just get access to the encrypted unintelligible “hash” created by your password. A common hash function is md5(), which returns a 32-character string from any input. Below are a few examples of what a hash looks like: md5(helloworld) = fc5e038d38a57032085441e7fe7010b0.
Can hashing be broken
Indeed there are some cryptographic hash functions based on number-theoretical problems, such as x2(modN), that can be exponentially broken with a quantum computer. Here, N is the product of two large prime numbers N=p1×p2, and x is a binary representation of the string to be hashed.
Can a hashed password be unhashed : Unlike encrypted data, hashed data cannot be unhashed; the hashing process is irreversible, thanks to the algorithms used.
You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.

Another important detail is that SHA256 hashes don't include the salt element, which makes them more susceptible to dictionary-based cyberattacks. So while SHA256 is more suitable for applications that require frequent interaction, bcrypt is a better solution for safely storing passwords.
How secure is a hash
Password storage: Hash functions are useful for storing passwords in a secure manner. Hashing the password ensures that the original password cannot be recovered from the hash value, making it more difficult for attackers to access user accounts.The hashes start with a $2y$ identifier, this indicates the hash has been created using BCrypt ( $2*$ usually indicates BCrypt). The hashes also indicate they were generated using a somewhat decent work factor of 10.The prefix "$2a$" or "$2b$" (or "$2y$") in a hash string in a shadow password file indicates that hash string is a bcrypt hash in modular crypt format.
Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible. The way hashing works is with a hashing algorithm. This algorithm is most effective when it collision resistant.
Is it possible to decrypt a hash : Hashing is a one-way process that converts a password to ciphertext using hash algorithms. A hashed password cannot be decrypted, but a hacker can try to reverse engineer it.
How hard is it to reverse a hash : As hashing is extremely infeasible to reverse, hashing algorithms are used on passwords.
Can SHA256 hash be reversed
Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
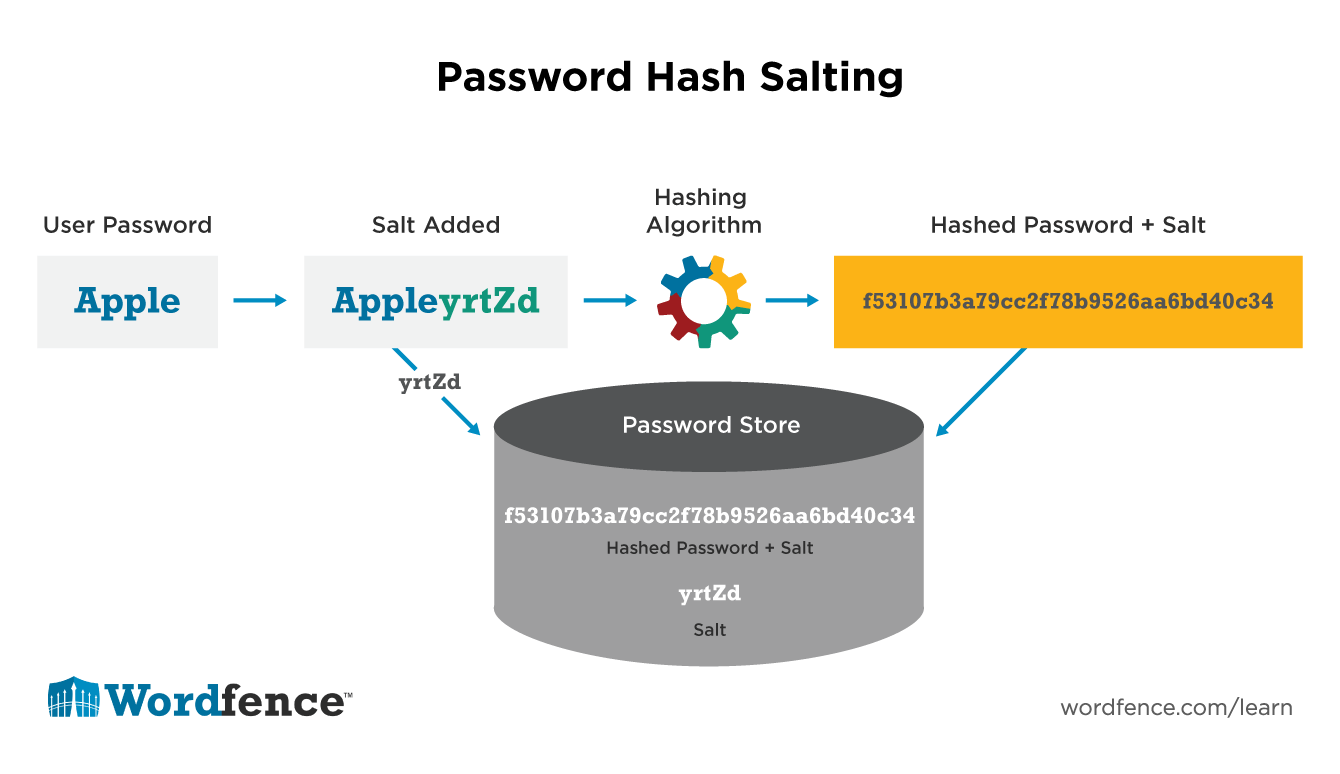
Instead of simply hashing the given password, bcrypt adds a random piece of data, called salt, to create a unique hash that is almost impossible to break with automated guesses during hash dictionary and brute force attacks. Bcrypt also stands out among other hashing algorithms because it uses a cost factor."SHA-2" is the traditional codename for a family of six functions that includes SHA-256 and SHA-512. These functions are considered completely fine and current and non-obsolete.
Can hash be broken : For example, if a dedicated attack finds a collision of a certain hash function with computational complexity of less than 2n/2, it is considered that the hash function has a unique weakness and has been broken.