On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.Three properties make SHA-256 this secure. First, it is almost impossible to reconstruct the initial data from the hash value. A brute-force attack would need to make 2256 attempts to generate the initial data. Second, having two messages with the same hash value (called a collision) is extremely unlikely.No, SHA256 does not require a key.
Is SHA-256 bad for passwords : SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
Is SHA-256 always unique
Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.
Is SHA-256 used for passwords : One of the most popular SHA-256 uses is password hashing. Instead of storing the actual passwords, companies derive their hash values instead. It's much safer for the user. Every time you enter your password, the system derives a new hash value and checks if it matches with the one stored on the database.
Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken". How to use the SHA-256 hash generator
Type in the text to be hashed in the input box.
Click the "Generate" button.
Get your SHA-256 hash in the output box.
Click on the output box to get copy the code to your clipboard.
Can SHA-256 be hacked
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.If you feed SHA-256 with too little entropy (or even smaller input than 256 bits), the output may appear random, but it is not. For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.
Is SHA-256 breakable : If a classical computer is used, the collision resistance of SHA-256 is broken when the number of steps is reduced to 31, while the original number of steps is 64. However, no attacks were found that would break collision resistance when more than 31 steps were iterated.
Is SHA-256 unbreakable : Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.
How to find SHA-256 key
To generate SHA1 and SHA256 keys in Android Studio,
Open your project in Android Studio.
Click on the Gradle tab located on the right side of the window.
Navigate to your project > Tasks > android.
Double-click on signingReport.
The SHA1 and SHA256 keys will be displayed in the Run tab at the bottom of the window.
The encryption has a key size of 256 bits, which is considered virtually uncrackable—even with the most advanced computing power and algorithms. It is also the same level of security used by banks and other financial institutions to protect sensitive customer information.all SHA-1 hash value will have 160 bits. That is whether you give single character or 100000 character, the output size will be 160 bits only. So SHA-1 don't need key. It is used for Authentication purpose.
How to get SHA-256 key : To generate SHA1 and SHA256 keys in Android Studio,
Open your project in Android Studio.
Click on the Gradle tab located on the right side of the window.
Navigate to your project > Tasks > android.
Double-click on signingReport.
The SHA1 and SHA256 keys will be displayed in the Run tab at the bottom of the window.
Antwort Does SHA-256 need a key? Weitere Antworten – Is SHA-256 still secure
On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible.Three properties make SHA-256 this secure. First, it is almost impossible to reconstruct the initial data from the hash value. A brute-force attack would need to make 2256 attempts to generate the initial data. Second, having two messages with the same hash value (called a collision) is extremely unlikely.No, SHA256 does not require a key.
Is SHA-256 bad for passwords : SHA256 is a very popular hashing algorithm and was and is extremely common in password management. The algorithm itself is considered secure — it is impossible to reverse the encryption, so that's not the issue. People are the issue.
Is SHA-256 always unique
Hashes are not unique. This is easy to prove: a SHA256 hash is only 256 bits long, so if you hash all the possible inputs that are 264 bits long, some of them will have to have the same hash because there aren't enough possible hashes for them to all be different. However, for all practical purposes they are unique.
Is SHA-256 used for passwords : One of the most popular SHA-256 uses is password hashing. Instead of storing the actual passwords, companies derive their hash values instead. It's much safer for the user. Every time you enter your password, the system derives a new hash value and checks if it matches with the one stored on the database.
Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
How to use the SHA-256 hash generator
Can SHA-256 be hacked
SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value. Hashing can also help you fight off a cybersecurity attack.For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.If you feed SHA-256 with too little entropy (or even smaller input than 256 bits), the output may appear random, but it is not.
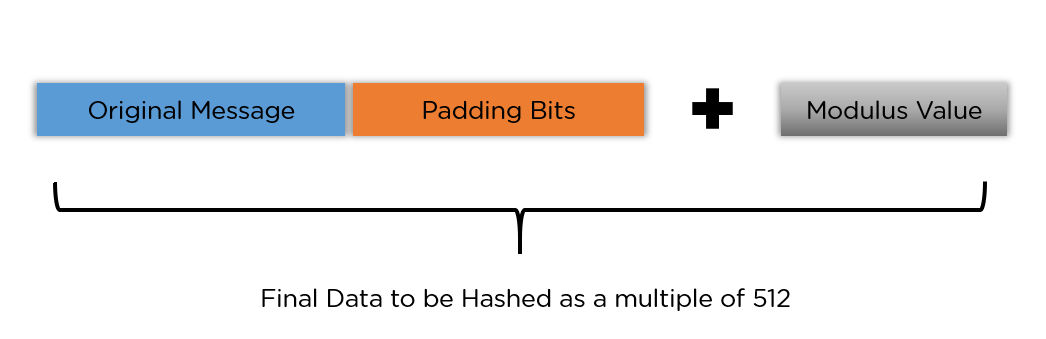
For example, SHA-256 generates a hash value from the content being signed, acting as a unique digital fingerprint. The signer's private key is then used to encrypt the hash value, creating the digital signature.
Is SHA-256 breakable : If a classical computer is used, the collision resistance of SHA-256 is broken when the number of steps is reduced to 31, while the original number of steps is 64. However, no attacks were found that would break collision resistance when more than 31 steps were iterated.
Is SHA-256 unbreakable : Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.
How to find SHA-256 key
To generate SHA1 and SHA256 keys in Android Studio,
The encryption has a key size of 256 bits, which is considered virtually uncrackable—even with the most advanced computing power and algorithms. It is also the same level of security used by banks and other financial institutions to protect sensitive customer information.all SHA-1 hash value will have 160 bits. That is whether you give single character or 100000 character, the output size will be 160 bits only. So SHA-1 don't need key. It is used for Authentication purpose.
How to get SHA-256 key : To generate SHA1 and SHA256 keys in Android Studio,