Hashing uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map. For example, in hash tables, developers store data — perhaps a customer record — in the form of key and value pairs.The hashCode method in Java is a built-in function used to return an integer hash code representing the value of the object, used with the syntax, int hash = targetString. hashCode(); . It plays a crucial role in data retrieval, especially when dealing with Java collections like HashMap and HashSet.In Java hash function is usually connected to hashCode() method. Precisely, the result of applying a hash function to an Object is a hashcode. Every Java object has a hash code. In general Hash Code is a number calculated by the hashCode() method of the Object class.
How to hash value in Java : hashCode() Method—The hashCode() method belongs to the Java Integer class. It returns the hash value of a given Integer object and overrides the hashcode() method of the Object class. hashCode(int value) Method—This method clearly has a parameter and determines the hashcode of that parameter: value.
Can we decrypt hash code
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
What is the 31 hash code : There is perhaps a couple of reasons for choosing 31. The main reason is that it is a prime number and prime numbers have better distribution results in hashing algorithms, by other words the hashing outputs have less collisions for different inputs.
The hash code for a String object is computed as s [ 0 ] ∗ 31 n − 1 + s [ 1 ] ∗ 31 n − 2 + . . . + s [ n − 1 ] using int arithmetic, where s[i] is the i th character of the string, and n is the length of the string. (The hash value of the empty string is zero.)” The hash value for new Integer(1) is 1; the hash value for String("a") is 97.
How does hashing work
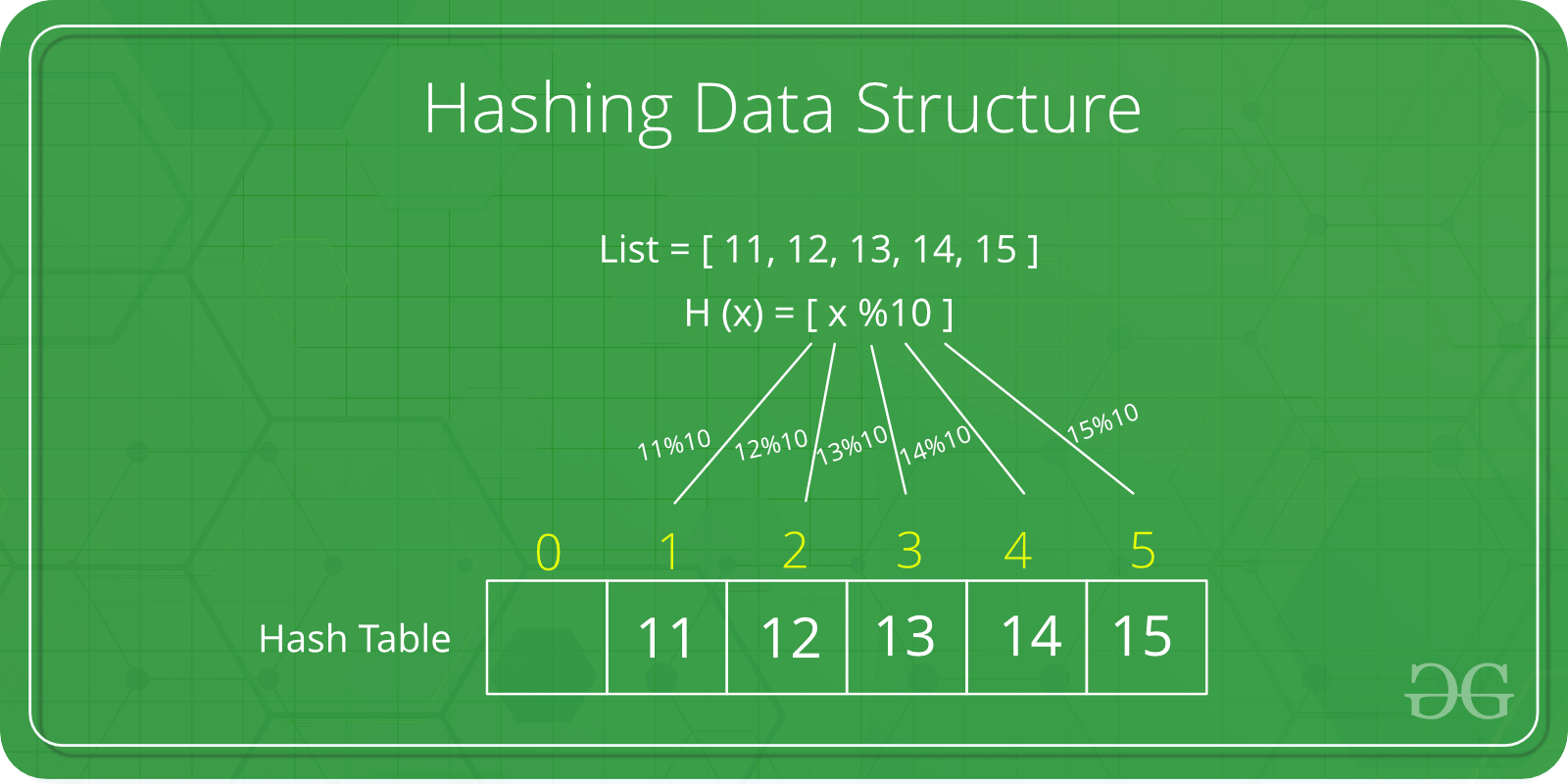
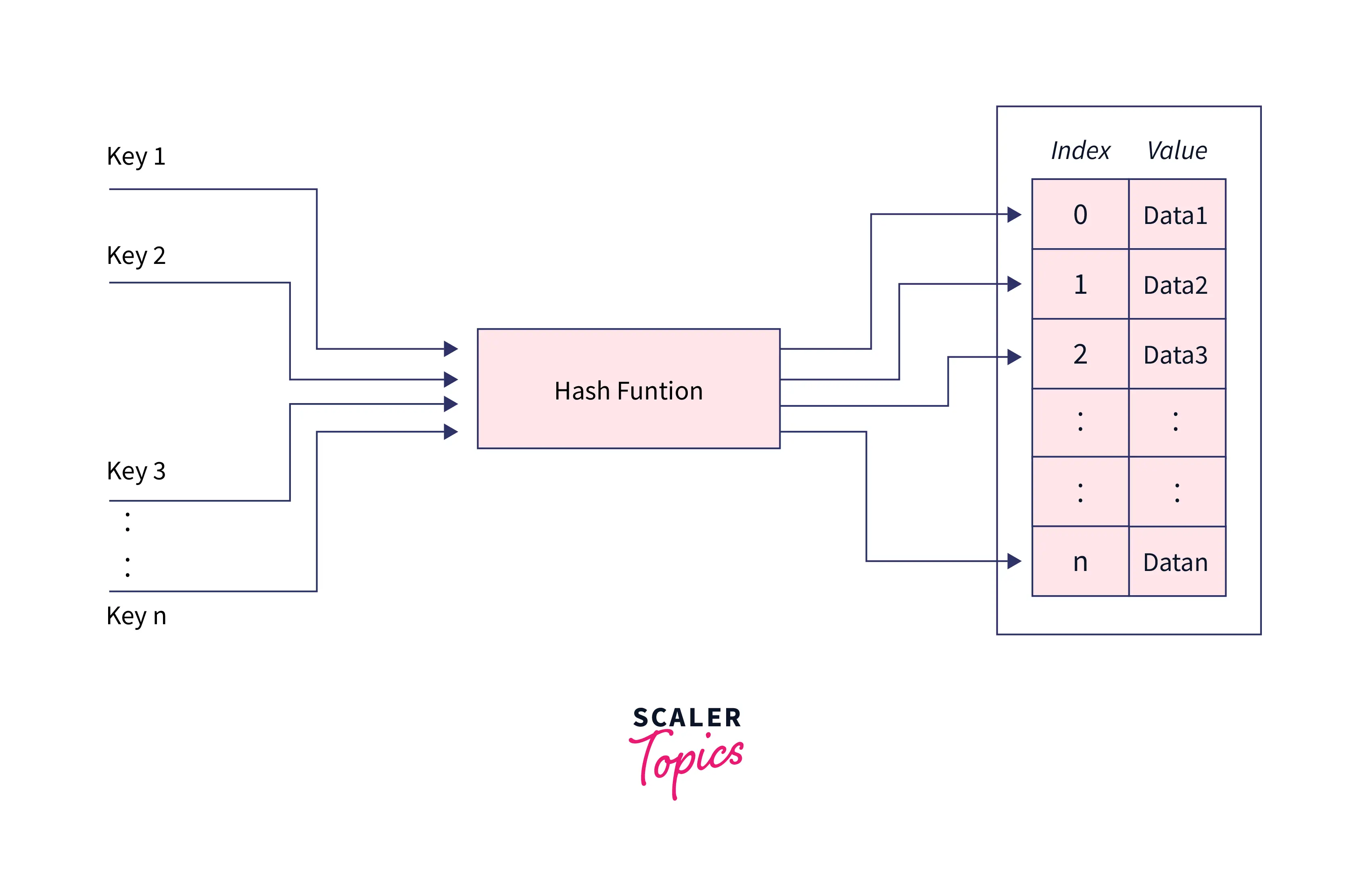
As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.Efficient Retrieval in Hash-Based Collections: Hash-based collections like HashMap , HashSet , and Hashtable use the hashCode() method to efficiently store and retrieve elements. It allows these data structures to quickly locate objects based on their hash code, resulting in faster access times.Hashing in java is a two-step process: firstly, A hash function is used to turn an input key into hash values. This hash-value is used as an index in the hash table and corresponding data is stored at that location in the table. The element is stored in a hash table and can be retrieved quickly using the hashed key. Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.
Is hash a malicious code : Hashing is a common method used to uniquely identify malware. The malicious software is run through a hashing program that produces a unique hash that identifies that malware (a sort of fingerprint).
