This can be accomplished with a quick application of a conditional operator, as seen below. public final class Boolean { private final boolean value; … public int hashCode() { return hashCode(value); } … public static int hashCode(boolean value) { return value 1231 : 1237; } … }Example. The hash of string S = “cat” can be calculated as: hash(S) = ('c' – 'a') + ('a' – 'a') * 31 + ('c' – 'a') * 31^2. Here, P = 31 as all the characters are in lowercase, so the count of all distinct lowercase characters is 26, and 31 is the prime number and greater than 26.Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.
What is a hashCode in C# : The GetHashCode method provides a hash code for algorithms that need quick checks of object equality. A hash code is a numeric value that is used to insert and identify an object in a hash-based collection, such as the Dictionary<TKey,TValue> class, the Hashtable class, or a type derived from the DictionaryBase class.
How to generate sha256 code
How to use the SHA-256 hash generator
Type in the text to be hashed in the input box.
Click the "Generate" button.
Get your SHA-256 hash in the output box.
Click on the output box to get copy the code to your clipboard.
How to calculate MD5 : Open a terminal window. Type the following command: md5sum [type file name with extension here] [path of the file] — NOTE: You can also drag the file to the terminal window instead of typing the full path. Hit the Enter key. You'll see the MD5 sum of the file.
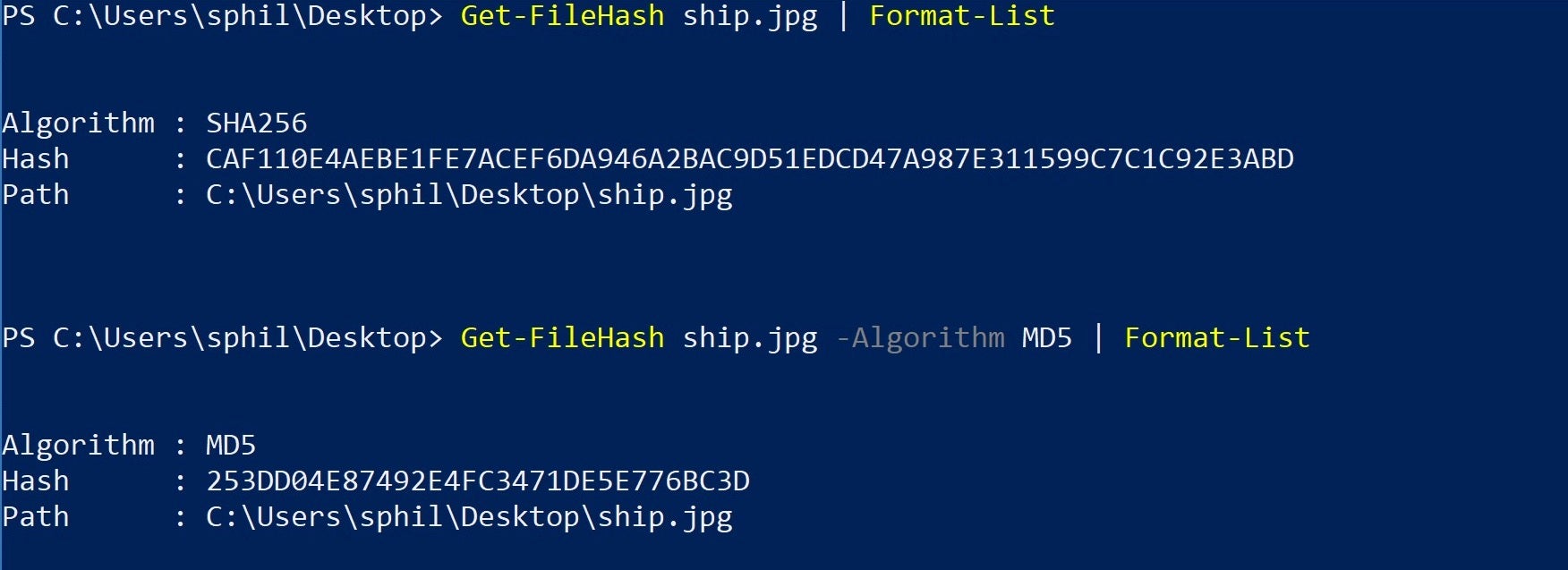
You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
A small utility that allows you to calculate the cryptographic hash value of a string or file… Multiple hashing algorithms are supported including CRC32, MD5, SHA1, SHA256, SHA512 and many other algorithms. This simple application helps you quickly and easily list the hashes of your files.
What is perfect hash code
In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions. In mathematical terms, it is an injective function. Perfect hash functions may be used to implement a lookup table with constant worst-case access time.The first thing to note about the hashCode() method of the Object class is that it returns a 32-bit integer. So the output is allowed to be anything in the range from −231 to 231−1.Hash codes are used to insert and retrieve keyed objects from hash tables efficiently. However, hash codes don't uniquely identify strings. Identical strings have equal hash codes, but the common language runtime can also assign the same hash code to different strings. Using the Code
Mark the object as Serializable() . Mark all variables which should not be serialized as NonSerializable() .