What is hash 256 code : The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash. With recent computational advancements, it has become possible to decrypt SHA-256 hashes.
What hash starts with $1$
md5-crypt hashes
$1$ is the prefix used to identify md5-crypt hashes, following the Modular Crypt Format. salt is 0-8 characters drawn from the regexp range [./0-9A-Za-z] ; providing a 48-bit salt ( 5pZSV9va in the example). For SHA-256 these are calculated from the first 8 primes. These always remain the same for any message. The primes are firstly square rooted and then taken to the modulus 1. The result is then multiplied by 16⁸ and rounded down to the nearest integer.The phenomenon when two keys have same hash code is called hash collision. If hashCode() method is not implemented properly, there will be higher number of hash collision and map entries will not be properly distributed causing slowness in the get and put operations.
Why is hashCode 0 : If it was zero, it was assumed to have not been calculated. Thus if we have strings with hash code of 0, the caching does not work and the time complexity stays linear, regardless of how often we call hashCode(). In Java 13, they improved the calculation by adding an additional boolean hashIsZero , defaulting to false.
Antwort How do hash codes work? Weitere Antworten – How does hash code work
Hashing uses functions or algorithms to map object data to a representative integer value. A hash can then be used to narrow down searches when locating these items on that object data map. For example, in hash tables, developers store data — perhaps a customer record — in the form of key and value pairs.The hashCode method in Java is a built-in function used to return an integer hash code representing the value of the object, used with the syntax, int hash = targetString. hashCode(); . It plays a crucial role in data retrieval, especially when dealing with Java collections like HashMap and HashSet.In Java hash function is usually connected to hashCode() method. Precisely, the result of applying a hash function to an Object is a hashcode. Every Java object has a hash code. In general Hash Code is a number calculated by the hashCode() method of the Object class.
How to hash value in Java : hashCode() Method—The hashCode() method belongs to the Java Integer class. It returns the hash value of a given Integer object and overrides the hashcode() method of the Object class. hashCode(int value) Method—This method clearly has a parameter and determines the hashcode of that parameter: value.
Can we decrypt hash code
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
What is the 31 hash code : There is perhaps a couple of reasons for choosing 31. The main reason is that it is a prime number and prime numbers have better distribution results in hashing algorithms, by other words the hashing outputs have less collisions for different inputs.
The hash code for a String object is computed as s [ 0 ] ∗ 31 n − 1 + s [ 1 ] ∗ 31 n − 2 + . . . + s [ n − 1 ] using int arithmetic, where s[i] is the i th character of the string, and n is the length of the string. (The hash value of the empty string is zero.)”
The hash value for new Integer(1) is 1; the hash value for String("a") is 97.
How does hashing work
As every file on a computer is, ultimately, just data that can be represented in binary form, a hashing algorithm can take that data and run a complex calculation on it and output a fixed-length string as the result of the calculation. The result is the file's hash value or message digest.Efficient Retrieval in Hash-Based Collections: Hash-based collections like HashMap , HashSet , and Hashtable use the hashCode() method to efficiently store and retrieve elements. It allows these data structures to quickly locate objects based on their hash code, resulting in faster access times.Hashing in java is a two-step process: firstly, A hash function is used to turn an input key into hash values. This hash-value is used as an index in the hash table and corresponding data is stored at that location in the table. The element is stored in a hash table and can be retrieved quickly using the hashed key.
:max_bytes(150000):strip_icc()/hash.asp-final-f341f429ebc1421ab167f2f97609b5eb.png)
Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.
Is hash a malicious code : Hashing is a common method used to uniquely identify malware. The malicious software is run through a hashing program that produces a unique hash that identifies that malware (a sort of fingerprint).
What is hash 256 code : The SHA-256 hash can be used as a secure 64 char password. If the purpose is to compare two raw source files then one can generate the hash and compare them. SHA-256 generates almost unique 32 bit hash. With recent computational advancements, it has become possible to decrypt SHA-256 hashes.
What hash starts with $1$
md5-crypt hashes
$1$ is the prefix used to identify md5-crypt hashes, following the Modular Crypt Format. salt is 0-8 characters drawn from the regexp range [./0-9A-Za-z] ; providing a 48-bit salt ( 5pZSV9va in the example).
For SHA-256 these are calculated from the first 8 primes. These always remain the same for any message. The primes are firstly square rooted and then taken to the modulus 1. The result is then multiplied by 16⁸ and rounded down to the nearest integer.The phenomenon when two keys have same hash code is called hash collision. If hashCode() method is not implemented properly, there will be higher number of hash collision and map entries will not be properly distributed causing slowness in the get and put operations.
Why is hashCode 0 : If it was zero, it was assumed to have not been calculated. Thus if we have strings with hash code of 0, the caching does not work and the time complexity stays linear, regardless of how often we call hashCode(). In Java 13, they improved the calculation by adding an additional boolean hashIsZero , defaulting to false.