Call the static method MD5HashGenerator. generateKey(Object sourceObject) . You get the MD5 – Hash for the object as a String .
Serialize the object, publish / store it and the hash.
How to get SHA-256 sum : Using Power Shell
Press Windows+R to open the Run box.
Type powershell and click OK.
The Windows PowerShell window will open.
Run the following command: Get-FileHash C:\file\path\my_file.exe -Algorithm SHA256.
Compare the generated value to the checksum of the file in Rublon Downloads.
How many SHA-256 hashes exist : The Benefits of SHA-256
Collisions are incredibly unlikely: There are 2256 possible hash values when using SHA-256, which makes it nearly impossible for two different documents to coincidentally have the exact same hash value.
How to calculate MD5 hash of a string
The md5() function calculates the MD5 hash of a string. The md5() function uses the RSA Data Security, Inc. MD5 Message-Digest Algorithm. Open a terminal window. Type the following command: md5sum [type file name with extension here] [path of the file] — NOTE: You can also drag the file to the terminal window instead of typing the full path. Hit the Enter key. You'll see the MD5 sum of the file.The MD5 hashing algorithm uses a complex mathematical formula to create a hash. It converts data into blocks of specific sizes and manipulates that data a number of times. While this is happening, the algorithm adds a unique value into the calculation and converts the result into a small signature or hash.
Which algorithm is used to calculate the hash : Hashing algorithms are just as abundant as encryption algorithms, but there are a few that are used more often than others. Some common hashing algorithms include MD5, SHA-1, SHA-2, NTLM, and LANMAN. MD5: This is the fifth version of the Message Digest algorithm.
Antwort How do you calculate hash code? Weitere Antworten – How to generate hash code
This can be accomplished with a quick application of a conditional operator, as seen below. public final class Boolean { private final boolean value; … public int hashCode() { return hashCode(value); } … public static int hashCode(boolean value) { return value 1231 : 1237; } … }Example. The hash of string S = “cat” can be calculated as: hash(S) = ('c' – 'a') + ('a' – 'a') * 31 + ('c' – 'a') * 31^2. Here, P = 31 as all the characters are in lowercase, so the count of all distinct lowercase characters is 26, and 31 is the prime number and greater than 26.Hashing means using some function or algorithm to map object data to some representative integer value. This so-called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.
What is a hashCode in C# : The GetHashCode method provides a hash code for algorithms that need quick checks of object equality. A hash code is a numeric value that is used to insert and identify an object in a hash-based collection, such as the Dictionary<TKey,TValue> class, the Hashtable class, or a type derived from the DictionaryBase class.
How to generate sha256 code
How to use the SHA-256 hash generator
How to calculate MD5 : Open a terminal window. Type the following command: md5sum [type file name with extension here] [path of the file] — NOTE: You can also drag the file to the terminal window instead of typing the full path. Hit the Enter key. You'll see the MD5 sum of the file.
You can use Windows Powershell to calculate the SHA-256 checksum for a file.
A small utility that allows you to calculate the cryptographic hash value of a string or file… Multiple hashing algorithms are supported including CRC32, MD5, SHA1, SHA256, SHA512 and many other algorithms. This simple application helps you quickly and easily list the hashes of your files.
What is perfect hash code
In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions. In mathematical terms, it is an injective function. Perfect hash functions may be used to implement a lookup table with constant worst-case access time.The first thing to note about the hashCode() method of the Object class is that it returns a 32-bit integer. So the output is allowed to be anything in the range from −231 to 231−1.Hash codes are used to insert and retrieve keyed objects from hash tables efficiently. However, hash codes don't uniquely identify strings. Identical strings have equal hash codes, but the common language runtime can also assign the same hash code to different strings.
Using the Code
How to get SHA-256 sum : Using Power Shell
How many SHA-256 hashes exist : The Benefits of SHA-256
Collisions are incredibly unlikely: There are 2256 possible hash values when using SHA-256, which makes it nearly impossible for two different documents to coincidentally have the exact same hash value.
How to calculate MD5 hash of a string
The md5() function calculates the MD5 hash of a string. The md5() function uses the RSA Data Security, Inc. MD5 Message-Digest Algorithm.
Open a terminal window. Type the following command: md5sum [type file name with extension here] [path of the file] — NOTE: You can also drag the file to the terminal window instead of typing the full path. Hit the Enter key. You'll see the MD5 sum of the file.The MD5 hashing algorithm uses a complex mathematical formula to create a hash. It converts data into blocks of specific sizes and manipulates that data a number of times. While this is happening, the algorithm adds a unique value into the calculation and converts the result into a small signature or hash.
Which algorithm is used to calculate the hash : Hashing algorithms are just as abundant as encryption algorithms, but there are a few that are used more often than others. Some common hashing algorithms include MD5, SHA-1, SHA-2, NTLM, and LANMAN. MD5: This is the fifth version of the Message Digest algorithm.